FakeXPA
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1,299 |
| First Seen: | November 30, 2010 |
| Last Seen: | April 6, 2024 |
| OS(es) Affected: | Windows |
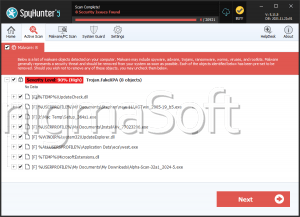
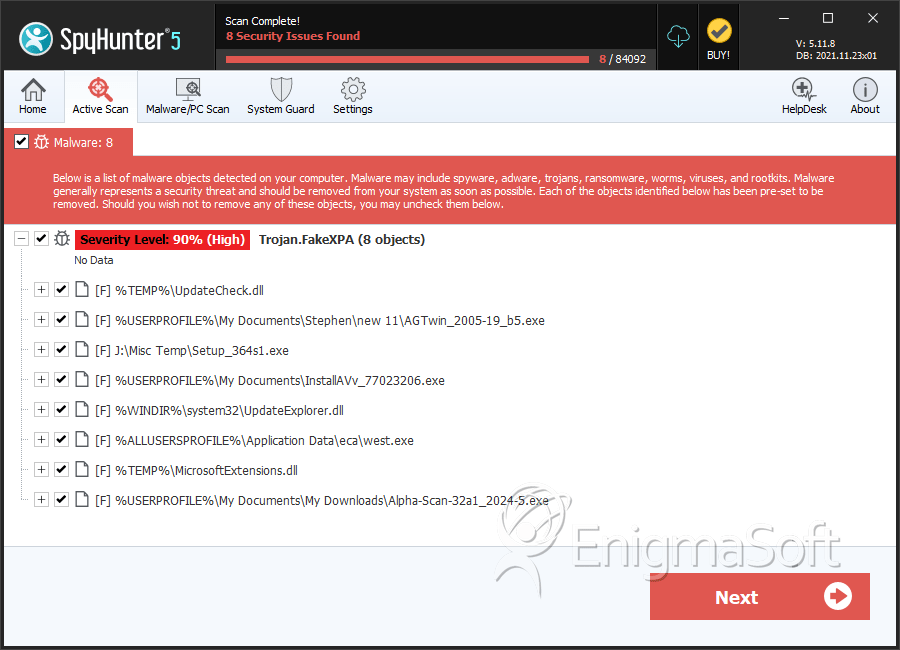
FakeXPA is a family of rogue security applications that have been detected in the wild since 2008. Some examples of rogue security programs that belong to the FakeXPA family of fake security applications include Antivirus 2009, 2010 and 360, Total Security 2009 and 2011, Green AV, Alpha AV, Cyber Security and fake versions of E-Set and AVG anti-virus programs. ESG security researchers consider that any fake security programs on your computer system belonging to the FakeXPA family of rogue security programs pose a severe threat to your computer system's security and should be removed immediately with a real, legitimate anti-malware application.
Table of Contents
Understanding How Fake Security Programs in the FakeXPA Family Infect Your System
Programs in the FakeXPA family of malware claim to scan the victim's computer system and display multiple fake error messages claiming that the victim's computer has fallen victim to a virus attack. These fake security programs claim that they can only remove these imaginary threats if the victims pay for a 'full version' of the rogue security program in question. Malware in the FakeXPA family are characterized because they imitate Windows Security Center closely. According to ESG security researchers, some malware in the FakeXPA family has been known to connect to a remote server and download the Alureon Trojan and rootkit and install it onto the victim's computer. These distributions of FakeXPA rogue security programs are particularly dangerous and may require a specialized anti-rootkit tool to be removed.
How FakeXPA Rogue Security Programs are Installed on the Victim’s Computer System
The FakeXPA installer will usually be associated with additional malware, which will be installed on the same directory as the rogue security program itself. This malware infection will usually take the form of an executable file with the EXE extension (such as 'win.exe', for example). As part of their payload, malware belonging to the FakeXPA family will overwrite any security programs it finds on the victim's computer. They will check the victim's computer's Windows Registry in order to detect common security programs, particularly AVG, Kaspersky, Norton, McAfee and Norton. Then, these dangerous rogue security programs will overwrite portions of executable files corresponding to these legitimate security applications. This corrupts them, disabling them completely. Once the victim's security software has been disabled, FakeXPA has free rein to attack the victim's computer and cause browser redirects, block access to the victim's files and carry out its malicious scam.
