Are You Sure You’re NOT Infected with Malware?
Don’t Fall Victim to Malware or Ransomware Attacks!
Detect and remove malware, viruses, ransomware & other threats for FREE! Get Protected with SpyHunter.
Download SpyHunter (FREE Trial!)*A banking trojan is a type of trojan infection that comes with a specific function. Just like any other trojan out there, it pretends to be something it is not in order to get into the target system. However, as its name says, it mostly targets financial institutions to steal important credentials and make easy money.
The core of a banking trojan does not differ much from a regular trojan infection. At the end of the day, it is there to steal information behind its owner’s back. Hence, once installed, these programs set out to create botnets, steal sensitive credentials and money, as well as inject malicious codes into browsers, and so on. However, banking trojans are unique in the way that there are banking trojan families, and each family has its signature moves.
The origins of online banking date back to the 1980s, but it was not until the year 2000 that online banking actually took off as an important part of banking services. Likewise, when something gains momentum, there will always be parties that want to exploit it. Thus, it did not take long for cybercriminals to target online banking services.
At first, their main targets were the banks and their cyber systems. However, banks were quick to invest in cybersecurity measures that made it harder for hackers to take them down from within. Consequently, the attack vector shifted from institutions to their customers. It is a lot easier to trick an unsuspecting user into downloading and installing a trojan infection than to penetrate a corporate security system.
It is also important to note that these days, banking trojans do not just target financial institutions. They also aim to attack digital analytic firms, tech companies, social media and communication platforms, and other online entities that might give them direct access to a vulnerable customer. Aside from that, banking trojans still use the most common methods of distribution that involve spam, malicious advertising, phishing, and drive-by downloads.
With that covered, let us look at the most prominent banking trojan families to give you a better idea of what they are and how they work.
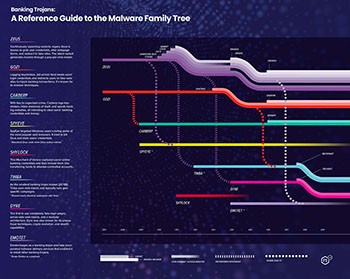
The Banking Trojan Family Tree Reference Guide – Source: F5.com (click for larger image)
Let us start from the very beginning and deal with probably the most well-known banking trojan out there. Zeus or Zbot is arguably the most widespread banking trojan that first appeared in 2007. It was first supposed to steal user credentials, but over time it evolved into a malware program that could change webpage forms and redirect users to malware-related pages. It is believed that Zeus Trojan was developed by a Russian hacker who, later on, sold the program’s code to the SpyEye Trojan developers. All in all, its code has been public since 2011, and it led to the development of other prominent banking trojans.
The original version of Zeus Trojan was supposed to work on the Microsoft operating systems, and it would usually reach its victims via spam or drive-by downloads. Although the original infection has been successfully taken care of by antimalware applications, there are still Zeus spin-offs out there that can still cause trouble (e.g., programs like Atmos, Citadel, Gameover).
Our next banking trojan on the list is Gozi. It was also first detected in 2007, and its signature move was to trick users into completing financial transactions into malware-related accounts. Gozi is considered to be one of the original banking trojans, and codes of its different versions were subsequently leaked in 2010 and 2015. According to the researchers at F5, its original developer from Latvia was arrested, but it did not stop this malware from spreading. Gozi continues to target financial institutions and works hand-in-hand with a few other banking trojans. For example, in 2019, Gozi was known to work along with DanaBot trojan.
The year 2009 saw the emergence of two prominent banking trojan families: Carberp and SpyEye. Carberp is known to log keystrokes and spoof websites. Although its original creator was arrested in Russia in 2012, the malware made a comeback in 2013, and it still continues to evolve. The threat level from this infection depends on who uses it. For example, for years, Carberp was associated with the Carbanak gang until the gang was arrested in 2018. Although the infection has not been making great rounds since then, it is still active, mostly targeting banks in Armenia, Malaysia, and Russia.
Now, SpyEye also logs keystrokes and employs form grabbing to steal data. It mostly targets devices that run on the Windows operating systems and use the most common web browsers. As mentioned, this toolkit was fused with Zeus Trojan in 2010, and between 2010 and 2012, these two infections together cause over $1bn damage. Finally, its distributor was sentenced in 2016.
