Relock Ransomware
The Relock Ransomware is a data encryption Trojan that was reported for the first time on November 3rd, 2017. The Relock Ransomware Trojan is classified as a mid-tier crypto-threat that uses secure cryptographic algorithms to make data unreadable and suggest the user pay a ransom for the access to the encrypted data. The developers of the Relock Ransomware weaponized an open-source code and delivered the threat payload via spam emails to users. Cybersecurity experts alert that the Relock Ransomware team is using standard ransomware tactics to distribute their product to potential victims. Corrupted macros are embedded into seemingly harmless Microsoft Word documents that may refer to recent purchases on Amazon, transaction via PayPal, and other actions on reputable services.
Table of Contents
A Misleading Message Causes to Installing the Relock Ransomware
As you may expect, many users who may not have spotted the hoax have fallen victims to the Relock Ransomware. The Relock Ransomware Trojan appears to be programmed to apply an AES-256 cipher to the targeted data containers and adds the '_[RELOCK001@TUTA.IO]' suffix to their file names. For example, 'Lepidoptera wings.png' is renamed to 'Lepidoptera wings.png_[RELOCK001@TUTA.IO].' The appended suffix is expected to serve as an invitation for the user to send an email to the threat authors and ask how to decrypt the data. Computer security analysts add that the Relock Ransomware Trojan is likely to prevent users from loading photos, videos, audio, databases, presentation, eBooks, spreadsheets and contacts lists. More information can be found in the document '!OoopsYourFilesLocked!.rtf' that the Relock Ransomware is programmed to leave on the desktop and delete its file structure to prevent reverse engineering a decryptor. The Relock Ransomware may change the desktop background of compromised systems and show the following text colored in red on a black background:
'Warning! All your files were encrypted with strong crypto algorithm!
Without your personal key and special software data recovery is impossible!
If you want to restore your files, please write us to the e-mails:
relock001@tuta.io OR relock001@yahoo.com
* Additinal information you can find in files: !OoopsYourFilesLocked!.rtf'
Data Recovery Options are Limited Significantly
It may be possible to begin negotiations with the cybercrooks by writing to 'relock001@tuta.io' and 'relock001@yahoo.com.' However, that course of action is advised against. Cybersecurity researchers remind that the ransomware business can be very lucrative if users don't know how to protect their data. You should incorporate a reliable anti-malware shield and a good backup tool to face the cyber threats of today. Unfortunately, the encrypted data that has the '_[RELOCK001@TUTA.IO]' extension can't be recovered yet. Consider loading backups if you have any available.
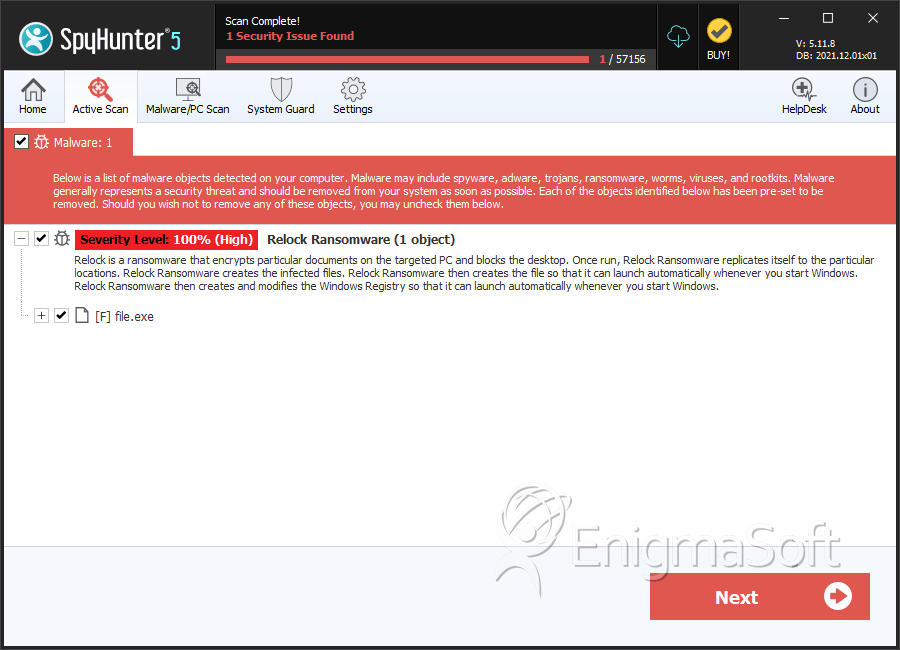
SpyHunter Detects & Remove Relock Ransomware
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | c97075cf1f28b322da460adfd404310f | 0 |