Are You Sure You’re NOT Infected with Malware?
Don’t Fall Victim to Malware or Ransomware Attacks!
Detect and remove malware, viruses, ransomware & other threats for FREE! Get Protected with SpyHunter.
Download SpyHunter (FREE Trial!)*What Is a Computer Worm?
A computer worm is a type of malware infection designed to deliver a malicious payload to a target machine. Unlike viruses, which require an infected host file to spread, a computer worm is a standalone program that does not need any help or human intervention to travel around, using solely networks like the Internet or a local intranet. Worms can be harmful in many ways as the payloads which they can drop on a computer can have various malicious features. Payloads are typically designed to corrupt important files or steal data. Furthermore, some worms can create a backdoor in host computers and make them accessible for hostile parties, allowing also cyber criminals to turn the network in which the compromised computers are connected into a botnet. Botnets can, later on, be used for performing DDoS attacks and spreading other kinds of malware. Yet, even without a malicious payload on board, a worm is considered a threat. Its ability to replicate itself indefinitely could make computers and web servers crash due to resources overload. Therefore, a worm should be removed from the infected system immediately. Over the past several years, worms have typically taken the third place among other types of malware infections, following Trojans and traditional viruses, which shows that they continue to be a significant threat for the cyber security.
 Image – Computer Worms Explanation – Source: Slideplayer.com
Image – Computer Worms Explanation – Source: Slideplayer.com
The latest example of a massive cyber attack using a computer worm happened just a couple of months ago. Called “Olympic Destroyer”, the new worm appeared in February 2018 with the purpose of disrupting the opening ceremony of the Olympic games in Pyeongchang. The malware was supposed to have had a political goal as well. Its authors obviously attempted to prevent the expected warming of the relationship between South and North Korea by attributing falsely the attack to a notorious, nation-state backed, North Korean hacking group known as Lazarus. Olympic Destroyer was successful in shutting down the WiFi connection during the Olympic Games opening ceremony, and it also prevented the event’s broadcast by knocking off the television screens that were supposed to display the ceremony.
According to researchers, the Olympic Destroyer was created to infect computers within the entire network of Pyeongchang as it also impacted the official website of the games, where it blocked the printing of tickets and the display of event results. Several South Korean ski resorts were affected by the hack as well as the operation of some ski lifts and ski gates had been distorted. Once the researchers dismantled the malware’s creator’s attempt to put Lazarus’ fingerprints on the malware code, numerous speculations concerning the true origin of attack emerged, particularly involving famous cyber-espionage groups from Russia, China, and Iran. Yet, for now the truth remains uncovered.
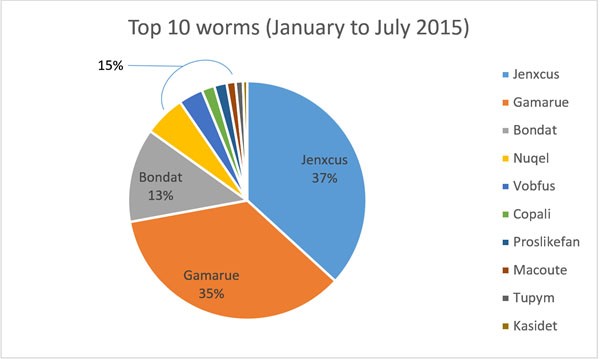 Image: Top 10 Computer Worms – Source: Microsoft.com
Image: Top 10 Computer Worms – Source: Microsoft.com
Worm Distribution Methods and Stealth Techniques
Most infections, including computer worms, exploit vulnerabilities in software or hardware to penetrate targeted machines. Mostly attacked are systems running Windows OS because its popularity and wide use guarantee that the attackers will compromise a significantly large number of devices. However,flaws that PC users do not patch in a timely fashion by installing the latest available updates also contribute to the vast spread of malware infections. Common distribution methods of a computer worm might be:
After gaining unauthorized access to the target machine , a computer worm wastes no time and quickly does the following:
First Appearances of Computer Worms
The first reported cases of computer worms date back to the early 1970s. The Creeper is considered the first worm and it appeared in 1971, created by Robert H. Thomas at BBN Technologies. Creeper did not require physical mediums to spread around over the earliest version of ARPANET — the precursor of the modern Internet as we know it today. The program was quite sophisticated for its time and, as its creator claims, did not have any malicious intentions. Running on the TENEX operating system, the Creeper application was intended to provide a convenient way for transferring programs to other computers with the purpose of finding the most efficient machine for a particular task. Yet, the self-replicating code of the Creeper caused trouble, more serious than just displaying the mocking message: “I am the Creeper: Catch me if you can.” The worm clogged compromised systems by replicating itself repeatedly, distorting thus the performance of the infected computers and even crushing them down completely.