While most of the other banking trojans seem to follow the general rules of malware activities and distribution, ShyLock was a peculiar type of infection. It was first detected in 2011, and it also captured user credentials in order to fool them into transferring their money to cybercriminal-controlled accounts. ShyLock was very adaptable, and it could quickly respond to security countermeasures imposed by financial institutions. The malware campaign was run like an actual business with real work hours, and it was privately owned. ShyLock remained active until 2014, mainly targeting UK and US banking institutions. Its code was never sold to other hackers, and when the gang operating this campaign was arrested in 2014, ShyLock’s servers were shut down.
Coming up next, we have Tinba that appeared in 2012. It is interesting because it is the smallest banking trojan to date. The main file is only 20KB in size, and this infection has been known to operate geography-specific attacks, having first appeared in Turkey. Its code was leaked in 2014, and it is supposedly a modified version of Zeus trojan. Researchers also suggest that it has almost identical web injects with the Gozi infection, which shows that both programs were probably acquired by the same cybercrime actor. Tinba is no longer making waves, but it is possible that it is not gone for good.
Another supposed (but unconfirmed) variant of Zeus popped up in 2014. It was called Dyre, and it targeted the US-based banks. According to a report in 2015, Dyre was the first banking trojan to employ 100% fake login pages, modular architecture, and server-side web injects. What’s more, it broadened its target scope as well, attacking not only online banking services but also software-as-a-service (SaaS) companies. The gang that was responsible for the Dyre campaign was arrested by the Russian law enforcement authorities in 2016.
An example of a classic banking trojan that has resurfaced in 2020 is Emotet. This infection first appeared as a simple banking trojan in 2014. However, later on, it developed into a complex program that also provided malware delivery services. For instance, in 2017, Emotet “worked” together with the Dridex banking trojan, where Emotet delivered it as an additional payload. Also, in 2018 Emotet infamously exploited the EnernalBlue Windows vulnerability that was also used by the notorious WannaCry Ransomware. The vulnerability has been patched by now, and Emotet reemerges time and again instead of running continuously. It usually focuses on geographically centered attacks and continues to evolve. To find out more about the latest Emotet wave, check out our detailed entry here.
Banking trojans clearly do not remain the same. If we were to give you an example of a new type of banking trojan, we could point out Backswap. It has been a while since this trojan first appeared in March 2018, but it still stands out as the first banking trojan written in the Assembly language with a position-independent code. It means that the infection can run from anywhere in the memory, and it makes the trojan different from others. Backswap first attacked banks in Poland and then moved to target banks in Spain. The infection campaigns are known to be continuously running, although its technical evolution has slowed down.
Although there are multiple banking trojan families out there and they employ various distribution methods, most of the time, banking trojans use a similar set of data-stealing techniques. Those are as follow:
When a banking trojan uses the automatic transfer system, it can steal funds from the user’s account directly instead of just stealing their credentials. This method enables cybercriminals to automatically initiate financial transactions to predetermined accounts.
The two-factor authentication bypass exploits the flaunted two-factor authentication that is supposed to make online banking and, in general, web surfing safer. A banking trojan infection can modify banking pages in a way that requires the potential victim to enter their phone number before the one-time password is sent out. After that, users receive a text message with an outgoing link that installs malware. That is why online banking security experts maintain that users should not click on outgoing links they receive via text messages.
When the system is infected with a banking trojan that changes its DNS settings, whenever the victim tries to access a certain website, they get redirected to the fake banking pages. There, the moment they enter their login information, those credentials get stolen by the banking trojan. The Man-in-the-browser (MitB) attack vector is slightly similar to the malware that modifies DNS settings in that it is related to the webpage that the victim is on. Although instead of changing the DNS settings, the MiTB injects another HTML code into the web pages that victims access, and this allows the malware to steal the entered credentials straight from the browser’s memory.
As for keylogging and phishing, be sure to check out our in-depth descriptions of each technique via the links provided above.
Protection against banking trojans depends not only on the victim but also on the service provider. In other words, if we are talking about online banking services, they have to make sure that they employ the latest security measures to protect their systems and consequently your information from various threats.
Customers should also be aware of their bank policies, so they could avoid malware scams. It is also strongly recommended to delete all spam emails with outgoing links or attached files. If the email looks like it was sent by a financial institution, but you are not sure why you received it, you can always double-check with the said institution.
It is also vital to regularly change your passwords and other important credentials. It would be a good idea to employ a password manager tool that would generate strong and unique passwords. Finally, investing in an antimalware application should be at the top of your to-do list because it would protect your system and your data from banking trojans and many other threats.
Last updated: 2026-02-07