Gozi Trojan
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 90 % (High) |
| Infected Computers: | 75 |
| First Seen: | October 26, 2012 |
| Last Seen: | October 1, 2019 |
| OS(es) Affected: | Windows |
There's a variant of the Zeus Trojan that has targeted banks and credit unions in the United States in October of 2012. This malware infection, known as the Gozi Trojan, has managed to steal sensitive data belonging to customers of important credit unions all around the United States. The Gozi Trojan attacks the targeted financial institutions' websites by inserting fields into the website in order to trick visitors into handing over their private information. The Gozi Trojan has affected at least thirty banks in the United States, often using fraudulent signatures in order to infiltrate secure networks. ESG security researchers have also observed the involvement of more than one hundred botnets in an effort to steal money using information stolen with the Gozi Trojan and transfer that money to offshore accounts. The criminals responsible for the Gozi Trojan and for these fraudulent wire transfers appear to be based in the Russian Federation, which is an outstanding country for harboring many criminals associated with high profile computer crimes.
The Trojan Zeus, also called Zbot, is among the most notorious banking Trojans of all time. ESG security researchers have observed malware attacks associated with this threat happening on several countries. One of the factors that have influenced the spread of variants of this dangerous banking Trojan is that its code was released a few years ago, available to criminals on underground file sharing networks and websites. In the past, crafting a banking Trojan as sophisticated as the Zeus Trojan required expert computer knowledge and large amounts of time and money, but with the release of this malware code, it has allowed relatively low profile criminals to use this dangerous banking Trojan as a starting point for their own malware attacks. In fact, many computer users are calling attacks with this level of sophistication the 'new normal' due to the fact that banking Trojans like the Gozi Trojan use components of the Zeus Trojan to carry out sophisticated file stealing maneuvers.
Most Gozi Trojan attacks initiate with a social engineering approach. Like most Trojan infection, the Gozi Trojan requires the victims themselves to download and install this threat. Because of this, the Gozi Trojan is typically spread through spam email messages or bundled with other files, disguised as a harmless video codec or player download.
Table of Contents
SpyHunter Detects & Remove Gozi Trojan
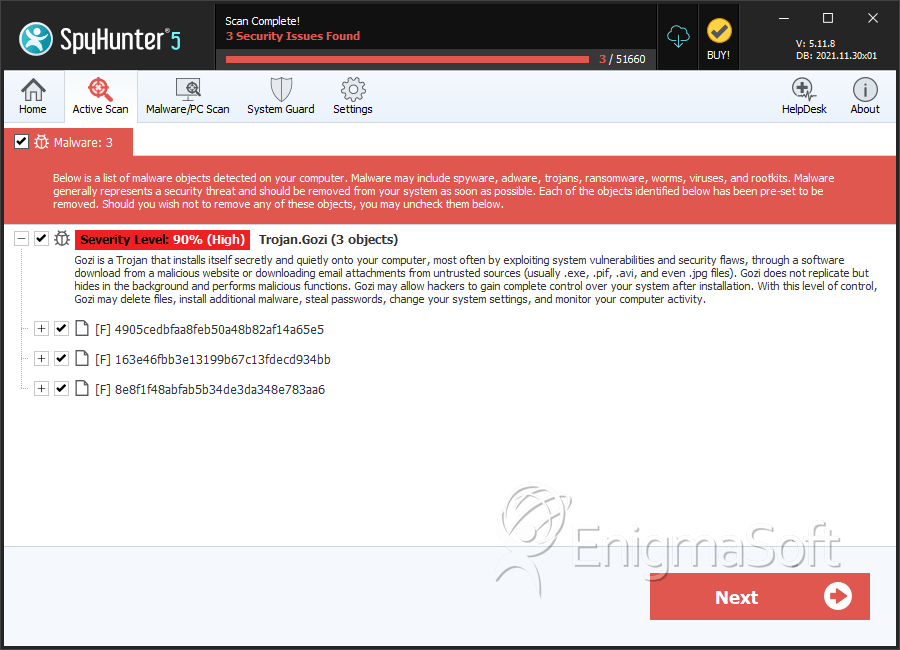
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 4905cedbfaa8feb50a48b82af14a65e5 | 4905cedbfaa8feb50a48b82af14a65e5 | 0 |
| 2. | 163e46fbb3e13199b67c13fdecd934bb | 163e46fbb3e13199b67c13fdecd934bb | 0 |
| 3. | 8e8f1f48abfab5b34de3da348e783aa6 | 8e8f1f48abfab5b34de3da348e783aa6 | 0 |

