BTCWare Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 43,684 |
| First Seen: | March 27, 2017 |
| Last Seen: | March 1, 2022 |
| OS(es) Affected: | Windows |
The BTCWare Ransomware is a ransomware family that has been highly active since April of 2017. Several variants in the BTCWare Ransomware family have been released in 2017, most using similar ransom demand messages and appending similar extensions to the encrypted files. The BTCWare Ransomware variants may ask for different ransoms, although most average approximately $500 USD in BitCoin. They also have been branded in different ways. Fortunately, PC security researchers have reported on the release of a decryptor application that can help computer users recover from the BTCWare Ransomware attacks.
Table of Contents
Is the BTCWare Ransomware’s Name a Tribute to the Currency Favored by Extortionists?
The BTCWare Ransomware carries out a typical ransomware attack, encrypting the victims' files using a strong encryption algorithm and then demanding a ransom payment from the victim in exchange for the decryption key necessary to recover the affected files. Up until now, the only solution for computer users was to restore the affected files from a backup copy. Fortunately, a decryptor released in late May can help computer users recover their files from most of the BTCWare Ransomware variants (although it is expected that the BTCWare Ransomware's developers will change their tactics to release new variants that are not affected by this decryptor). The BTCWare Ransomware decryptor was developed after the BTCWare Ransomware master key was released on computer security forums (perhaps by one of the BTCWare Ransomware developers or one of its competitors looking to sabotage the con artists' efforts). The BTCWare Ransomware is quite active currently, with new variants released almost daily since March 2017. The rate of the BTCWare Ransomware infections made it comparable to better-known ransomware Trojans such as Locky.
Recovering Your Files from a BTCWare Ransomware Attack
The decryptor released by PC security researchers can help computer users recover their files if the following file extensions have been added to them:
- .[< email address >].btcware
- .[< email address >].cryptobyte
- .[< email address >].cryptowin
- .[< email address >].theva
This decryption program may help computer users recover from other BTCWare Ransomware variants. PC security researchers are updating this decryptor to help computer users deal with newer BTCWare Ransomware variants as they are released. In May a variant known as Onyonware, which used the '.onyon' and other extensions was released, and this decryptor is being updated to include these variants. It is possible that the people responsible for the BTCWare Ransomware attacks, however, have already moved onto new variants of this ransomware threat.
The BTCWare Ransomware Attack is Very Common
The BTCWare Ransomware infection is typical of these encryption ransomware attacks. The BTCWare Ransomware ransom note tends to be contained in files with names such as '#_HOW_TO_FIX_!.hta.htm' or '!#_RESTORE_FILES_#!.inf' and may contain a variant of the following message:
'[WHAT HAPPENED]
Your important files produced on this computer have been encrypted due a security problem
If you want to restore them, write us to the e-mail: look1213@protonmail.com
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
[FREE DECRYPTION AS GUARANTEE]
Before paying you can send to us up to 3 files for free decryption.
Please note that files must NOT contain valuable information
and their total size must be less than 1Mb
[HOW TO OBTAIN BITCOINS]
The easiest way to buy bitcoin is LocalBitcoins site.
You have to register, click Buy bitcoins and select the seller
by payment method and price
https://localbitcoins.com/buy_bitcoins
[ATTENTION]
Do not rename encrypted files
Do not try to decrypt your data using third party software, it may cause permanent data loss
If you not write on e-mail in 36 hours - your key has been deleted and you cant decrypt your files
Your ID: -'
When the victims of the BTCWare Ransomware attack visit the BTCWare Ransomware payment portal or website, they may be greeted with the following instructions:
'Recovery files. Telegram: @decryps
To decrypt files, you will have to pay 0.5 BTC
1. You should register Blockchain wallet
2. Buy bitcoins to your wallet.
3. Send 0.5 BTC to Bitcoin address: -
4. Enter you transaction ID: -
5. Press Win+R, type cmd and press Enter In appeared console:
1) Enter cd %appdata%
2) Enter biz net.exe -d your_decrypt_key and wait for decryption...
