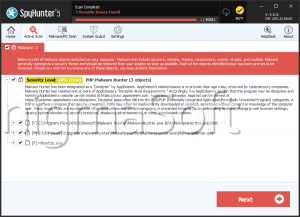
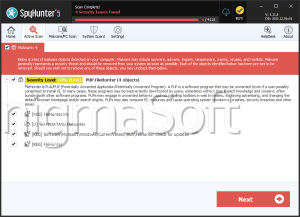
HUNTER Ransomware
Cybersecurity analysts have identified a new threat known as the HUNTER Ransomware while examining potential malware risks. This particular strain of threatening software possesses the capability to encrypt a wide range of file types, rendering them inaccessible and unusable for the victims. Moreover, HUNTER ransomware modifies the original filenames of the encrypted files and presents two ransom notes labeled 'info.txt' and 'info.hta' to the affected users.
Furthermore, the HUNTER Ransomware alters the filenames by appending the victim's unique ID, an email address, and the '.HUNTER' extension, thereby transforming filenames such as '1.doc' into '1.doc.id[9ECFA74E-3345].[Hunter-X@tuta.io].HUNTER' and '2.pdf' into '2.png.id[9ECFA74E-3345].[Hunter-X@tuta.io].HUNTER,' and so forth. Additionally, cybersecurity experts have warned that HUNTER belongs to the Phobos Ransomware family, indicating its association with a group of ransomware variants known for their sophisticated encryption techniques and extortion tactics.
The HUNTER Ransomware Seeks to Extort Victims for Money by Taking Data Hostage
The ransom note issued by the HUNTER Ransomware serves as a notification to its victims, informing them of the encryption of all their files, attributing it to a security flaw within their PC system. It provides explicit instructions for contacting the attackers via an email address (hunter-x@tuta.io), specifying the inclusion of a unique ID in the subject line to facilitate communication. In the event of non-response within a 24-hour timeframe, an alternative contact method is suggested through a Telegram account (@Online7_365).
Furthermore, the note outlines the payment demands, stipulating Bitcoin transactions for decryption services, with the ransom amount varying based on the promptness of victim contact. As a gesture of assurance, the attackers offer to decrypt up to three files for free, provided they meet certain criteria, such as being under 4 MB in size and lacking significant data.
Moreover, the note emphasizes caution, advising against renaming encrypted files or attempting decryption using unauthorized software to prevent irreversible data loss or falling prey to fraudulent schemes.
The HUNTER Ransomware poses a multifaceted threat by not only encrypting files but also disabling firewalls, leaving systems vulnerable to unsafe exploits. Additionally, it actively eliminates the Shadow Volume Copies, impeding potential file recovery endeavors. Furthermore, HUNTER demonstrates the ability to gather location data and employ persistence mechanisms, strategically avoiding certain system areas to evade detection.
How to Boost Your Defense against Malware and Ransomware Threats?
Users can enhance their defenses against malware and ransomware threats through a combination of proactive measures and security best practices:
- Keep software up to date: Regularly updating operating systems, applications, and antivirus software helps patch security vulnerabilities that malware often exploits. Enable automatic updates whenever possible.
- Install reputable security software: Install and regularly update reputable anti-malware software to detect and remove threats. Additionally, consider using security solutions that offer features like behavior monitoring and real-time scanning for enhanced protection.
- Exercise caution when dealing with links and email attachments: Be cautious when dealing with email attachments or links, especially if they are from unfamiliar or suspicious sources. Verify the sender's identity and be wary of unexpected emails, especially those urging urgent action or containing unusual requests.
- Enable firewall protection: Activate firewalls on both network routers and individual devices to monitor and control incoming and outgoing traffic, preventing unauthorized access and blocking malicious connections.
- Use strong, unique passwords: Create strong, unique passwords for each account and enable multi-factor authentication (MFA) when possible to maximize your security. Think about the advantages of using a reputable password manager store and manage passwords to securely.
- Regularly backup data: Implement a regular backup routine to ensure that essential data is securely stored and can be recovered in the event of a ransomware attack or data loss incident. Store backups in a separate network location or offline to prevent them from being compromised by malware.
- Educate users: Educate yourself and other users about common malware and ransomware tactics, such as phishing scams and social engineering techniques. Train employees to recognize suspicious behavior and report potential security threats promptly.
- Limit user privileges: Restrict user privileges to only those necessary for performing job functions to minimize the impact of malware attacks. Implant the principle of least privilege to reduce the likelihood of malware spreading across systems.
- Stay informed: Stay informed about the latest malware and ransomware threats by following reputable cybersecurity news sources and advisories. Being aware of emerging threats can help users proactively adjust their security strategies to better protect against evolving risks.
The ransom note generated by the HUNTER Ransomware as a pop-up window is:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail Hunter-X@tuta.io
Write this ID in the title of your message -
If you do not receive a response within 24 hours, please contact us by Telegram.org account: @Online7_365
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 3 files for free decryption. The total size of files must be less than 4Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
hxxps://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
hxxp://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
The text file of HUNTER Ransomware delivers the following instructions from the attackers:
!!!All of your files are encrypted!!!
To decrypt them send e-mail to this address: Hunter-X@tuta.io.
If we don't answer in 24h, send messge to telegram: @Online7_365