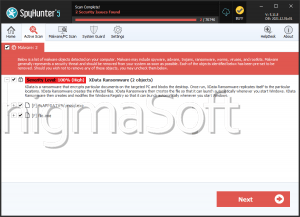
Xda Ransomware
Nowadays, even a person with very little technical skill and experience can create and distribute a file-locking Trojan. This is done by borrowing the code of already established ransomware threats, tweaking it to fit one's needs slightly, and then propagating it. By using Tor services, encrypted email clients, and cryptocurrencies, the cyber crooks manage to keep their anonymity and avoid punishment for their crimes. Recently, malware researchers spotted a brand-new ransomware threat that is being propagated. Its name is the Xda Ransomware, and it appears to belong to the notorious Dharma Ransomware family.
Propagation and Encryption
The exact infection vectors involved in the spreading of the Xda Ransomware are yet to be established. Cybersecurity experts speculate that some of the most commonly used methods may be among the propagation methods used in the Xda Ransomware campaign. These would include spam emails that contain macro-laced attachments, fake application updates, and bogus pirated copies of popular software services. This is why experts warn users against downloading pirated content tirelessly and keep reminding us to be exceptionally careful when receiving emails from unknown sources. The Xda Ransomware will scan the files on the infected host as soon as it manages to penetrate it. Data-locking Trojans like the Xda Ransomware are programmed to target a very wide variety of file types to make sure enough damage is done so that the user contemplates paying the ransom fee. When the scan is through, the Xda Ransomware will trigger its encryption process. Upon encrypting a file, the Xda Ransomware also will change its name by adding a '.id-
The Ransom Note
When the Xda Ransomware is done locking all the targeted files, it will drop its ransom note on the user's desktop. The note's name is 'FILES ENCRYPTED.txt' as the people who propagate ransomware threats often tend to use all caps in naming their ransom notes. This method makes it less likely for their message to be overlooked by the victim. There is no allusion of a specific ransom fee in the attackers' note. However, they provide the user with an email where they expect to be contacted – ‘fullrestore@qq.com.' exceptionally
It is not a good idea to contact the attackers or attempt to negotiate with them. Cybercriminals often lack scruples and will happily take your cash and never provide the decryption key, which they promise. This is why it is way safer to download and install a legitimate anti-spyware application, which will help you remove the Xda Ransomware from your system safely. Next, if you wish, you can try to restore some of the lost files using a third-party data-recovery service, but it is likely that the results will be far from satisfactory.