Shade Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 17,153 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 4,909 |
| First Seen: | September 23, 2015 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
Shade Ransomware is an encryption ransomware infection. The Shade Ransomware is specifically designed to take over the victim's computer, encrypting the victim's files and then asking for the payment of a ransom to restore these files to the affected computer user. The number of encryption threats that are active in the wild is growing up. Like many other encryption threats that are currently active, the Shade Ransomware encrypts the victim's files, which become unrecoverable unless the victim pays the Shade Ransomware's ransom. PC security analysts strongly advise computer users to avoid paying the Shade Ransomware's ransom. Paying to restore the affected files enables the creators of the Shade Ransomware to continue carrying out their attacks. There is also no guarantee that the encrypted files will be restored, even if computer users pay the ransom. Instead, precautionary measures should be taken to ensure that the files encrypted by the Shade Ransomware can be recovered from a backup.
Table of Contents
How the Shade Ransomware Infection Works
PC security researchers have observed a marked increase in encryption ransomware in recent years. What makes these kinds of attacks devastating is that computer users cannot recover the encrypted files, even if the infection is removed.The Shade Ransomware is no exception. The Shade Ransomware attack is simple: once the Shade Ransomware enters a computer, it scans the victim's computer for all files matching a list of extensions. After encrypting all these files and changing their extensions, the Shade Ransomware displays a ransom note. The Shade Ransomware uses text files, displays pop-up messages, and changes the victim's desktop image to display a ransom note demanding to decrypt the victim's files. The Shade Ransomware has been associated with the following message:
"All the important files on your computer were encrypted.
To decrypt the files you should send the following code:
A4B50EC5C45D44A401F9|0
to e-mail address decode010@gmail.com or decode1110@gmail.com.
Then you will receive all necessary instructions.
All the attempts of decryption by yourself will result only in irrevocable loss of your data."
The Shade Ransomware also uses a message written in Russian, reflecting the Shade Ransomware's Russian origin. The Shade Ransomware demands payment using Bitcoin and TOR to ensure that payments remain anonymous. The Shade Ransomware ransom amount may add up, totaling several hundred dollars. Even after paying, computer users receive no guarantee that their files will be restored.
Protecting Your Computer from the Shade Ransomware and Similar Attacks
Unfortunately, it is not currently possible to restore files that have been encrypted by the Shade Ransomware. The decryption key for these kinds of attacks is not stored anywhere on the victim's computer or in the threat's code itself. Some files may be recovered from the infected computer's shadow volume. However, the Shade Ransomware deletes shadow copies of encrypted files, so this is not a reliable method for recovery. The best way to thwart the Shade Ransomware attacks is protecting your machine from them preemptively. Some measures you can take to avoid becoming a victim of the Shade Ransomware and other ransomware attacks include:
- Back up all of your files using an external memory device or a Cloud-based backup method.
- Use a strong security program that is fully up-to-date to intercept any threatening components.
- Avoid visiting websites considered unsafe, such as pornographic websites or websites with pirated content.
- Use a reliable anti-spam filter to ensure that spam emails with threatening file attachments never make it to your inbox.
If your files become encrypted, the best way to deal with the Shade Ransomware is to wipe the affected hard drive entirely and restore its contents from a backup. You should ensure that the Shade Ransomware is entirely removed before restoring backed-up files, or your files may be re-encrypted by the Shade Ransomware.
SpyHunter Detects & Remove Shade Ransomware
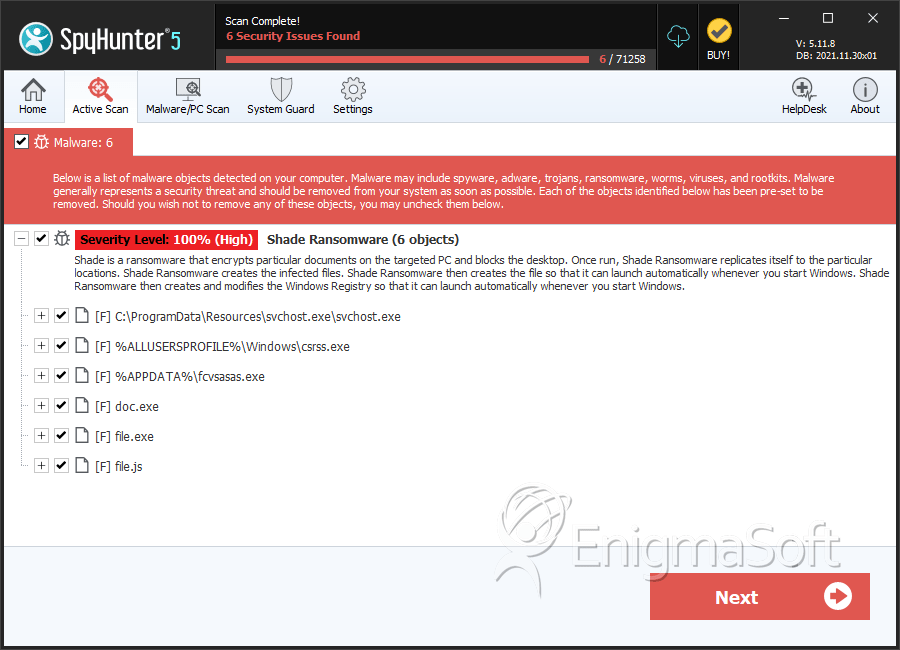
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | svchost.exe | 9c4bc5f6bc61fadc7d5c1481990ab451 | 681 |
| 2. | B32035D7.exe | 8fbe9a961300fb62df587ed708160655 | 356 |
| 3. | csrss.exe | 4039c1e8c180688104b67c315473fdb4 | 5 |
| 4. | fcvsasas.exe | bbcf995c22756a6a634a0f54bae05ea0 | 1 |
| 5. | doc.exe | dfcd797a1ffdab6dbedafe190d0992ad | 0 |
| 6. | file.js | 63ba865c22863ef7d354634bace10166 | 0 |
| 7. | file.exe | 84307f2217068875dd710248c6f5fedf | 0 |