Petya Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 16,464 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 198 |
| First Seen: | March 25, 2016 |
| Last Seen: | November 20, 2025 |
| OS(es) Affected: | Windows |
The Petya Ransomware is used to take over the victims' computers, encrypting their files and then demanding the payment of a ransom to restore the affected files. The Petya Ransomware is just one of countless ransomware attacks that have appeared in 2016 so far. There are diverse reasons for the rise in ransomware infections like the Petya Ransomware. Some of these include the release of TeslaCrypt 3.0, which fixed a bug that allowed malware researchers to create a decryption utility, and the rise of the RaaS (Ransomware as a Service) industry, which allows fraudsters to create and deliver ransomware threats easily. The Petya Ransomware presents a real threat to a computer user, making the encrypted files inaccessible until the victim pays the ransom. In the best of cases, the victims of the Petya Ransomware can restore their files from a backup after wiping the affected hard drive completely. Because of this, the best protection against the Petya Ransomware and similar threats is always to maintain reliable backups of all files.
Table of Contents
How can You be Attacked by the Petya Ransomware and Similar Encryption Ransomware Trojans
It is not hard to predict how the Petya Ransomware attack works; most ransomware Trojans follow the same basic strategy (and in many cases, share a majority of their codes). The Petya Ransomware may be delivered using corrupted email messages containing embedded links or compromised email attachments. When computer users open these attached files, the Petya Ransomware runs in the background, scanning the victim's hard drive in search for any files with extensions matching a list of file extensions contained in its configuration files. By only targeting a specific set of file extensions, threats like the Petya Ransomware can encrypt the victim's files but still allow the affected computer to continue functioning and display the Petya Ransomware's ransom note. The following are some examples of file formats that the Petya Ransomware and similar ransomware threats target (new file extensions may be added to this list in each new update):
.7z; .rar; .m4a; .wma; .avi; .wmv; .csv; .d3dbsp; .sc2save; .sie; .sum; .ibank; .t13; .t12; .qdf; .gdb; .tax; .pkpass; .bc6; .bc7; .bkp; .qic; .bkf; .sidn; .sidd; .mddata; .itl; .itdb; .icxs; .hvpl; .hplg; .hkdb; .mdbackup; .syncdb; .gho; .cas; .svg; .map; .wmo; .itm; .sb; .fos; .mcgame; .vdf; .ztmp; .sis; .sid; .ncf; .menu; .layout; .dmp; .blob; .esm; .001; .vtf; .dazip; .fpk; .mlx; .kf; .iwd; .vpk; .tor; .psk; .rim; .w3x; .fsh; .ntl; .arch00; .lvl; .snx; .cfr; .ff; .vpp_pc; .lrf; .m2; .mcmeta; .vfs0; .mpqge; .kdb; .db0; .DayZProfile; .rofl; .hkx; .bar; .upk; .das; .iwi; .litemod; .asset; .forge; .ltx; .bsa; .apk; .re4; .sav; .lbf; .slm; .bik; .epk; .rgss3a; .pak; .big; .unity3d; .wotreplay; .xxx; .desc; .py; .m3u; .flv; .js; .css; .rb; .png; .jpeg; .txt; .p7c; .p7b; .p12; .pfx; .pem; .crt; .cer; .der; .x3f; .srw; .pef; .ptx; .r3d; .rw2; .rwl; .raw; .raf; .orf; .nrw; .mrwref; .mef; .erf; .kdc; .dcr; .cr2; .crw; .bay; .sr2; .srf; .arw; .3fr; .dng; .jpeg; .jpg; .cdr; .indd; .ai; .eps; .pdf; .pdd; .psd; .dbfv; .mdf; .wb2; .rtf; .wpd; .dxg; .xf; .dwg; .pst; .accdb; .mdb; .pptm; .pptx; .ppt; .xlk; .xlsb; .xlsm; .xlsx; .xls; .wps; .docm; .docx; .doc; .odb; .odc; .odm; .odp; .ods; .odt.
The Petya Ransomware searches for the above files and then encrypts them using an AES encryption algorithm (in its ransom message, the Petya Ransomware claims that it has used 'military grade' encryption to make it sound scarier). The Petya Ransomware delivers a variety of ransom notes in the form of dropped image, text and HTML files. The Petya Ransomware also displays pop-up messages, redirects the affected Web browser to a ransom note Web page, and changes the victim's Desktop image into the ransom note. The ransom note alerts the victims about the attack and instructs them to visit a certain Darknet website to carry out the payment through anonymous methods such as BitCoin or PaySafeCard. PC security analysts advise computer users to avoid paying the Petya Ransomware's ransom since this allows the people responsible for the Petya Ransomware to finance their illicit activities and continue producing these threats.
SpyHunter Detects & Remove Petya Ransomware
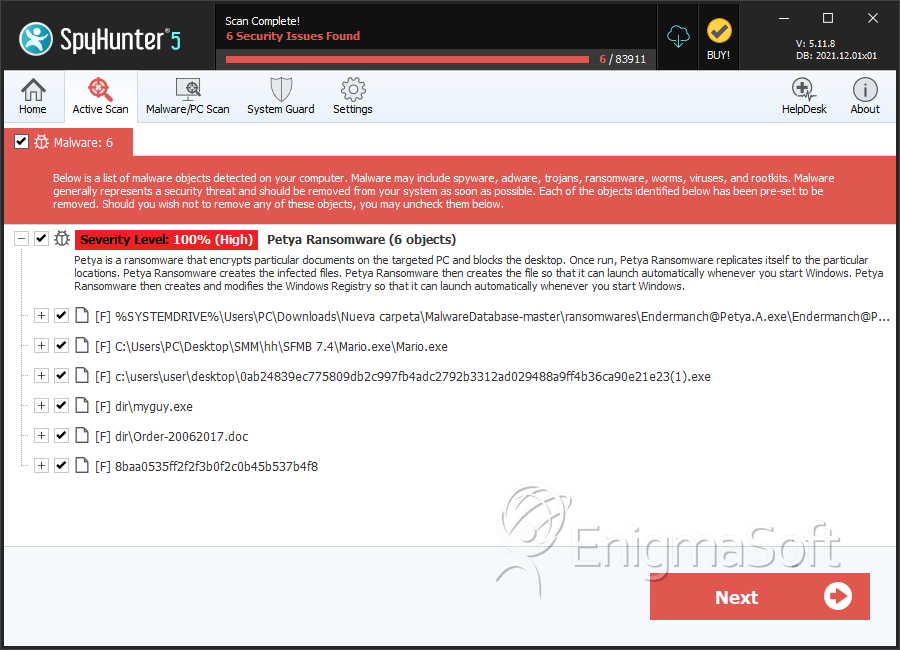
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Endermanch@Petya.A.exe | af2379cc4d607a45ac44d62135fb7015 | 88 |
| 2. | Mario.exe | 71b6a493388e7d0b40c83ce903bc6b04 | 38 |
| 3. | myguy.exe | a1d5895f85751dfe67d19cccb51b051a | 1 |
| 4. | 0ab24839ec775809db2c997fb4adc2792b3312ad029488a9ff4b36ca90e21e23(1).exe | 16a2fd266cbf9d88fb359c82e9ff5bb3 | 1 |
| 5. | Order-20062017.doc | 415fe69bf32634ca98fa07633f4118e1 | 0 |
| 6. | 8baa0535ff2f2f3b0f2c0b45b537b4f8 | 8baa0535ff2f2f3b0f2c0b45b537b4f8 | 0 |