Oled Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 19 |
| First Seen: | May 31, 2017 |
| OS(es) Affected: | Windows |
The Oled Ransomware is a ransomware Trojan that, coincidentally, has the same name as diodes used in modern televisions and other technology. There is little to differentiate the Oled Ransomware from the many other encryption ransomware Trojans that are being used to carry out attacks against computer users currently. The Oled Ransomware will encrypt the victim's files and then add the extension '.oled' to the affected files to mark them. Once a file is encrypted by the Oled Ransomware attack, it becomes unreadable. The main way in which the Oled Ransomware may be distributed is by appending it to email messages as an attachment, which may take advantage of vulnerabilities in macros and scripts to execute a corrupted code and download and install the Oled Ransomware onto the victim's computer.
Table of Contents
The Oled that Instead of Light Emits Darkness to Your Files
Unfortunately, once the files have been encrypted by the Oled Ransomware attack, they will become unrecoverable. Because of this, the best way to deal with the Oled Ransomware and other ransomware Trojans is by taking preventive measures. The Oled Ransomware will display a ransom note informing the victim of the attack, provide information on the ransom payment, and offer to decrypt three files for free (as long as they are small and contain no 'important' information). Security experts do not recommend contacting the con artists at all since in many cases this can lead to additional infections and other tactics. The following is the full text of the Oled Ransomware ransom note:
'Your ID:
*****
All your files have been encrypted due to a security problem with your PC.
If you want to restore them, write us to the e-mail: black.mirror@qq.com
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
FREE DECRYPTION AS GUARANTEE
Before paying you can send to us up to 3 files for free decryption.
Please note that files must NOT contain valuable information and their total size must be less than 5Mb
How to obtain Bitcoins
The easiest way to buy bitcoin is LocalBitcoins site.
You have to register, click Buy bitcoins and select the seller by payment method and price https://localbitcoins.com/buy_bitcoins
Attention!
Do not rename or move encrypted files - this may compromise the integrity of the decryption process
Do not try to decrypt your data using third party software, it may cause permanent data loss.'
How the Oled Ransomware Attack will Affect Your Files
The Oled Ransomware belongs to the BTCWare family of ransomware, a known ransomware Trojan family that tends to demand very high ransoms. The Oled Ransomware's ransom note is contained in a text file named 'DECRYPTION.txt' that is dropped on the infected computer. The Oled Ransomware will use a combination of the AES and RSA encryptions to make the victim's files completely inaccessible and demand its ransom payment in BitCoins, which allows the con artists to remain anonymous. Email messages being used to deliver the Oled Ransomware may take the form of emails that resemble communications from legitimate companies, such as PayPal. They may often include an embedded link or file attachment and use social engineering techniques to convince inexperienced computer users into downloading and installing the Oled Ransomware onto their computers.
Dealing with the Oled Ransomware
Although the Oled Ransomware infection itself can be removed with the help of a reliable security program that is fully up-to-date, once the Oled Ransomware has encrypted the files, they will not be recoverable without access to the decryption key (this is what makes these threats so scary and effective). Because of this, the best preventive measure computer users can take, is to have file backups of all files, storing them on the cloud or an external memory device. Having the ability to restore the files from a backup negates the Oled Ransomware's attack completely.
SpyHunter Detects & Remove Oled Ransomware
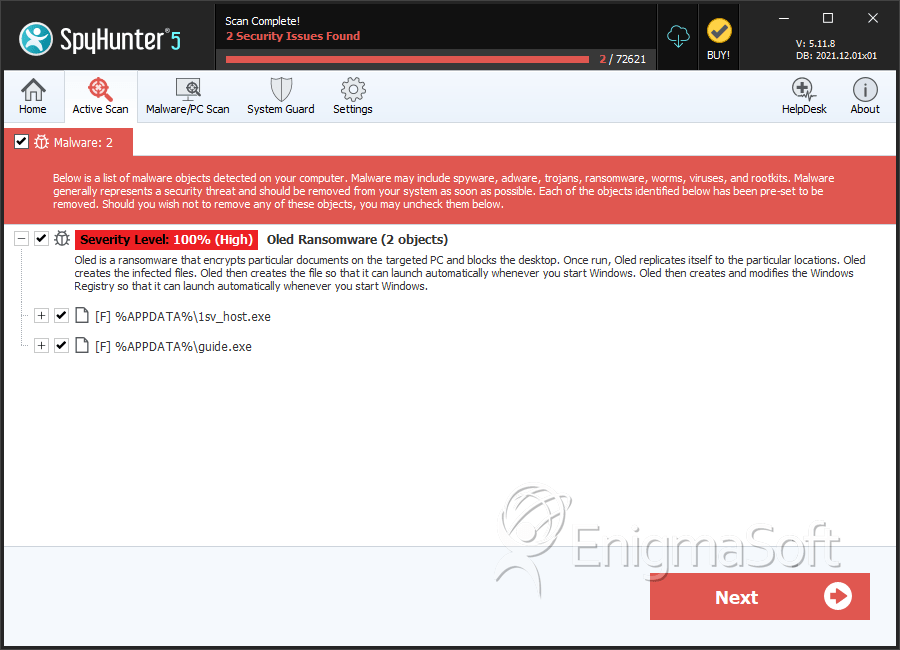
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 1sv_host.exe | 4e1c53e8c46a365a3d7ad8d80c2aab27 | 10 |
| 2. | guide.exe | a9b86e4c328f29548ea1fd4a8e794602 | 9 |

