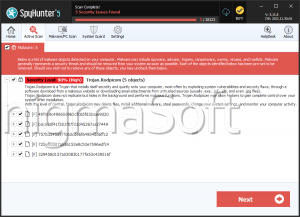
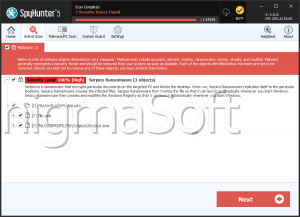
Pico Ransomware
The Pico Ransomware is an encryption ransomware Trojan, designed to take victims' files hostage to demand the payment of a ransom. The Pico Ransomware is typically distributed through the use of corrupted email attachments, often employing social engineering techniques to mislead computer users into opening the attached file. The Pico Ransomware is installed onto the victim's computer by some embedded macro scripts used by these files. This is a method commonly used by many encryption ransomware Trojans, making it important for computer users to disable macros if not needed and become cautious about opening any unsolicited email attachments.
How the Pico Ransomware Trojan Attacks a Computer
The Pico Ransomware uses a strong encryption algorithm to make the victim's files inaccessible. The Pico Ransomware targets the user-generated files, which may include a wide variety of media files, document types, databases and numerous others. The files that are targeted in attacks like the Pico Ransomware include:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
The Pico Ransomware's decryption key is stored on its Command and Control servers, which are out of the reach of the victim completely. This means that when the Pico Ransomware encrypts a file, it becomes unrecoverable with current technology. However, it is easy to recognize the damaged files because they will have the file extension '.PICO' added to each file affected by the attack. The Pico Ransomware then demands a ransom payment from the victim in the form of a text file demanding 100 USD to be paid in Bitcoin or Etherium. The ransom note is displayed in a file named 'README.txt' that contains the following message:
'Pico Ransomware y1.0
Your files was encrypted. To decrypt your files,
follow next steps: 1. send $100 to one of these wallets:
BTC: 3CC9umWMV1nrn8nadZ9eGnJ76Bg4jinem
ETH: 0xBb171CC7113dbdc532C42D22928f6b6c56fBE242
2. send your TXID and your MachinelD to mail
E-Mail: de.picocode@gmail.com
MactinelD:
[random characters]
Do not waste your time, files can only be
decrypted by our decode tool.'
Dealing with the Pico Ransomware Infection
Paying the Pico Ransomware ransom or contacting the criminals responsible for the Pico Ransomware attack is not the best solution for the victims. Instead, computer users are advised to take steps to back up all of their data. The file backups are the best protection against infections like the Pico Ransomware because they allow computer users to restore any data compromised by the Pico Ransomware without having to contact the criminals or risk paying the Pico Ransomware ransom and not receiving anything in return. Apart from file backups, it is important to have a security program that is always up-to-date.