SnakeLocker Ransomware
The SnakeLocker Ransomware is an encryption ransomware Trojan that was first observed on July 24, 2017. The SnakeLocker Ransomware carries out a typical variant of this attack, encrypting the victims' files and then requesting the payment of a ransom in exchange for the decryption key, necessary to recover the affected files. The SnakeLocker Ransomware seems to target English speakers, and most of its attacks have been concentrated in Europe and the United States.
Table of Contents
This SnakeLocker Has Two Heads
There are two variants of the SnakeLocker Ransomware, which use different extensions to identify the files affected by the attack. One of these versions of the SnakeLocker Ransomware will mark the encrypted files with the file extension '.snake' and the other will use the file extension '.TGIF.' There are very slight differences between both versions of the SnakeLocker Ransomware, which make it difficult for malware researchers to truly assess how the SnakeLocker Ransomware is being distributed. It is likely that the SnakeLocker Ransomware is being delivered to victims in spam email messages, which will include a file attachment in the form of a Microsoft Word document with enabled macro scripts. When the document is opened, the SnakeLocker Ransomware will be downloaded and installed, beginning its attack on the victim's computer.
How the SnakeLocker Ransomware may Infect a Computer
The SnakeLocker Ransomware infection itself is no different from most encryption ransomware Trojans. Using the AES and RSA encryptions combined, the SnakeLocker Ransomware will encrypt the victim's files, searching for all files on the infected computer that match a list of file extensions. The SnakeLocker Ransomware will target the user-generated files while leaving the Windows operating system mostly intact. This means that the SnakeLocker Ransomware will encrypt numerous file types, including spreadsheets, texts, databases, videos, music, audio, and files belonging to numerous commonly used applications. The files encrypted by the SnakeLocker Ransomware attack will be marked with one of the two file extensions associated with the SnakeLocker Ransomware.
The SnakeLocker Ransomware’s Ransom Demand
The SnakeLocker Ransomware displays a ransom note on the infected computer after encrypting the victim's files. This ransom note takes the form of an HTML file that is dropped on the infected computer's desktop named 'INSTRUCTIONS-README.html' and a new desktop wallpaper image, which takes the place of the computer user's default image. These ransom notes contain the following message, displayed on the victim's computer:
'Your files have been securely encrypted with top notch, extremely secure encryption algorithm. The only way you can
get these files back is to pay ransom of 0.1 Bitcoins.
To proceed to the next step in this process, download the Tor Browser Bundled here . Open the Tor Browser Bundle and proceed to the following link:
[.ONION DOMAIN]
This link will give you payment instructions .
Don't know hot to get Bitcoins? No problem. You can buy bitcoins, at any of the following websites:
[LINKS TO POPULAR BITCOIN SITES]'
PC security researchers advise computer users to disregard the SnakeLocker Ransomware message. Paying these ransoms is not recommended for several reasons:
- Paying the SnakeLocker Ransomware ransom allows con artists to continue creating and developing ransomware Trojans like the SnakeLocker Ransomware.
- Con artists will rarely keep their word and help victims of the SnakeLocker Ransomware recover their files after the attack. They are just as likely to demand additional ransom payments or simply ignore the victim's payment.
- Once the victim pays the ransom, these people may target that particular victim for future ransomware attacks and new spam email hoaxes since the victim has already demonstrated a willingness to pay.
Instead of paying the SnakeLocker Ransomware ransom, PC security analysts strongly advise computer users to take preventive measures to ensure that recovery is possible after a SnakeLocker Ransomware infection. The best protection against these attacks is to have file backups on an external memory device or the cloud. This, combined with a reliable security program, can help protect computer users from most encryption ransomware Trojans.
SpyHunter Detects & Remove SnakeLocker Ransomware
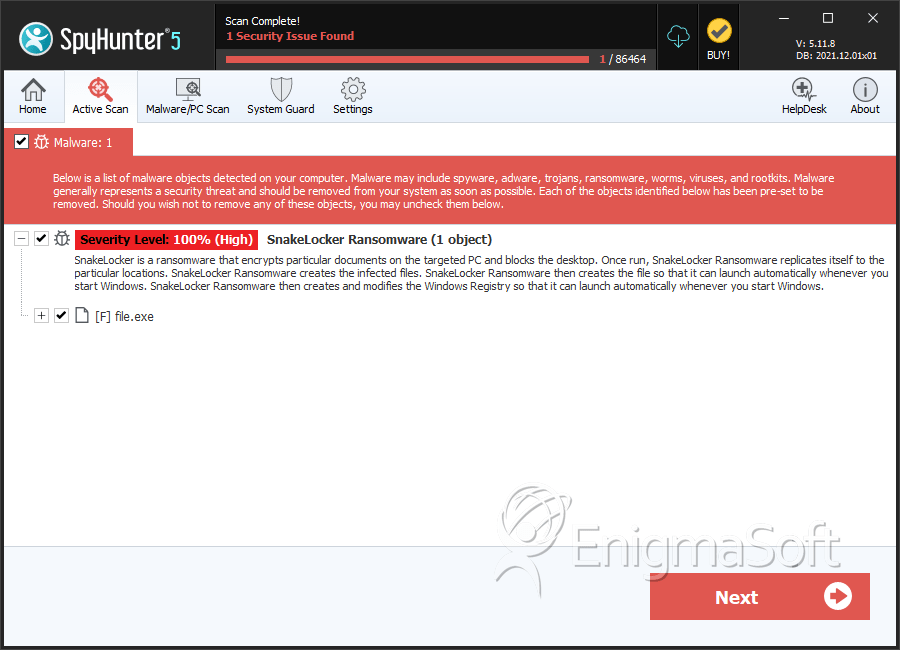
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 7602f5d19df01ea70f957e23837024a8 | 0 |
| 2. | file.exe | f3fbc6000cfb7371623acd54efe853cb | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.