ACAD/Medre.A
ACAD/Medre.A is a worm that is highly effective at what ACAD/Medre.A does: steal AutoCAD drawings. AutoCAD is a program that is essential for engineers and architects and is widely used to draw blueprints and other important documents. The ACAD/Medre.A worm has a very specific line of attack and is designed to steal these often highly-sensitive files. The ACAD/Medre.A worm can also be harmful for computer users with no relationship to AutoCAD since ACAD/Medre.A also has the ability to steal email information. Basically, the ACAD/Medre.A worm has a virus-like capability to infect AutoCAD files in order to spread itself from one computer to another (ensuring that its victims will have some relationship with AutoCAD). ESG security researchers strongly advise to be on the alert for attacks similar to the ACAD/Medre.A worm if you use AutoCAD. Although this is certainly a very specific niche, it can be highly profitable for criminals due to its potential for industrial espionage.
Table of Contents
ACAD/Medre.A Disguises Itself as an AutoCAD File in Order to Steal Data
The ACAD/Medre.A worm and similar malware have been associated with state-sponsored malware attacks and high-level malware creators interested in industrial sabotage and espionage. The ACAD/Medre.A worm can target AutoCAD 2000 through 2015. Basically, ACAD/Medre.A can corrupt existing AutoCAD files as well as creating malicious files that are disguised to resemble legitimate AutoCAD files. When a file corrupted by ACAD/Medre.A is opened, it will launch the ACAD/Medre.A's malicious executable and allow it infect other AutoCAD files on the infected machine. Unfortunately, since the ACAD/Medre.A worm is mainly used to steal sensitive data, ACAD/Medre.A will rarely, if ever, display explicit symptoms of an infection.
ACAD/Medre.A’s Main Lines of Attack
The ACAD/Medre.A worm is very good at what ACAD/Medre.A does and can rapidly spread throughout a computer system or network. Basically, ACAD/Medre.A carries out its attack using the following tactics:
- ACAD/Medre.A will detect all AutoCAD files with the DWG extension and then transmit these to a remote server via email.
- The ACAD/Medre.A worm can also steal email information on Outlook or Thunderbird in order to carry out future attacks.
- The ACAD/Medre.A worm also has a sophisticated component that creates a RAR archive. This archive will include the stolen files' metadata and the ACAD/Medre.A worm's own code.
Most of the time, the initial ACAD/Medre.A infection will come from a malicious email attachment. Because of this, ESG security researchers strongly advise scanning all AutoCAD files received via email with an updated anti-malware program before they can infiltrate your computer system. While people that do not use AutoCAD will not be affected greatly by ACAD/Medre.A, industry professionals that rely on this program should consider ACAD/Medre.A a significant threat.
SpyHunter Detects & Remove ACAD/Medre.A
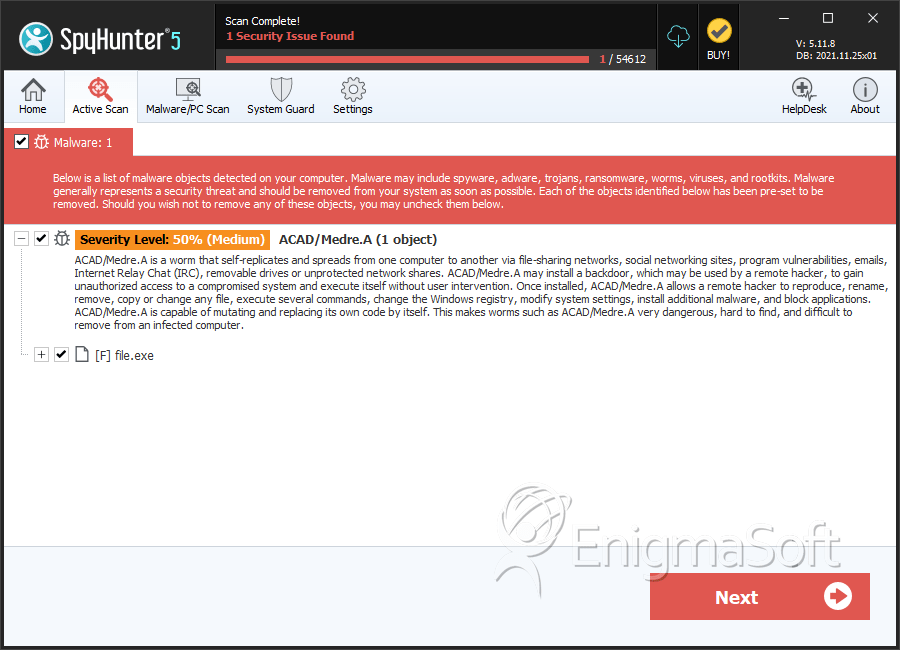
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | %CurrentWorkingDirectoryofdwg%\cad.fas | ||
| 2. | %AutoCADSupportDirectory%\cad.fas | ||
| 3. | %CurrentWorkingDirectoryofdwg%\acad.fas | ||
| 4. | %AutoCADSupportDirectory%\acad.fas | ||
| 5. | %WinDir%\System32\Acad.fas | ||
| 6. | %WinDir%\Acad.fas | ||
| 7. | %AutoCADInstallationFolder%\Support\acad20*.lsp | ||
| 8. | file.exe | 916744d1e7064a5522092f310a7c4ab0 | 0 |
| 9. | file.exe | 25c7e10bb537b4265f6144f2cd7f6d95 | 0 |
| 10. | file.exe | ea04c29bc814af6d96157c1113b3806d | 0 |
| 11. | file.exe | 73dd85951ea154fbb40c26cd259ee0b7 | 0 |
| 12. | file.exe | 7b563740f41e495a68b70cbb22980b20 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.