WatchDog Malware
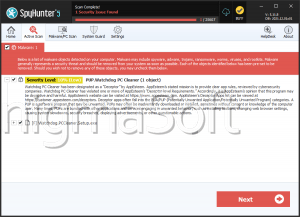
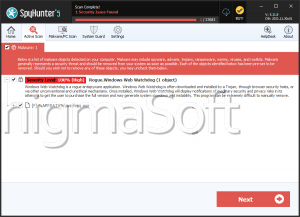
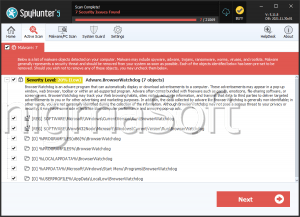
The WatchDog Malware is a cryptocurrency-mining Trojan that circulates through abusing software vulnerabilities. The WatchDog Malware hijacks Android and Windows hardware for generating Monero coins without the user's consent. Users should remove the WatchDog Malware immediately through appropriate anti-malware tools and double-check for software and password-related vulnerabilities as appropriate.
Modernized Money at the Cost of Others' Computers
After making waves in the cyber-security industry due to its impressive longevity, the WatchDog Malware is coming under focus as a recently-identified cryptocurrency-miner Trojan. The threat's campaign is at least two years old – more than much of the competition – and is compatible with Android and Windows environments. Although WatchDog Malware's goals are pedestrian, many of its features are far less so.
The WatchDog Malware generates the Monero cryptocurrency by taking over the infected system's hardware and running concealed mining processes. In this respect, it's no different from Bird Miner or MassMiner, among other examples. Structurally, it divides itself into several components:
- A variant of XMRig for mining Monero
- A process monitor that maintains WatchDog Malware's persistence
- A network-scanning component that spreads the WatchDog Malware to new targets
The distribution portion of WatchDog Malware's campaign is of greater interest to malware experts. It includes dozens of built-in exploits for breaching servers with outdated software, such as old Oracle WebLogic Server versions. Besides being better at self-distribution than comparable threats, the WatchDog Malware also is evasive impressively, as its long-term history demonstrates.
Putting Unruly Dogs Back on a Leash
Android and Windows server administrators should be cautious about possible WatchDog Malware attacks, particularly. Since its distribution model involves targeting outdated software, installing security patches, when available, should help curb much of its current circulation plans. However, there also is the possibility of attackers gaining access to passwords and other credentials during or before infection. With that information, criminals could drop additional threats and perform more attacks with little hindrance.
Most cryptocurrency-mining Trojans don't cause long-term harm to infected PCs. Still, there always is a possibility of WatchDog Malware's abusing mining routines to the point of causing hardware damage. Users should watch for symptoms such as poor performance or overheating and attend to them before replacing hardware becomes mandatory.
In light of its evasion-heavy properties – possibly, partly from its Go programming language basis – malware experts recommend users install any updates to all security services' databases when possible. When removing the WatchDog Malware through usual anti-malware tools, users also should disable network connectivity and, after disinfection, consider changing their passwords.
The WatchDog Malware is a dog with a powerful bite and not much bark along with it. As Monero continues fluctuating in its value, users can expect hackers deploying similar Trojans for plunder and cashing out at the victims' expense.