Cerberus
 Sometimes instead of using their own hacking tools in various threatening operations, cybercriminals opt to sell them as a service instead. This trend is called malware-as-a-service and is rather popular in the world of cybercrime. This way, even individuals with no technical skills can operate a threat and generate revenue on the backs of innocent users. Recently, malware researchers uncovered a new malware-as-a-service being offered on a hacking forum. This threat is called Cerberus and is believed to have been made in the Russian Federation. Cerberus is an Android-based banking Trojan with impressive abilities to gather important data and avoid malware-debugging software.
Sometimes instead of using their own hacking tools in various threatening operations, cybercriminals opt to sell them as a service instead. This trend is called malware-as-a-service and is rather popular in the world of cybercrime. This way, even individuals with no technical skills can operate a threat and generate revenue on the backs of innocent users. Recently, malware researchers uncovered a new malware-as-a-service being offered on a hacking forum. This threat is called Cerberus and is believed to have been made in the Russian Federation. Cerberus is an Android-based banking Trojan with impressive abilities to gather important data and avoid malware-debugging software.
Table of Contents
Cheap and Updated Regularly
Unlike the popular Anubis banking Trojan, the Cerberus banking Trojan is rather cheap, which is likely to make it garner a significant amount of attention immediately. Furthermore, the creator of the Cerberus Trojan makes sure to update the hacking tool on a regular basis, which will make this malware-as-a-service even more attractive to potential buyers.
This Week in Malware Ep8: COVID-19 Lockdown Causes Rise in Telecommuting Scams #thisweekinmalware
Phishing Overlays
The Cerberus banking Trojan relies on display phishing overlays when the user attempts to interact with a legitimate banking application primarily. This Trojan also has a keylogger module, which will allow its operators to collect data from the victim, such as usernames and passwords for various accounts. Furthermore, this threat also can collect the contact list of the user.
Cerberus Hackers Seek to Modify Device Settings and Promote Malware via Social Media
The underlying code that permits Cerberus to gain access to an infected device starts with the accessibility services of Android devices being modified for certain privileges as shown in the image below.
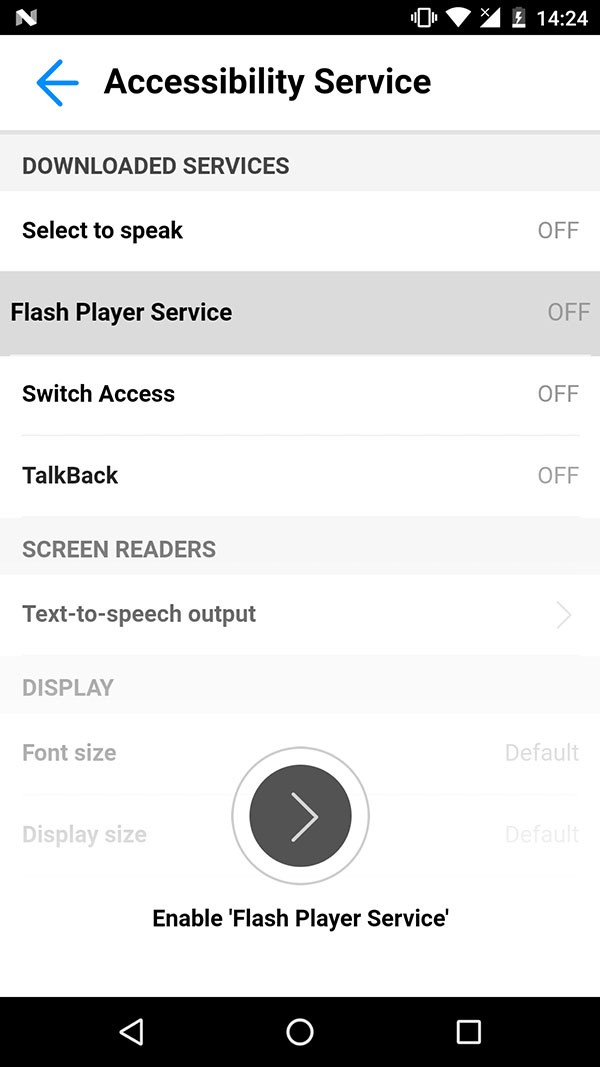
Android device infected with Cerberus having its accessibility service settings modified – Source: Threatfabric.com
It was uncovered by multiple security researchers that the threat actors behind the Cerberus banking malware have an official twitter account that has been used in the past to promote content and media content to spread the malware. The screenshot below is from their twitter account of a recent advertising campaign.
