SAD Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 10 |
| First Seen: | November 14, 2017 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
The SAD Ransomware is a file encoder Trojan that was reported by computer security researchers on November 3rd, 2017. The threat payload is delivered to potential victims by using macro-enabled documents attached to spam emails. Usually, the attached documents are presented as messages from a trusted company to trick users into thinking the file is safe to open. The threat authors take advantage of the fact that Windows interprets macro scripts as a sequence of user commands since macros are meant to help people automate repetitive tasks.
Once the SAD Ransomware is installed, the Trojan runs a scan of the accessible memory storage and determines which files to encrypt. Samples of the Trojan showed that it might use the name 'picture.exe' when it runs on a compromised device. The threat is reported to use a modified AES-256 cipher and add either the '.
- _HELPME_DECRYPT_.txt
- _HELPME_DECRYPT_.hta
- _HELPME_DECRYPT_.html
These messages serve as ransom notes. The SAD Ransomware may offer help with decrypting your data if you are willing to deliver the payment of 0.3 Bitcoin (2152 USD/1858 EUR) to their wallet address. All three versions of the ransom notification offer the same content:
'-- ALL YOUR FILES HAVE BEEN ENCRYPTED --
All of your data(photo, documents, databases,...) have been encrypted with AES 256 bit and a private and unique key generated for this computer.
It means that you will not be able to accsess your files anymore until they´re decrypted.
The private key is stored in our servers and the only way to receive your key to decrypt your files is to pay.
The only one way to decrypt your files is to receive the private key and decryption program.
Dont waste your time. No one will be able to recover tem without our decryption service.
The payment has to be done in Bitcoin to a unique address that we generated for you, Bitcoins are a virtual currency to make online payments.
[edit: followed by instructions on how to obtain Bitcoins]
YOUR PERSONAL IDENTIFICATION:
51C51342BC305F401E014AAF44A***'
The SAD Ransomware may be aimed at English-speaking users primarily, but that does not mean everyone else is safe. Threats like the Hermes 2.1 Ransomware, the Relock Ransomware, and the SAD Ransomware should not be taken lightly. Most of the Trojans on the crypto-threat landscape today can perform irreversible data encryption, and it is recommended to employ the services of a reliable backup manager. Building backups often allow PC users to benefit from a stable and secure data consistency. AV engines recognize the objects associated with the SAD Ransomware and mark them as:
- Ransom.CryptXXX
- Trojan.GenericKD.12532403
- Trojan.MulDrop7.46328
- Trojan.Ransom.Sad (A)
- Trojan.Win32.FileCoder.eutheq
- Trojan/Win32.Ransom.R212087
- malicious_confidence_100% (W)
Table of Contents
SpyHunter Detects & Remove SAD Ransomware
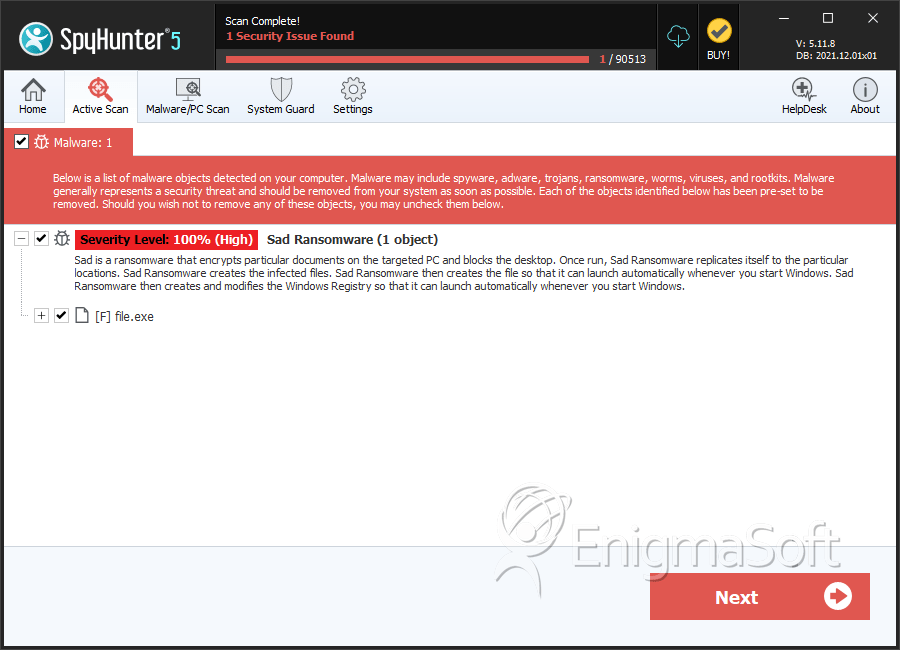
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | f4c2f65b5b89d4f4e74099571b40c0d5 | 1 |
