Hermes 2.1 Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 38 |
| First Seen: | February 15, 2017 |
| Last Seen: | June 17, 2020 |
| OS(es) Affected: | Windows |
The Hermes 2.1 Ransomware is a file encoder Trojan that was released to users using a massive spam campaign. Emails loaded with a macro-enabled Microsoft Word document were received by users. Loading the attached file resulted in a security compromise that allowed the Hermes 2.1 Ransomware to be installed on the system with administrative privileges. The threat appears to be aimed at English-speaking users and TOR-to-Web services for its 'Command and Control' communications. The Hermes 2.1 Ransomware is the third release in the Hermes Ransomware line of Trojans preceded by the original version and Hermes 2.0.
Table of Contents
The Attack Vector Used in the Hermes 2.1 Ransomware Campaign
The new variant emerged in the first days of November 2017, and cybersecurity vendors managed to pick it up relatively early. The Hermes 2.1 Ransomware is not very different from previous adaptations, but it uses a new set of servers to receive and transmit data. Additionally, the threat authors are using new email accounts to spread their product. A new packaging technique and encryption is implemented to make it harder for AV scanners to recognize the Hermes 2.1 Ransomware payload as well. The threat is reported to attach the '.HRM' extension to the file names and use a secure AES cipher that makes it possible for the threat actors to be the only ones with a viable decryption solution. For example, 'Hymenoptera wings.pptx' is renamed to 'Hymenoptera wings.pptx.HRM.' The Trojan at hand is known to encrypt standard data formats associated with Microsoft Office, Windows Photos, VLC Media Player and database managers.
The Hermes 2.1 Ransomware Limits Recovery Options
The Hermes 2.1 Ransomware deletes the Shadow Volume Copies made by Windows for recovery purposes and encourages users to decrypt their data using the "services" provided by its creators. The ransom request is presented within a file named 'DECRYPT_INFORMATION.html' that can be located on the desktop and be opened with any modern Web browser. The enclosed message reads:
'All your important files are encrypted Your files has been encrypted using RSA2048 algorithm using unique public-key stored on your PC. There is only one way to get your files back: contact with us, pay and get decryptor software. You have "UNIQUE_ID_DO_NOT_REMOVE" file on your desktop also it duplicated in some folders, its unique ID key , attach it to letter when contact with us. Also, you can decrypt 3 files for test. We accept Bitcoin, you can find exchangers on h[tt]p://www.bitcoin.com/buy-bitcoin and others.'
The Hermes 2.1 Ransomware team is known to welcome victims into writing a message to the Hermes team by using channels on the BitMessage platform. The BitMessage platform is based around TOR relays, and it is challenging to trace the origin and destination of the encrypted messages. The teams behind the Synack Ransomware and the Master Ransomware are big fans of the IM platform. The Hermes team is reported to operate the following accounts:
BM-2cTSTDcCD5cNqQ5Ugx4US7momFtBynwdgJ@bitmessage.ch
BM-2cT72URgs1AWGV6Wy6KBu2yuj3ychN5vxC@bitmessage.ch
Remove the Hermes 2.1 Ransomware before You Load Backups
It is recommended that you remove the Hermes 2.1 Ransomware with the help of a credible anti-malware tool. Paying the ransom is not guaranteed to yield a satisfactory decryption service. Backups and system recovery disks should help you rebuild your file structure safely and reliably instead of spending your money and hoping for the best. It may be a good idea to explore what services such as Google Drive and other cloud-based solution have to offer regarding data security.
SpyHunter Detects & Remove Hermes 2.1 Ransomware
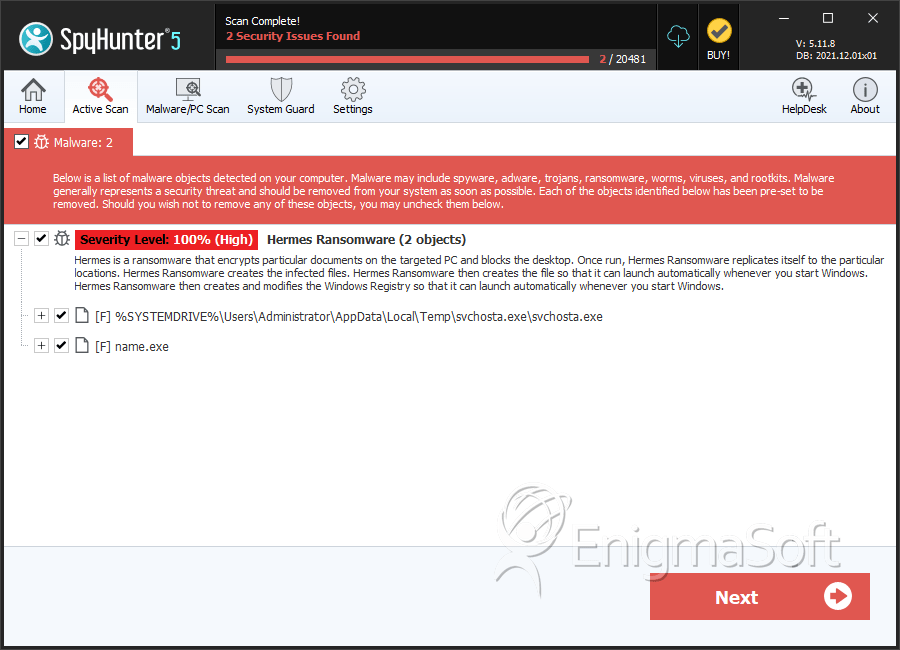
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | svchosta.exe | af93204bc5fa9b99c9b9b9012be9bb1b | 8 |
| 2. | name.exe | 6bbff3614efa6329bb43b2b0a6be8b9c | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.