The Morris was the next famous computer worm to come around. It was the first worm to get significant media attention at the end of the past century as it resulted in the first felony conviction in the US under the Computer Fraud and Abuse Act. It was also the first worm for which it is known to have had malicious content, although it had not been created with the intention to cause any trouble. Supposedly, its author, a 23-year old college student, wrote the program with the intention to gauge the size of the Internet at that time, however, a critical error in the spreading mechanism turned the code into a virulent weapon for denial of service attacks.
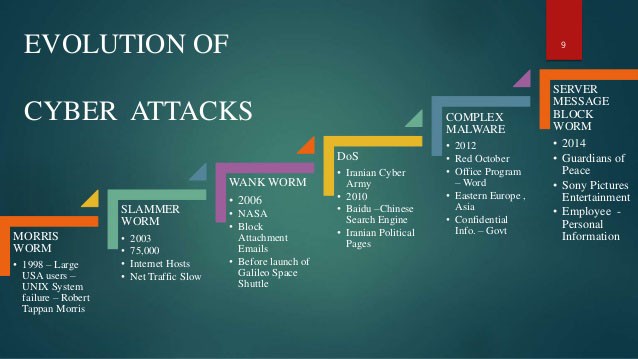 Image: Evolution of Cyber Threats – Source: slidesharecdn.com)
Image: Evolution of Cyber Threats – Source: slidesharecdn.com)
The Morris worm exploited weak passwords, as well as vulnerabilities in the UNIX sendmail command. In particular, the worm exploited a buffer overflow vulnerability in the BSD variant of UNIX, a flaw that still pops up in some contemporary software. Exploits based on this type of bug work by setting up a container for information called buffer where the developer can store data. The problem occurs when the stored data is larger than the space available within the buffer, and that is when the buffer starts to overflow, causing unpredictable behavior of the operating system, which may include granting unauthorized access to the affected machine. Once the Morris worm penetrated a host computer, it started executing its instructions which consisted of installing itself on that computer, and then trying to infects as many other computers as possible. Thus, the malware scanned the network for new hosts to propagate itself to, whereby it copied its code even on systems on which the worm was already running, taking the spreading of the malware completely out of control and resulting in numerous copies of the program running simultaneously on one and the same machine. New instances of the worm on each host launched additional processes of reproducing the worm code, each of these processes slowing down the system and, eventually, making it crash down completely.
The Morris worm became the precursor of some of the most destructive modern malware threats, some of which still exploit buffer overflows and other well-known vulnerabilities. Unfortunately, not all software developers pay enough attention to security when building new programs, or revising old software, which makes it preferable for users to install a reliable anti-malware program.
The Most Destructive Worms of All Times
Many highly destructive computer worms have spread across the Internet since the Creeper and the Morris worms, yet only several of them have imposed billion dollar damages. Some of the first mass destruction worms employed social engineering techniques to infect target machines. In the beginning of the 21st century, ILOVEYOU was let loose on the Internet, and quickly became the most damaging malware of all time. It represented a visual basic script that spread through email messages with a subject line saying “I love you.” Then, the user only needed to open the attached text file to get his or her entire system files overwritten and, basically, destroyed. What made the malware spread like wildfire was its ability to send a copy of itself to all contacts stored in the victim’s Microsoft Outlook account.
A few years later, My Doom appeared, and it topped the record dollar cost of all previous malware attacks seen before as it hit major technology companies like Google and Microsoft with Distributed Denial of Service (DDOS) attacks. Total costs caused by My Doom have been estimated at $38 billion. It was distributed through a “Sending Failed” message from the mail server which contained an attachment laced with the malicious code. The user was supposed to click on the attachment in order to re-send the mail, however, opening the infected file resulted in the installation of the worm. My Doom then sent a copy of itself to all contacts in the user’s address book, as well as to Peer — to — Peer shared devices.
