Trojan.Glupteba
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 16,984 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 14,065 |
| First Seen: | March 5, 2014 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
The Glupteba Trojan is a threat that has been known to malware researchers for a while. In previous campaigns, it appeared that the main purpose of the Glupteba Trojan is to infect as many devices it can and use them to build a botnet. Usually, botnets are used for crypto mining operations, DDoS (Distributed-Denial-of-Service) attacks, and to be rented out as a service to other shady actors online. However, the Glupteba Trojan has recently made a comeback, and its activity appears to be spiking. The Glupteba malware has returned in the shape of a Trojan dropper, which can not only serve as a gateway for more threats to be planted on the host but also can allow its operators to get almost complete control over the infected machine.
This Week In Malware Ep 13: Glupteba Cryptojacking Malware Becomes Unstoppable
Table of Contents
Propagation Method
The latest Glupteba variant is propagated via a malvertising campaign that is likely to reach users in multiple parts of the world. Furthermore, the Glupteba Trojan's payload packs a heavily obfuscated dropper that is meant to deliver additional malware - an information collector, and a weaponized exploit that targets a vulnerability in MikroTik routers.
Dropper Module
The Glupteba Trojan has a dropper module, which is used to deliver the MikroTik router exploit, as well as the info stealer. The Glupteba Trojan dropper module is written in Google's Go programming language and has the ability to detect whether it is being run in a sandbox environment or a regular system. Its code is heavily obfuscated to make it nearly impossible for anti-malware tools to detect its activity. The Glupteba dropper module also makes sure to tamper with the Windows Firewall and the Windows Defender and thus manages to bypass their security measures.
Backdoor Module
The Glupteba Trojan's backdoor module packs a wide variety of capabilities. This backdoor module can:
- Execute a Monero cryptocurrency miner module.
- Download files.
- Execute files.
- Collect files.
- Modify the Registry.
- Update its server.
- List processes.
Infostealer Module
The info stealer module of the Glupteba Dropper can collect saved login credentials from Web browsers like Google Chrome, Yandex Web and Opera. Furthermore, this module can also siphon other sensitive data to the C&C (Command & Control) servers of the attackers such as user profiles, cookies and browsing history.
It is fundamental to download and install a legitimate anti-virus software suite to keep your system safe from nasty threats like the Glupteba malware.
SpyHunter Detects & Remove Trojan.Glupteba
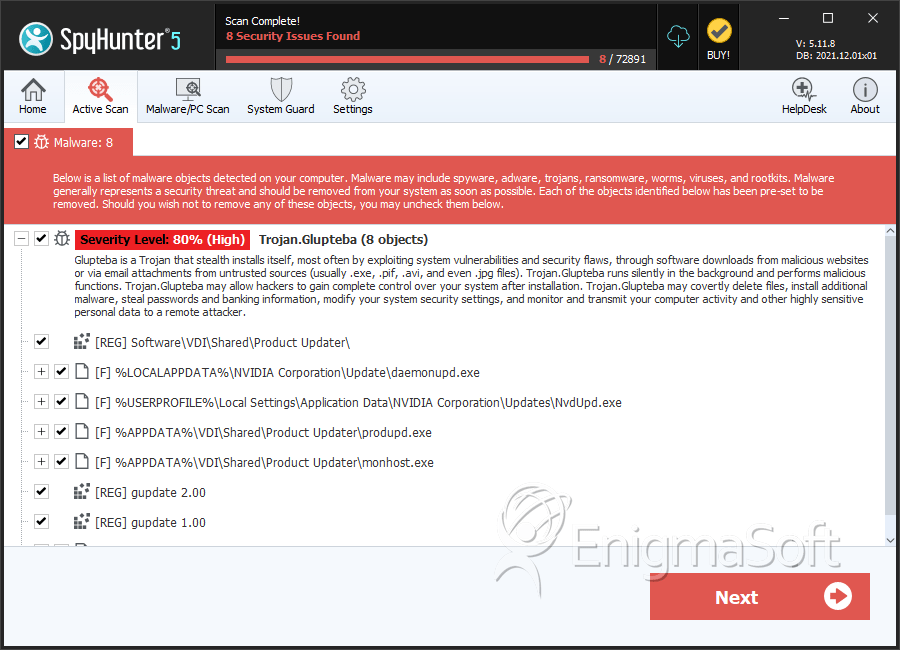
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | daemonupd.exe | ec58d901b742c3dd6814af8a7651f175 | 78 |
| 2. | gupdate.exe | 9b3d13af2e1da6541ef94dc9667e40f3 | 73 |
| 3. | NvdUpd.exe | aa94c0223583e7ed2b2fd3689abf1989 | 64 |
| 4. | monhost.exe | 34e8a05a5e5f2006ee8b143528cd1634 | 60 |
| 5. | produpd.exe | 9fd43a49ced631b92cea22a54b58a60d | 46 |
| 6. | ProductUpdater.exe | b0d63cecb620da431d521ac00f82b548 | 12 |
| 7. | winupdate.exe | 69addae65b023d9b2a0113a3029df9cb | 5 |