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| AVG | Downloader.Generic8.BSRD |
| Fortinet | W32/PackBredolab.C!tr |
| AhnLab-V3 | Win-Downloader/Zlob.173056 |
| eTrust-Vet | Win32/FakeXP.J |
| DrWeb | Trojan.Packed.19697 |
| F-Secure | Trojan:W32/XPAntivirus.gen!L |
| Sophos | Troj/FakeAv-AAQ |
| BitDefender | Trojan.Generic.2503965 |
| Kaspersky | Trojan-Downloader.Win32.FraudLoad.fmh |
| Avast | Win32:MalOb-CA [Cryp] |
| Symantec | Trojan.FakeAV!gen5 |
| F-Prot | W32/FakeAV.MN |
| NOD32 | Win32/Adware.Antivirus2009.AA |
| McAfee | FakeAlert-IS |
| CAT-QuickHeal | TrojanDownloader.FraudLoad.fm |
SpyHunter Detects & Remove FakeXPA
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | iesafemode.exe | f578ab4b5bc76e71a209a0a795618c20 | 46 |
| 2. | iesafemode.exe | 222ce2263b8e92c61284bb1b4c704ae5 | 16 |
| 3. | iesafemode.exe | 9967e5956005fc377605304e60ca4d78 | 15 |
| 4. | iesafemode.exe | c2089ab47353d142b7d1ea4b3f49562e | 15 |
| 5. | iesafemode.exe | 18f1d1761c0a70b641157ceb07a8f0b2 | 13 |
| 6. | e-set.exe | ca2326019dffbf70ba05f92dba9276a5 | 13 |
| 7. | iesafemode.exe | 0e8f4807cad312f597cfe7dbcf2261ad | 12 |
| 8. | iesafemode.exe | 23ef8ad8894754b6b031ef59d024a8dd | 11 |
| 9. | setup.exe | b0677ddcd6e67d716e8a2315952bea94 | 11 |
| 10. | iesafemode.exe | c880fa52d8ec65e792fe694212c29eed | 10 |
| 11. | iesafemode.exe | 8a8d987f61778c0b60b30b6f991a5f52 | 10 |
| 12. | iesafemode.exe | 4fb3fa33ae7c845218cbe54d13c9bb9f | 8 |
| 13. | Soft_95.exe | 3734185c9e1bdd05bb9b077ee4f32878 | 8 |
| 14. | iesafemode.exe | cac1918e12e1ef7c8418b2904fb179ef | 7 |
| 15. | iesafemode.exe | 556e6129ab4e0a86a0cfc1d3d425597c | 6 |
| 16. | avg.exe | d568107809815871a46169f63ac52e0c | 5 |
| 17. | setup.exe | 1694f0522272a4e732185c18aae9e3ba | 4 |
| 18. | iesafemode.exe | 22a323b50a890f899c4800cf921ec2dc | 3 |
| 19. | iesafemode.exe | ff0b1b68924b4ef31e11ec439602a266 | 3 |
| 20. | e-set.exe | fdcb6a236f1fe4f464ff6a9e0267d726 | 2 |
| 21. | e-set.exe | 1949f8303d9826221c04518bb3256056 | 2 |
| 22. | wdn.exe | f9f1dcfae3e975440a8e28ab751b0397 | 2 |
| 23. | powersecure_2053_ibr8.exe | 730f23c83957ec25e8b4e0a04420d993 | 1 |
| 24. | avg.exe | 4865d43bb53fd0aba54d831328bb7c01 | 1 |
| 25. | avg.exe | 1f79908e06cd00466b97f086b7cead16 | 1 |
| 26. | e-set.exe | 2830867abf0a4585f68bda47b8e4a107 | 1 |
| 27. | msiexecs.exe | de8634ff52b49a1c0ebb36b1ffa2cf43 | 1 |