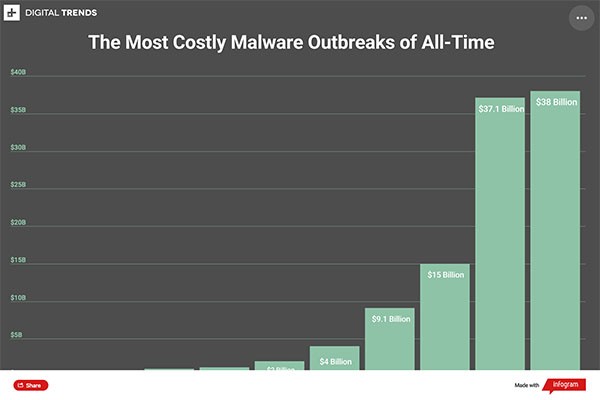 Image of Most Costly Malware Outbreaks – Source: digitaltrends.com
Image of Most Costly Malware Outbreaks – Source: digitaltrends.com
Other examples of successful worms from the beginning of the century include Code Red, Nimda, Jerusalem, Storm Worm, MSBlast (The Blaster Worm). Code Red attacked computers running Microsoft IIS web server in the summer of 2001. Named after the drink that the researchers were having at the time of the discovery, the worm spread by exploiting the good old buffer overflow-type of vulnerability while its payload defaced the infected website to display the message: “HELLO! Welcome to hxxp://www(dot)worm(dot)com! Hacked by Chinese”! Code Red demonstrated a brand new propagandation technique — the malware did not rely on sending copies of itself to the victim’s mailing contacts; instead, it scanned the network to find connected IP addresses and used these as vectors of distribution. Nimda was another worm that appeared in September the same year and its name came from the backward spelling of the word “admin”. It was both a computer worm and a file infector. Its release coincidently collided with the 11/9 World Trade Center attacks, leaving many to speculate about a possible connection between the two events, a claim later found ungrounded. Nimda eclipsed neighbor Code Red and similar outbreaks due the multiple propagation vectors it used, helping it spread quickly and making it the Internet’s most widely spread infection within 22 minutes. Nimda attacked IIS Web servers and network computers running Windows 2000, Pro, NT, 98, and 95. The Blaster worm (also known as MSBlast, Lovesan, or Lovsan) attacked systems running Windows XP and 2000, also exploiting a buffer overflow vulnerability. It did not require the user to open any attachment, but simply spammed itself to random IP addresses until it managed to enter a big network of a company or a university. It was designed to start a SYN flood attack against port 80 of windowsupdate.com and create DDoS attacks against the site, whereby there was a particular rule related to the attacked system’s date and month.
Probably the most prominent example of a more recent worm infection is the Stuxnet worm. Stuxnet was created in 2006 when US military and intelligence forces started working together with Israel on a top-secret cyberwar program named “Olympic Games”. The program had the purpose of delaying, or stopping completely, Iran’s nuclear weapon production, whereby the idea was to create the most sophisticated computer worm that the world had seen by then. Until the beginning of 2010, the worm had managed to crash 20% of Iran’s functioning centrifuges for uranium enrichment, setting back the country’s nuclear program with 2 years. It did not take long, however, before the infection leaked out and copies of the worm began spreading all over the Internet, infecting 130,000 computers worldwide. It was also in 2010 when the worm was discovered by researchers after it started affecting machines outside of the initial target range.
The worm spread on Windows operating systems and targeted industrial control systems (ICS) made by Siemens, whereby Stuxnet is considered the first malware of that type capable of spying on and destroying such systems. Also, it was the first malware that was able to change the modifications of Programmable Logic ControlLers (PLCs) of infrastructure facilities like power plants, gas lines, water treatment facilities and so on. In order to be able to reach these highly secured systems, Stuxnet incorporated sophisticated propagation techniques which allowed it to infect target files without using the Internet or any other network. Stuxnet was able to spread across Windows computers by copying itself from a Windows computer to a USB stick. However, PLCs are not based on Windows, therefore the worm needed to find another way to infect the target machines: it scanned Windows systems in order to find those that manage the PLCs, and dropped its payload on them. In order to alter the PLCs settings, the malware then sought out and infected the so called STEP 7 project files which are the files used by Siemens to program the PLCs. Once the malware had identified the specific PLC model, it gained complete control over all data flowing in and out of the infected PLC.
