SNAKE Ransomware
SNAKE Ransomware Image
Hundreds upon hundreds of low-quality ransomware threats are distributed online every year. However, high-end data-locking Trojans are far sparser and more interesting. One of the latest threats of this type is called SNAKE Ransomware. The SNAKE Ransomware appears to be a sophisticated and well-thought-out project likely the doing of experienced cybercriminals. This threat targets corporate networks and makes sure to cause maximum damage by encrypting the data of whole networks. Interestingly enough, the SNAKE Ransomware is written in a programming language that is not very common when it comes to the creation of malware – the Golang language. On top of this, the authors of the SNAKE Ransomware have made sure to obfuscate their threat heavily, which makes analyzing and combating the data-locking Trojan far more difficult.
This Week in Malware Ep3: Snake Ransomware
Table of Contents
Propagation and Encryption
The infection vectors involved in the distribution of the SNAKE Ransomware are unknown currently. The attackers may be using fraudulent emails with corrupted attachments to compromise their targets. To lock the targeted data, the SNAKE Ransomware will apply a secure encryption algorithm that will render the data unusable. Most ransomware threats apply a fixed extension to the newly locked data. However, this is not what happens with the SNAKE Ransomware. Instead, the SNAKE Ransomware appends a different five-symbol extension to every affected file. For example, a file, which was named ‘winter-sun.jpeg’ initially, could be renamed to ‘winter-sun.jpeg.7vO3s.’ However, each file has a unique, randomly generated five-character extension.
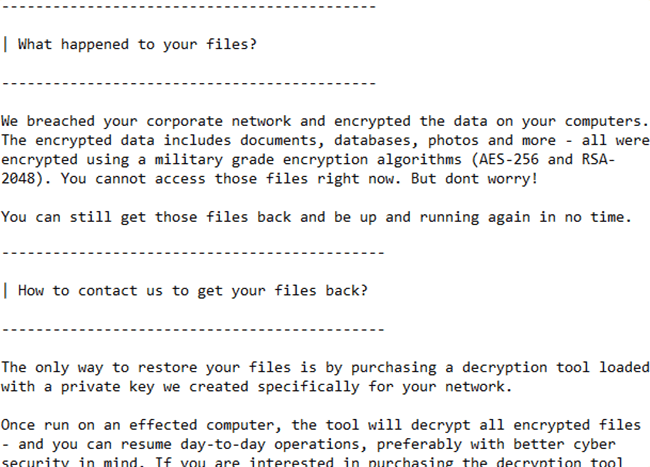
The Ransom Note
Next, the SNAKE Ransomware will drop its ransom message, which is contained in the ‘Fix-Your-Files.txt’ file. Like with most ransomware threats, the SNAKE Ransomware’s ransom note is dropped on the victim’s desktop. The creators of the SNAKE Ransomware demand to be paid a significant sum if they are to provide a decryption tool. The attackers want to be contacted via email for additional details – ‘bapcocrypt@ctemplar.com.’
Do not trust the promises of cyber crooks. Countless users have fallen for the trickery of cybercriminals, and despite paying what is demanded of them, they often remain empty-handed. If you want to remove the SNAKE Ransomware from your system, you should trust a reputable anti-malware solution that will take care of this pest and keep you safe in the future.