StormCry Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | July 16, 2024 |
| OS(es) Affected: | Windows |
The StormCry Ransomware is threatening software designed to encrypt files on a victim's computer, rendering them inaccessible until a ransom is paid. This ransomware adds the '.stormous' file extension to the encrypted files, which is a clear indicator of infection. The attackers demand a ransom of $300 in Bitcoin and provide specific instructions for payment and contact.
Table of Contents
Key Characteristics
- File Extension: The StormCry Ransomware appends the '.stormous' extension to all encrypted files upon infection. For instance, a file named document.docx would be renamed to document.docx.stormous.
- Ransom Messages: Two ransom messages are generated on the infected system:
- readme.html
- pleas_readme@.txt
- Ransom Demand: The ransom demanded is $300, payable in Bitcoin.
- Payment Instructions:
- Bitcoin Wallet Address: 1DzX3w6Fb8yd78UMnWxfjnPQ14jWpEtVSA
- Contact Method: @StormousBot on Telegram
Detailed Ransom Message
The ransom messages, typically named readme.html and pleas_readme@.txt, contain the following information:
'All your files have been encrypted by StormCry Ransomware.
To restore your files, you need to pay $300 in Bitcoin to the following address:
Bitcoin Wallet: 1DzX3w6Fb8yd78UMnWxfjnPQ14jWpEtVSA
After payment, contact us via Telegram at @StormousBot for further instructions on decrypting your files.'
What to Do When Infected by the StormCry Ransomware
- Do Not Pay the Ransom: It is highly advised not to pay the ransom. There is no assurance that the attackers' perpetrators will provide the decryption key even after the payment is made. Additionally, paying the ransom encourages criminal activities and funds further attacks.
- Disconnect from the Network: Disconnect the infected device from the internet and any network to which it is connected immediately. This helps prevent the ransomware from spreading to other devices on the network.
- Identify the Ransomware: Confirm that the ransomware is indeed StormCry by checking the file extensions and the ransom messages generated.
- Report the Attack: Report the ransomware attack to local law enforcement and cybersecurity agencies. This can help authorities track the attackers and prevent further incidents.
- Restore from Backup: If you have a recent data backup, restore your files from the backup. Ensure that the backup is clean and not infected by the ransomware.
- Use Decryption Tools: Check if there are any available decryption tools for the StormCry Ransomware.
- Professional Help: If you are unable to decrypt your files or restore them from backup, consider seeking help from cybersecurity professionals who specialize in ransomware recovery.
- Improve Security Measures:
- Update Software: Maintain your operating system and all software up-to-date with the latest security patches.
- Use Anti-Malware Software: Install and regularly update anti-malware software.
- Backup Regularly: Regularly back up your data to an external drive or cloud storage.
- Educate Users: Train employees and users on how to recognize phishing emails and other common ransomware delivery methods.
The StormCry Ransomware is a threat that can cause significant damage to personal and organizational data. By understanding its characteristics and following the recommended steps, victims can mitigate the impact and reduce the likelihood of future attacks. Do not forget that prevention and preparedness are key in the fight against ransomware.
The full ransom message left by the StormCry Ransomware to its victims reads:
'Oops. Your files have been encrypted!
Time remaining for payment:About bitcoin How to buy bitcoin?
Contact Us
Download decryption tool
What is happend ?
Your important files are encryption.Many of your documents,photos ,videos,database and other files are no longer accessible because they have been encrypted.Maybe you are busy looking for a way to recover your file,but do not waste your time.Nobody can recover your files without our decryptionCan I Recover My Files?
Sure.We guarantee that you can recover all your files safely and easily.But you have not so enough time.You can decrypt some of your files for free. Try now by clicking .But if you want to decrypt all your files,you need to pay.You only have 3 days to submit the payment.After that the price will be doubled.Also,if you don't pay in 7 days,you won't be able to recover your files forever.We will have free events for users who are so poor that they couldn't pay in 6 months
How Do I Pay?
Payment is accepted in Bitcoin only. To contact the owner of the key and for more information, contact us via the Telegram bot @StormousBot. Please check the current price of Bitcoin and buy some Bitcoin. Then send the correct amount to the specified address. After payment, click . The appropriate time to check in is from 9:00 AM to 11:00 AM.Send $300 to this address: 1DzX3w6Fb8yd78UMnWxfjnPQ14jWpEtVSA
To decrypt your files, you must first download a decryption software. Follow the instructions after payment to get the software and decryption key.'
SpyHunter Detects & Remove StormCry Ransomware
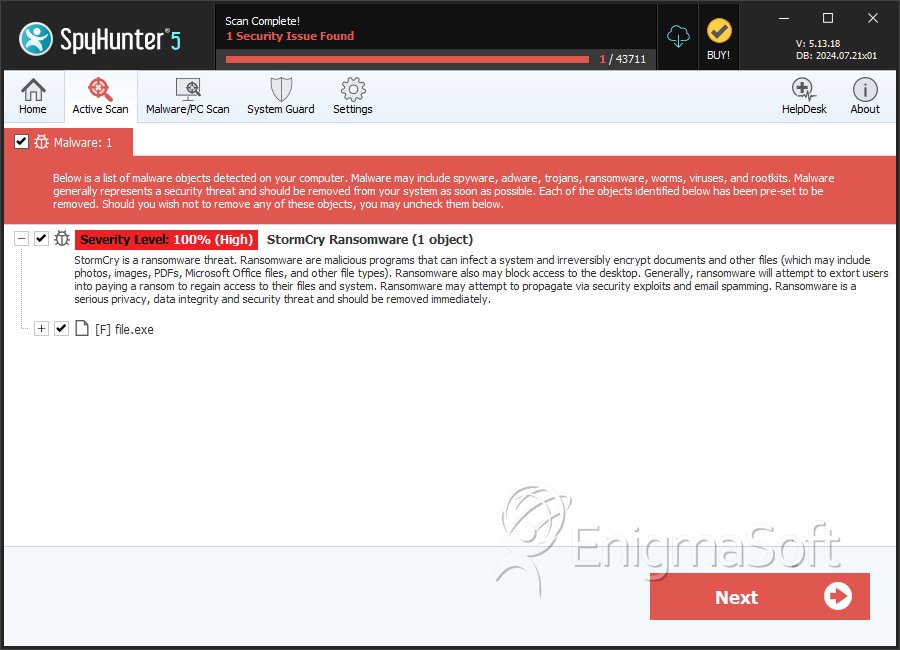
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | f0514037777ec49400b7ac301ea70c52 | 1 |