In the following two years, Stuxnet continued to exist, and even became the framework for the development of other pieces of malware. Parts of the Stuxnet source code have been discovered in the cyber spying program the Flame, while the Duqu worm, which was also created to disrupt the nuclear weapons production, also shows striking similarities. Unlike Stuxnet though, Duqu does not replicate itself and does not have a payload. Instead, it uses Trojans to gather sensitive information and it can set up remote access as well.
Not all pieces of malware want to alert their victims they’ve arrived, so without a scan alert, or the keen eye of a computer security expert, you may not be aware you are being hacked. In the absence of a stealth scan alert, below are some subtle signs of a worm intrusion of some sort:
If you suspect that a malicious program or tool has somehow managed to penetrate your system, there are several steps that you can undertake. First of all, it is very important to make sure that your computer’s operating system is up-to-date, and that you have downloaded and installed the latest versions of all your applications. Whenever a new cyber threat is discovered, software developers try to fix the vulnerabilities which have allowed the particular malware to operate, and to push updates with patches to end-users as soon as possible. If you have an antivirus program installed on your computer, you should also check whether is has the latest malware definitions since that is the only way it can protect you efficiently. Then, run a scan with your antivirus malware to find out if there are any suspicious elements in your computer. In case the scan detects a computer worm, you can safely use its functions to remove the detected malware and clean infected files. You may need to disconnect your computer from the Internet, as well as from any other networks, in order to prevent the worm from spreading to other devices connected to those networks. In this case, you will need an uninfected computer to download and install any necessary programs and updates, and then transfer them to the compromised computer using an external storage device.
The Code Red worm was a computer worm observed on the Internet on July 13, 2001. It attacked computers running Microsoft’s IIS web server. The payload of the worm included defacing the affected web site to display: HELLO! Welcome to hxxp://www.worm.com! Hacked By Chinese! This message became a meme to indicate an online defeat.
The Blaster Worm (also known as Lovsan, Lovesan or MSBlast) was observed during August 2003 and spread on computers running Windows XP and Windows 2000. The worm exploited a buffer overflow, which allowed the infection to spread without users opening attachments simply by spamming itself to large numbers of random IP addresses. The worm was programmed to start a SYN flood against port 80 of windowsupdate.com, thereby creating a distributed denial of service attack (DDoS) against the site. The damage to Microsoft was minimal as the site targeted was windowsupdate.com instead of windowsupdate.microsoft.com to which it was redirected. Microsoft temporarily shut down the targeted site to minimize potential effects from the worm.
Nimda (spelled backwards ‘admin’) is both computer worm and file infector. Its release coincidently collided with the 911 World Trace Attacks leaving many to speculate it was connected, a claim later unfounded. Nimda eclipsed neighbor Code Red and similar outbreaks due the multiple propagation vectors it used, helping it spread quickly and making it the Internet’s most widely spread infection within 22 minutes. Nimda attacked IIS Web servers and network computers running Windows 2000, Pro, NT, 98, and 95.
ILoveYou, also known as the Love Bug Worm, had persons clicking on its infectious email attachment, which automatically sent a copy of the worm to everyone in the victim’s email address contact list, to the tune of 10 million computers.
Not all viruses want to alert their victims they’ve arrived, so without a scan alert, or the keen eye of a computer security expert, you may not be aware you are being violated. Absent a stealth scan alert, below are subtle signs of a worm intrusion:
| # | Threat Name |
Severity Level
Severity Level: The determined severity level of an object, represented
numerically, based on our risk modeling process and research, as explained in our
Threat Assessment Criteria.