6. Finish. All the files decrypted.'
SpyHunter Detects & Remove BTCWare Ransomware
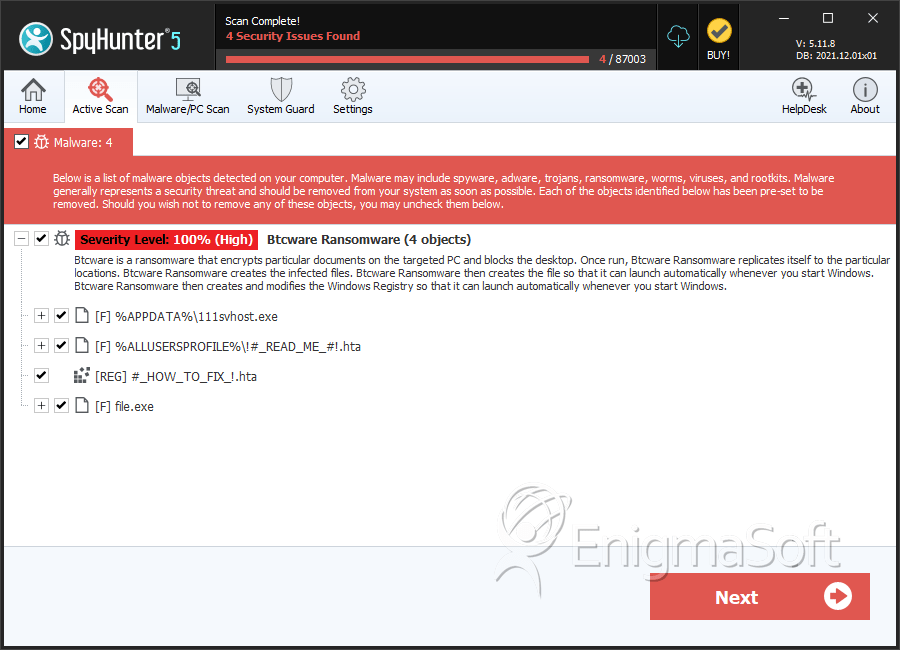
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | !#_READ_ME_#!.hta | 2075a6619aae0bf45bb9515988faf049 | 476 |
| 2. | !#_READ_ME_#!.hta | ec00a7b44e559c330eb2db44cb3b1519 | 155 |
| 3. | file.exe | 497c5a51d631d1cd79d5eae21eb2cb92 | 96 |
| 4. | !#_READ_ME_#!.hta | 4380fd010cddb70bc8abb0a755b6838b | 83 |
| 5. | !#_READ_ME_#!.hta | 209ed64326cef0d46b80e755af578827 | 54 |
| 6. | !#_READ_ME_#!.hta | d75f0bd5e01fc43c03278e735151da04 | 29 |
| 7. | !#_READ_ME_#!.hta | eab4241cc0da39462dd90eb748062068 | 27 |
| 8. | !#_READ_ME_#!.hta | e7d0a7d49a89452704def40486f32a32 | 24 |
| 9. | !#_READ_ME_#!.hta | 3bd2dea24d120cd624e84c41363706d5 | 19 |
| 10. | !#_READ_ME_#!.hta | 831b9e82c93ea2fe4f53a6272cf506a1 | 19 |
| 11. | 111svhost.exe | d0859aea3795ab294366ca5b5d3ef6cb | 17 |
| 12. | !#_READ_ME_#!.hta | cd682d02be86649571bf03bd1e69d9d2 | 15 |
| 13. | !#_READ_ME_#!.hta | 0a13b8f171275dc65e883fef727fbf77 | 15 |
| 14. | !#_READ_ME_#!.hta | f3c7da1139678cad16b2cd8b24a0be2f | 11 |
| 15. | !#_READ_ME_#!.hta | 059d4542b27a3f9b1d769a93c5b29127 | 8 |
| 16. | !#_READ_ME_#!.hta | 136ea58e7cb4b33598f3038583bfeb8a | 8 |
| 17. | !#_READ_ME_#!.hta | 10eb12c4749d83897bfcc2cb028fcc00 | 6 |
| 18. | !#_READ_ME_#!.hta | b0d2c6949a5ccb089af6f18c4a3fb8f8 | 6 |
| 19. | !#_READ_ME_#!.hta | b6c3fd2a886c74ab9cd0d4b0673d1927 | 5 |
| 20. | !#_READ_ME_#!.hta | 94ff7e538acb23d5ac598fbb2a39abf3 | 5 |
| 21. | !#_READ_ME_#!.hta | d8509e93dfa30c8d41f29c123b2e444a | 4 |
| 22. | !#_READ_ME_#!.hta | fa42610a9e8106df8b9467bf7195a112 | 3 |
| 23. | !#_READ_ME_#!.hta | a31ddee91c96512da46e2c2f39ebd7cc | 2 |
| 24. | !#_READ_ME_#!.hta | 0a0c688ead244f48a5731cec6ebf983d | 2 |
| 25. | !#_READ_ME_#!.hta | acb7e62659588fdbaf9f8e272343ab74 | 1 |
| 26. | !#_READ_ME_#!.hta | cab3262ed4e3649509aa5a6058200276 | 1 |
| 27. | !#_READ_ME_#!.hta | db5963ccd4c65e93e342781676c53bdb | 1 |
| 28. | file.exe | 2c1a9fff423a7afd1b25d1b4c7c5ae3c | 0 |