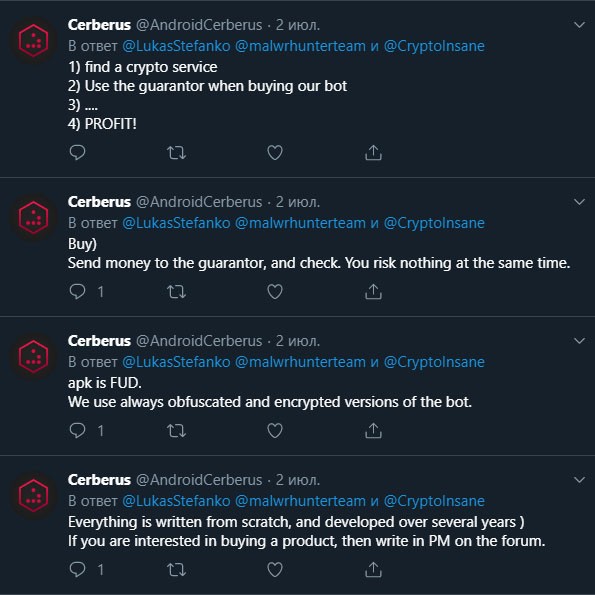
Image of Cerberus hackers’ twitter account and tweets promoting their malware – Source: Threatfabric.com
Limited Number of Banking Applications Targeted
The number of banking websites and applications, which the Cerberus Trojan was programmed to target is still fairly limited. Among them are seven U.S. banking applications, seven French banking applications, and one Japanese banking application. Apart from the banking applications, the Cerberus Trojan also has fifteen non-banking applications on its target list. The threat is capable of detecting when a user opens one of the applications on its list and would trick them into putting in their login credentials in a fake phishing overlay which is almost identical to the legitimate overlay of the banking portal. The Cerberus banking Trojan also may be able to avoid the two-factor authentication, which many banking websites offer as an additional safety measure.
The many clever actions of Cerberus Trojan involve Flash overlays. Such a process involves targeting the user by displaying a Flash overlay that looks like a harmless login screen, such as demonstrated in the image below. Through such an overlay, Cerberus may obtain banking details or credit card information from the user who may not suspect issue as the display form looks legitimate. The sandbox environment may prompt Cerberus to then collect the data and perform its malicious functions.
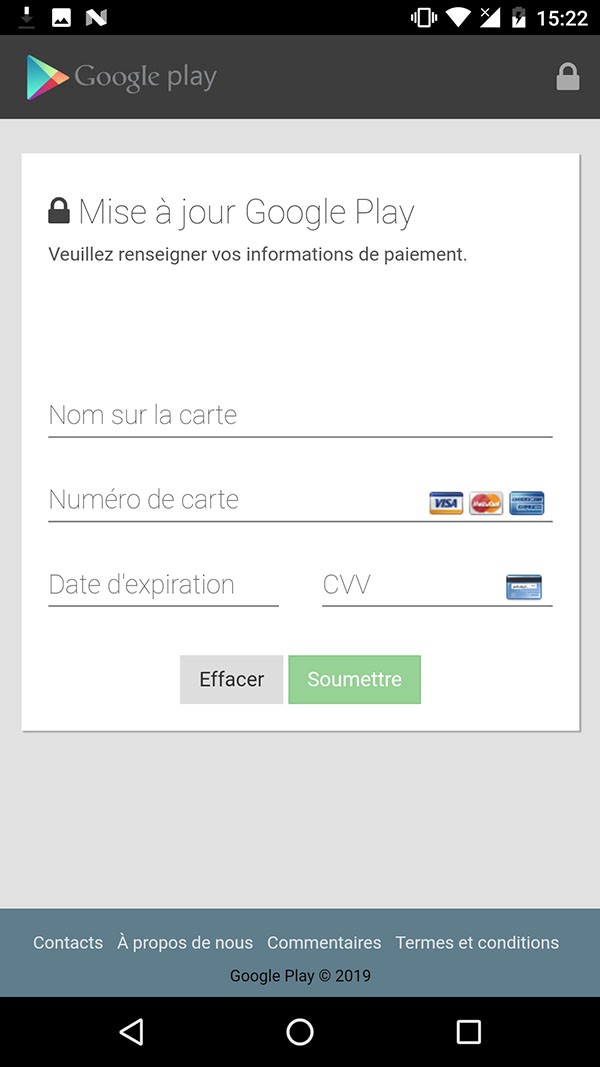
Example of a Flash overlay card form from a Cerberus-infected device - Source: Threatfabric.com
To avoid a potential sandbox environment, the Cerberus banking Trojan uses an interesting technique. This Trojan checks if it is being run on a legitimate device by using one of the sensors that are responsible for counting the user's footsteps - if it stays at zero, the malware will stay dormant. However, if a certain number of footsteps taken are reached, Cerberus will proceed with its harmful activity.
It is likely that many cyber crooks will take an interest in this malware-as-a-service offer, and we may see a surge of attacks involving the Cerberus Trojan in the near future. Android users need to stop underestimating the importance of the security of their devices and make sure to install a legitimate anti-malware application, which will keep their smart devices safe from threats like the Cerberus banking Trojan.