|
Alias(es) |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|---|
| 1. | W32.StuxnetQKY.Trojan | 10 % (Normal) | ||
| 2. | Worm.Banwarum | 90 % (High) | 11 | |
| 3. | Worm.Fbound | 90 % (High) | 3 | |
| 4. | Worm.Slenfbot.AKC | 50 % (Medium) |
Logger.OJW Monitor/Win32.KeyLogger.gen SPR/KeyLogger.ama |
96 |
| 5. | Worm.Klez | 50 % (Medium) | 41 | |
| 6. | IM-Worm.Win32.Sohanad.qi | 50 % (Medium) | ||
| 7. | Worm.AutoIt.Lisisor.A | 50 % (Medium) |
Trj/CI.A W32/Dx.UDD!tr IM-Worm.Win32.Sohanad |
|
| 8. | Email-Worm.Win32.Zhelatin.ml | 90 % (High) | ||
| 9. | W32.Micharo | |||
| 10. | Worm.Feebs | 90 % (High) | ||
| 11. | Net-Worm.Kido!sd6 | 50 % (Medium) |
W32/Conficker.FZ!worm.im Trojan.Win32.Genome Worm/Win32.Conficker |
570 |
| 12. | Worm.Deborm | 90 % (High) | 3,803 | |
| 13. | Worm.Wenper | 50 % (Medium) | 4 | |
| 14. | Worm.MSIL.Winupkiy.A | 50 % (Medium) |
Dropper.Generic7.IHO W32/Dapato.BYDD!tr Dropper/Win32.Dapato |
17 |
| 15. | Worm.MSIL.Wokswid.A | 50 % (Medium) |
Trojan.SuspectCRC TR/ATRAPS.Gen Trojan.Generic.6701628 |
|
| 16. | Worm.Slenfbot.AKU | 50 % (Medium) |
Worm.Win32.Dorkbot Win32/Dorkbot.worm.233472 Generic.grp!ec |
|
| 17. | Email-Worm.Win32.Bagle.fk | |||
| 18. | W32.Fubalca.E | |||
| 19. | Worm/Autorun.bkjm | |||
| 20. | Honditost | |||
| 21. | Worm.Win32.VB.bem | |||
| 22. | Worm.Cambot.A | 50 % (Medium) |
Trojan/Win32.Jorik HackTool/Win32.Kiser.gen Generic.dx!bbj4 |
1,522 |
| 23. | WORM_EBOOM.AC | 20 % (Normal) | ||
| 24. | Worm:Win32/Dorpiex.A | |||
| 25. | IM-Worm.Win32.VB.bn | |||
| 26. | Email-Worm.Warezov!sd5 | |||
| 27. | Worm.Burnwoo.A | 90 % (High) |
Generic5.PPL.dropper Worm/Win32.Agent.gen Worm.Win32.Agent.NBR |
29 |
| 28. | Worm.Vobfus.F | 50 % (Medium) |
W32/Autorun.JND Worm/AutoRun.HV W32/VBNA.IXO!worm |
|
| 29. | Conficker.C | 50 % (Medium) |
W32/Conficker.FZ!worm.im Trojan.Win32.Genome Worm/Win32.Conficker |
570 |
| 30. | W32.SillyFDC.BAZ |
Last updated: 2026-02-08
| Threat Name |
Severity Level
Severity Level: The determined severity level of an object, represented
numerically, based on our risk modeling process and research, as explained in our
Threat Assessment Criteria.
|
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 'U.Z.A. Operating System' Wallpaper | ||
| ACAD/Medre.A | 50 % (Medium) | 0 |
| ALS.Kenilfe!inf | ||
| Artemis!DD51CDCC10D0 | ||
| Autoit.Obfus | 100 % (High) | 3 |
| AutoIt/Renocide | 50 % (Medium) | 0 |
| AutoRun.AEC | 90 % (High) | 0 |
| Av.exe | ||
| Backdoor.Agobot.lo | 80 % (High) | 0 |
| Backdoor.Agobot.s | 80 % (High) | 0 |
| Backdoor.Agobot.wk | 80 % (High) | 0 |
| Backdoor.Agobot.y | 80 % (High) | 1 |
| Backdoor.Poebot.AL | 80 % (High) | 16 |
| Backdoor.Rinbot.A | 80 % (High) | 0 |
| Backdoor.SpyBoter | ||
| BD.Raptra | ||
| Bizex | ||
| Blackout | ||
| Bloodhound | 90 % (High) | 2 |
| Bloodhound.W32.1 | 90 % (High) | 77 |
| Bofra.A | 90 % (High) | 0 |
| BOO/Whistler.A | 50 % (Medium) | 10 |
| Brambul | ||
| BrowserModifier.SearchV | 20 % (Normal) | 1 |
| Cetus Malware |