Spook Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 2 |
| First Seen: | October 13, 2021 |
| OS(es) Affected: | Windows |
The Spook Ransomware is a threat that appears to be deployed against corporate targets predominantly. However, in no way does that mean that individual systems cannot be affected. If the Spook Ransomware manages to infiltrate itself onto the device successfully, it will initiate an encryption process with an uncrackable cryptographic algorithm. All affected files will no longer be accessible.
Exactly like most ransomware, Spook also marks each file it locks by modifying that file's original name. In this case, instead of using a specific word, the threat appends a string of characters - '.PUUEQS8AEJ' as a new file extension. Upon locking all targeted file types, the malware proceeds to deliver two ransom notes with instructions for its victims. Users will be shown identical messages in a pop-up window and inside a text file named 'RESTORE_FILES_INFO.txt'
Table of Contents
Spook Ransomware’s Demands
The lengthy ransom note states that apart from locking the files stored on the compromised devices, the attackers have also been able to steal vast amounts of sensitive information. The note mentions billing data, financial reports, client details, and more. The cybercriminals threaten to release the information and cause severe repercussions for the affected companies if their demands are not met.
The note also mentions that victims can test the ability of the hackers to restore the encrypted files. They can do so by visiting a dedicated website hosted on the TOR network. There, victims can upload up to 3 files to be decrypted for free. The site is also the only way to contact the attackers.
The full text of the note is:
'YOUR COMPANY WAS HACKED AND COMPROMISED!!!
All your important files have been encrypted!
Our encryption algorithms are very strong and your files are very well protected,
the only way to get your files back is to cooperate with us and get the decrypter program.Do not try to recover your files without a decrypter program, you may damage them and then they will be impossible to recover.
For us this is just business and to prove to you our seriousness, we will decrypt you three files for free.
Just open our website, upload the encrypted files and get the decrypted files for free.! WARNING !
Whole your network was fully COMPROMISED!We has DOWNLOADED of your PRIVATE SENSITIVE Data, including your Billing info, Insuranse cases, Financial reports,
Business audit, Banking Accounts! Also we have corporate correspondence, information about your clients.
We got even more info about your partners and even about your staff.Additionally, you must know that your sensitive data has been stolen by our analyst experts and if you choose to no cooperate with us,
you are exposing yourself to huge penalties with lawsuits and government if we both don't find an agreement.
We have seen it before cases with multi million costs in fines and lawsuits,
not to mention the company reputation and losing clients trust and the medias calling non-stop for answers.
Come chat with us and you could be surprised on how fast we both can find an agreement without getting this incident public.IF YOU ARE AN EMPLOYER OF A COMPANY THEN YOU SHOULD KNOW THAT SPREADING SENSITIVE INFORMATION ABOUT YOUR COMPANY BEING COMPROMISED IS A VIOLATION OF CONFIDENTIALITY.
YOUR COMPANY'S REPUTATION WILL SUFFER AND SANCTIONS WILL BE TAKEN AGAINST YOU.WE HIGHLY SUGGEST THAT YOU DON'T CONTACT THE AUTHORITIES REGARDING THIS INCIDENT BECAUSE IF YOU DO, THEN AUTHORITIES WILL MAKE THIS PUBLIC WHICH COMES WITH A COST FOR YOUR ENTERPRISE.
THE RECOVERY PROCESS OF YOUR FILES WILL BE FASTER IF YOU COME AND CHAT WITH US EARLY. IF YOU CHOOSE TO COOPERATE, YOU WILL SEE THAT WE ARE PROFESSIONALS WHO GIVES GOOD SUPPORT.Instructions for contacting us:
You have way:
Using a TOR browser!
Download and install TOR browser from this site: hxxps://torproject.org/
Open the Tor browser. Copy the link: hxxp://spookuhvfyxzph54ikjfwf2mwmxt572krpom7reyayrmxbkizbvkpaid.onion/chat.php?track=PUUEQS8AEJ and paste it in the Tor browser.
Start a chat and follow the further instructions.Key Identifier: -
Number of files that were processed is:'
SpyHunter Detects & Remove Spook Ransomware
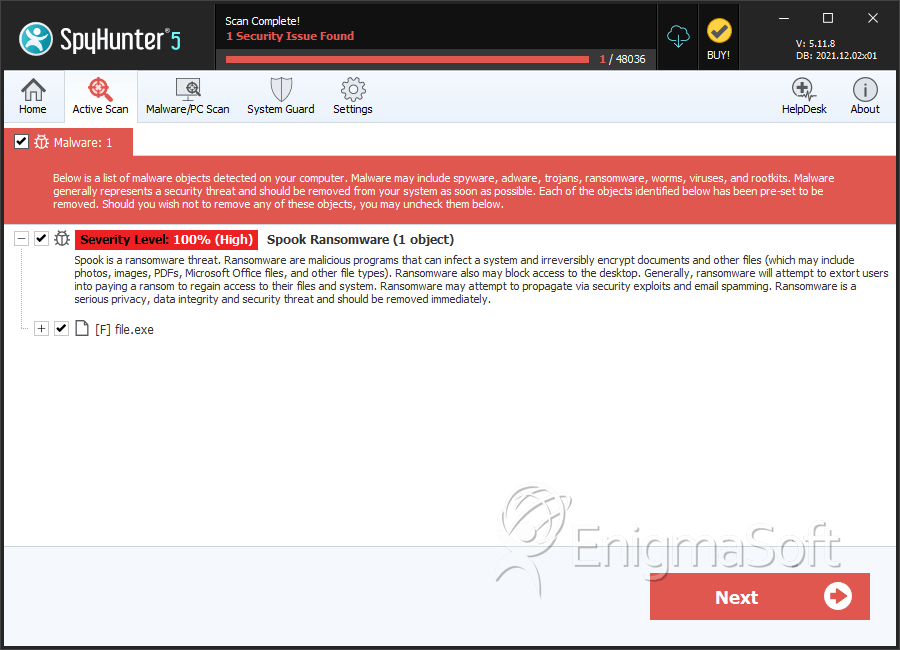
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 537a415bcc0f3396f5f37cb3c1831f87 | 1 |
| 2. | file.exe | 1c7b91546706f854891076c3c3c964c0 | 1 |

