Serpico Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | August 29, 2016 |
| Last Seen: | January 10, 2019 |
| OS(es) Affected: | Windows |
The Serpico Ransomware is a dangerous variant of the DetoxCrypto family of threats. The variants of the Serpico Ransomware seems to be written in Serbian and Croatian and designed to attack computer users in these countries. The Serpico Ransomware does not add a special extension to the files that it encrypts, unlike many other ransomware threats. The Serpico Ransomware has received this name because of the directory name it uses to save the files associated with the Serpico Ransomware attack.
Table of Contents
The Serpico Ransomware and Other DetoxCrypto Family Variants
The Serpico Ransomware and other variants in this family of threats seem to be created using a threat builder, resulting in attacks that have very different ransom notes and superficial characteristics while carrying out the same attack at their core. There were two previous variants in this family, one using content related to PokemonGO and the other using a scarier approach and including a backdoor component.
The Serpico Ransomware may be related to a RaaS (Ransomware as a Service) service that is active on the Dark Web currently. Con artists may create the Serpico Ransomware variants and operate on an affiliate system, giving a percentage of their earnings to the creators of this ransomware family. The Serpico Ransomware and all of its variants use the AES encryption to encrypt data on the victim's computer. The Serpico Ransomware and its variants stop the MySQL and MSSQL services on the infected machine, display a LockScreen with the ransom note, and also play an audio file in the background. For example, in the case of the Pokemon Go variants, an audio file containing a video game music would be played. Like its variants, the Serpico Ransomware's ransom note instructs the victim to contact an included email address in order to pay the ransom.
The Serpico Ransomware Attack
The Serpico Ransomware and its variants use a single executable file in their distribution vectors (for example, attached as an email attachment). When this corrupted executable file runs, it extracts several files to the victim's computer. In the case of the Serpico Ransomware and other variants in this family, the files extracted are the executable that carries out the encryption (which may have an innocuous name that makes it appear as a legitimate Windows process). In previous variants, this file has been named 'MircosoftHost.exe.' The other files that are installed include an audio file that plays in the background when the ransom note is displayed, an image file that is used to change the infected computer's wallpaper image into a ransom note, and an additional executable file, which displays the LockScreen and provides the means to decrypt the files when the victim enters the correct password. In the case of the Serpico Ransomware, the following files have been observed in attacks:
C:\Users\User_name\the Serpico\bg.jpg
C:\Users\User_name\the Serpico\key.pkm
C:\Users\User_name\the Serpico\the Serpico.exe
C:\Users\User_name\the Serpico\sound.wav
C:\Users\User_name\the Serpico\total.pkm
C:\Users\User_name\Desktop\MotoxUnlocker.exe
During its attack, the Serpico Ransomware will encrypt the following file types:
.3ds, .7z, .acbl, .all, .backup, .bak, .bmp, .bz2, .cab, .cdr, .cer, .cpr, .crt, .cs, .csv, .dat, .db, .dbf, .der, .doc, .docx, .dwg, .eps, .gif, .ibd, .ibz, .iso, .jpeg, .jpg, .mdb, .mdf, .myd, .pdf, .php, .png, .ppt, .pptx, .psb, .pst, .rar, .rns, .s3db, .sql, .sqlite, .sqlitedb, .tar, .txt, .xls, .xlsx, .xlt, .xltx, .xml, .zip.
The full text of the Serpico Ransomware ransom note reads:
SVI VAŠI FAJLOVI SU ZAKUUČANI!
Svi važni fajlovi na vašem kompjuteru su zaključani i nemoguće je razbiti enkripciju. NEMOGUĆE JE RAZBITI CryptoLocker.
Ako želite fajlove natrag javite se na mail:
motox2016@mail2tor.com
NAPOMENA:
Nemojte brisati ovaj program jer će biti potreban da bi vratili fajlove. Dobit ćete na mail upute i ključ koji ćete unijeti i svi fajlovi će biti vraćeni. Vrlo jednostavno, samo se javite na mail i dogovorimo se oko povratka fajlove.
Ako pokušate očistit ovaj program ili sami nešto popraviti moguće je da zauvijek oštetite i izgubite podatke zato je najbolje rješenje da se javite.
OTKUPNINA ZA SVE VAŠE FAJLOVE I TRAJNU ZAŠTITU OD SLIČNIH PROVALA JE SAMO 50€. JAVITE SE NA MAIL.
SpyHunter Detects & Remove Serpico Ransomware
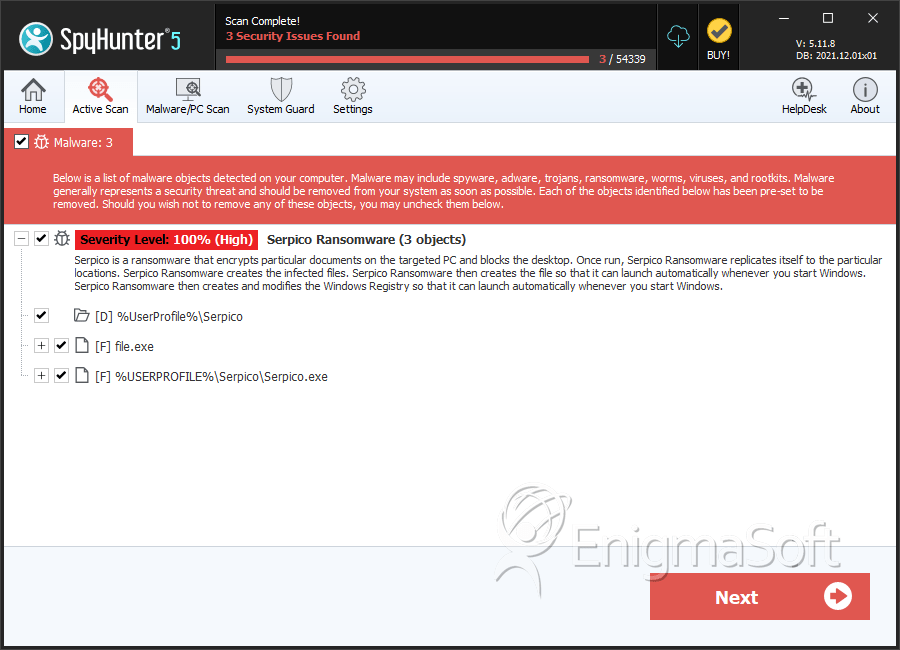
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 829f047ee3ff90e81ad056eb5ba4303c | 0 |
| 2. | Serpico.exe | 20791a1eb2b03a211f48e33ef39f97c6 | 0 |
Directories
Serpico Ransomware may create the following directory or directories:
| %UserProfile%\Serpico |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.