TrustNinja
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 15,682 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 6 |
| First Seen: | August 26, 2009 |
| Last Seen: | May 6, 2024 |
| OS(es) Affected: | Windows |
TrustNinja (also known as Trust Ninja) is a fake optimization tool presented as a useful program in order to gain the trust of the user. TrustNinja that is a member of the FakeSmoke family, must be installed manually, and once active, begins display fake infection results in order to trick the user into believing that the computer has been compromised. The user is then prompted to purchase the commercial version of TrustNinja in order to combat these threats or fix the various problems.
The family of TrustNinja has various members, all of them clones of TrustNinja. These members include WiniFighter, WiniShield, SaveKeep, SaveKeeper, SoftSafeness, TrustWarrior, WiniGuard, SecurityFighter, Security Soldier, SecureVeteran, Secure Warrior, Trust Cop, Safe Fighter, Trust Soldier, Virus Protector, BlockDefense, Security Soldier, SaveDefense, SystemCop.
Table of Contents
SpyHunter Detects & Remove TrustNinja
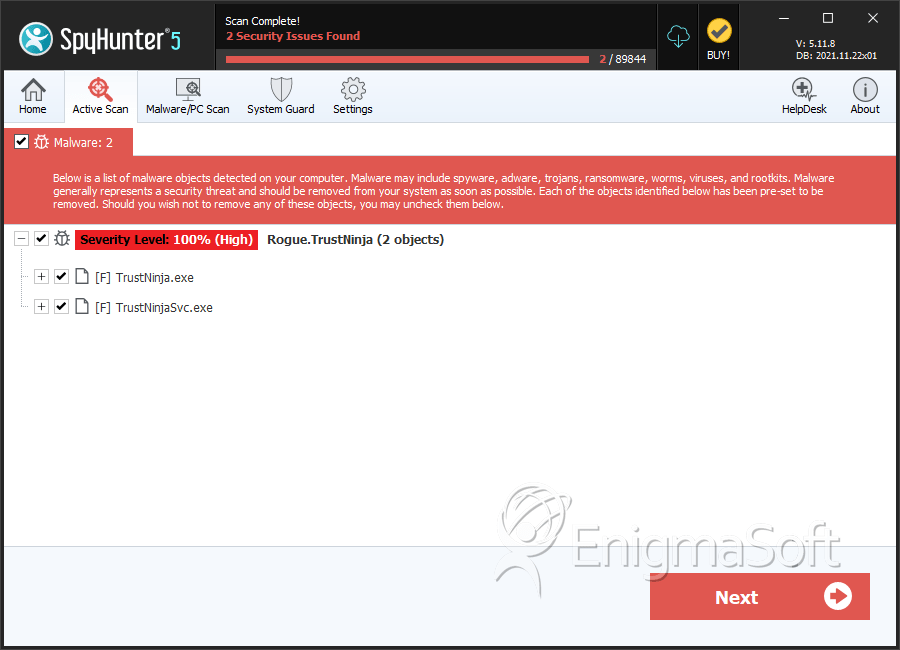
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | c9f6764aede6c4384af2d50bf00e6da8.exe | c9f6764aede6c4384af2d50bf00e6da8 | 3 |
| 2. | %ProgramFiles%\TrustNinja Software\TrustNinja\uninstall.exe | ||
| 3. | %ProgramFiles%\TrustNinja Software\TrustNinja\TrustNinjaSvc.exe | ||
| 4. | %Temp%\nsm2.tmp\nsSCM.dll | ||
| 5. | %ProgramFiles%\TrustNinja Software\TrustNinja\TrustNinja.exe | ||
| 6. | %Temp%\nsm2.tmp\nsProcess.dll | ||
| 7. | %ProgramFiles%\TrustNinja Software\TrustNinja\data.bin | ||
| 8. | %Documents and Settings%\All Users\Start Menu\Programs\TrustNinja\2 Homepage.lnk | ||
| 9. | TrustNinja | ||
| 10. | %ProgramFiles%\TrustNinja Software\TrustNinja | ||
| 11. | %Documents and Settings%\All Users\Start Menu\Programs\TrustNinja\1 TrustNinja.lnk | ||
| 12. | %Program Files%\TrustNinja Software | ||
| 13. | %Documents and Settings%\All Users\Desktop\TrustNinja.lnk | ||
| 14. | %ProgramFiles%\TrustNinja Software\TrustNinja\license.txt | ||
| 15. | %Documents and Settings%\All Users\Start Menu\Programs\TrustNinja\3 Uninstall.lnk | ||
| 16. | %ProgramFiles%\TrustNinja Software | ||
| 17. | TrustNinjaSvc.exe | e92f901fb0a487d9aac6ae40b8e05d56 | 0 |
Registry Details
URLs
TrustNinja may call the following URLs:
| akeoqpxcer.com |
| probanitos.com |
| trustninja.com |
