XUY Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | November 15, 2018 |
| OS(es) Affected: | Windows |
The XUY Ransomware is an encryption ransomware Trojan that is used to extort computer users. The XUY Ransomware uses a strong encryption algorithm to take the victim's files hostage like most encryption ransomware Trojans and then demands a ransom payment in exchange for the decryption key required to restore the affected files. The XUY Ransomware's creators demand a ransom of €400 EUR to restore the affected files. Security experts counsel computer users to refrain from paying the XUY Ransomware ransom or contacting the criminals responsible for this attack. Instead, computer users should take preemptive measures to ensure that their data is safe from this and other, similar attacks.
Table of Contents
How the XUY Ransomware Attack Works
Once the XUY Ransomware is installed, it uses a strong encryption algorithm to encrypt the victim's files. The XUY Ransomware is typically delivered to the victim's computer via corrupted spam email attachments. The XUY Ransomware is designed to target the user-generated files in this attack, marking each file that is compromised by adding the file extension '.xuy' to the affected file's name. The following are examples of the files that the XUY Ransomware and similar threats target in these infections:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
The XUY Ransomware changes the affected computer's desktop image and displays a ransom note via an HTA application. The XUY Ransomware ransom note simply states that the victim should contact the criminals via the email address 'luxenburg@cock.li.' Experts advise PC users to refrain from doing this or contacting the criminals responsible for the XUY Ransomware attack. Contacting these criminals or paying the ransom only serves to expose computer users to additional infections and allows the criminals responsible for the XUY Ransomware attack to continue creating these threats and profiting off of new victims. Instead, they should take action to protect their PCs from threats like the XUY Ransomware.
Protecting Your PC from the XUY Ransomware and Similar Threats
The best protection against the XUY Ransomware is to have file backups saved on the cloud or an external device. Having file backups ensures that computer users can recover any files encrypted by the XUY Ransomware without having to cooperate with the criminals responsible for the attack. Unfortunately, threats like the XUY Ransomware use an encryption kind that is quite strong, and it may not be possible for computer users to restore their data without the encryption key used by the XUY Ransomware currently. Apart from file backups, PC security researchers advise computer users to use a security program to protect their computer from the XUY Ransomware and similar threats.
SpyHunter Detects & Remove XUY Ransomware
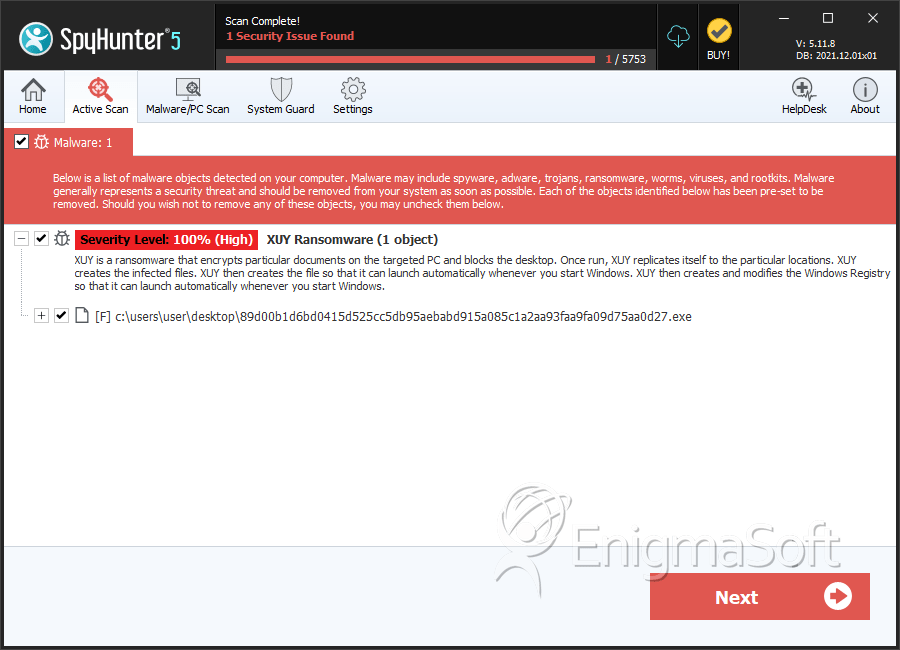
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 89d00b1d6bd0415d525cc5db95aebabd915a085c1a2aa93faa9fa09d75aa0d27.exe | 6ebecab25813a8b9eb60d8901e03137a | 4 |
