XData Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 2 |
| First Seen: | May 21, 2017 |
| OS(es) Affected: | Windows |
In the aftermath of the WannaCry ransomware infection, PC security researchers have received reports of a new widespread attack involving the XData Ransomware, a similar ransomware Trojan that is being used to carry out numerous ransomware attacks in Ukraine currently. Hundreds of computers were infected in Ukraine within the span of only 24 hours on May 19, 2017. The XData Ransomware carries out a typical ransomware attack, encrypting the victims' files to demand the payment of a ransom from the victim. It is crucial to take steps to protect computers from ransomware Trojans like this one, especially as the XData Ransomware attacks start spreading beyond the Ukraine's borders. More than 90% of all victims of the XData Ransomware are active in Ukraine currently, but new victims have started appearing in the Baltic region, Germany and Russia.
Table of Contents
The XData Ransomware is Among the Most Active Threats Currently
The XData Ransomware attack is on a rampage in Ukraine currently, claiming four times more victims in this country than the total reported for an entire week for the WannaCry Ransomware, which has the capacity to spread on its own. Ukraine was ranked fifth in the list of countries most affected by the WannaCry outbreak. Currently, the XData Ransomware is the second most active ransomware Trojan according to current daily statistics, only behind the Cerber ransomware family, that is clearly the most widespread ransomware variant.
Currently it is not known how the XData Ransomware is spreading to victims. The following file processes have been associated with the XData Ransomware attack, which may help PC security researchers identify the XData Ransomware variants or threats related to this ransomware family:
- mssql.exe
- msdns.exe
- msdcom.exe
- mscomrpc.exe
How the XData Ransomware Carries out Its Attack
The XData Ransomware uses the AES encryption to make the victims' files unusable. This is a strategy typical of most ransomware Trojans. The files affected in the XData Ransomware attack will have the file extension '.~xdata~' included at the end of each file's name, making it simple to know which files have been compromised at any given time in the XData Ransomware attack. The XData Ransomware will encrypt the files contained on network drives and external memory devices connected to the infected computer, as well as the files contained on the victim's main drives. After encrypting victims' files, the XData Ransomware will drop its ransom note on the victim's computer in the form of a text file named 'HOW_CAN_I_DECRYPT_MY_FILES.txt.' Below is the full text of the ransom note displayed in the XData Ransomware attack:
'Your IMPORTANT FILES WERE ENCRYPTED on this computer: documents, databases, photos, videos, etc.
Encryption was prodused using unique public key for this computer.
To decrypt files, you need to obtain private key and special tool.
To retrieve the private key and tool find your pc key file with '.key.~xdata~' extension.
Depending on your operation system version and personal settings, you can find it in:
'C:/',
'C:/ProgramData',
'C:/Documents and Settings/All Users/Application Data',
'Your Desktop'
folders (eg. 'C:/PC-TTT54M#45CD.key.~xdata~').
Then send it to one of following email addresses:
begins@colocasia.org
bilbo@colocasia.org
frodo@colocasia.org
trevor@thwonderfulday.com
bob@thwonderfulday.com
bil@thwonderfulday.com
Your ID: [PC-NAME]#[VICTIM_ID]
Do not worry if you did not find key file, anyway contact for support.'
Dealing with the XData Ransomware
Unfortunately, as soon as the files have been encrypted in the XData Ransomware attack, it becomes impossible to restore the files without paying the ransom. Because of this, it is imperative that computer users take steps to back up all files on an external memory device or the cloud. Having a trustworthy backup system can make you invulnerable to the XData Ransomware and other ransomware attacks completely. This is because the ability to restore files from a backup removes any leverage the extortionists have that allows them to demand a ransom payment. Apart from file backups, PC security researchers recommend the use of a reliable, fully updated anti-malware application.
SpyHunter Detects & Remove XData Ransomware
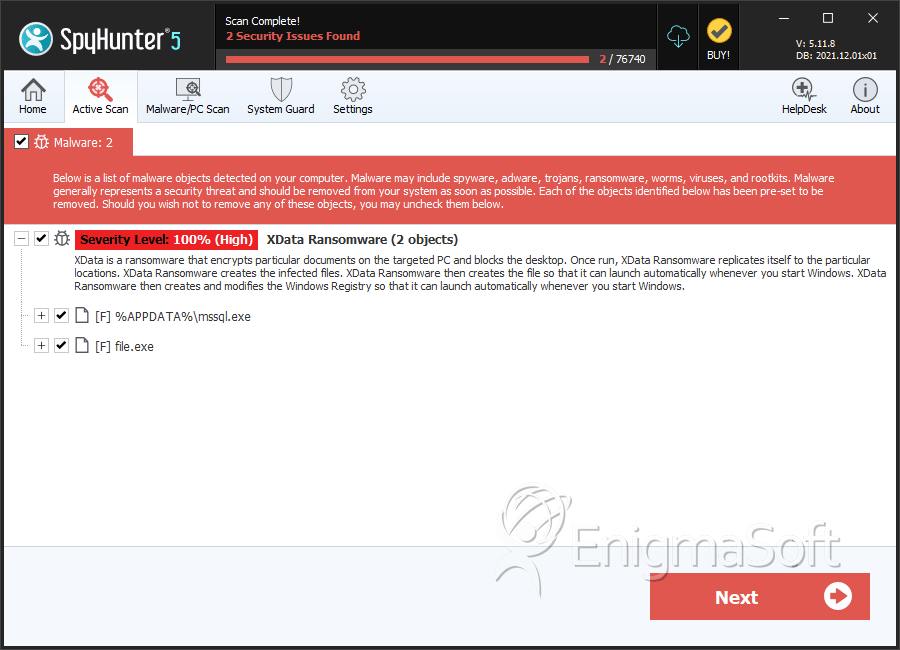
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | mssql.exe | a0a7022caa8bd8761d6722fe3172c0af | 2 |
| 2. | file.exe | c6a2fb56239614924e2ab3341b1fbba5 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.