W32.Gammima.AG
W32.Gammima.AG is part of a large family or worms designed to spread on their own on computers with the Windows operating system and steal passwords for many popular online games, such as World of Warcraft, Arad or Diablo III. The sale of accounts, gold, and in-game items can be considerably lucrative, making online games a prime target for hackers and online scammers. W32.Gammima.AG has also been associated with malware designed to install fake security applications, also known as rogue anti-virus programs. ESG security researchers consider that W32.Gammima.AG is a severe threat to your computer system's health and to your privacy. If you suspect that your computer system has become infected with W32.Gammima.AG, you should use an appropriate anti-malware program to scan your hard drives – particularly if you are a subscriber to various popular online games.
Awaited by fans for more than a decade, Diablo III has a massive online following and had incredible opening day sales when it was finally released. However, Blizzard (the makers of Diablo III) has included an intriguing feature in this release, the so-called Real Money Auction House. Due to the fact that this feature connects in-game items and gold with real cash in an unprecedented way, it has the likelihood to become one of the preferred targets for malware attacks in the next few months. The Real Money Auction House does exactly what its name implies: it allows players to sell their items and gold in exchange for dollars or Euros.
In July of 2012, a variant of the well-known online worm W32.Gammima.AG was detected in the wild. While this malware infection is definitely not new, this variant contained components that allowed it to steal Diablo III account information and other sensitive data. Because of this, Diablo III players should stay on the alert, use the Blizzard authenticator to connect to their games, use a reliable anti-malware program, and use Blizzard's built-in security features (such as the password authenticator and account locking) in order to prevent the consequences of these kinds of attacks. The W32.Gammima.AG worm was created to make copies of itself on all drives on the infected computer system as well as on shared folders and various locations on the victim's hard drive. It has been used to steal passwords for popular online games, particularly MMOs, or Massive Multiplayer Online games that can have millions of users and a bustling economy.
Table of Contents
SpyHunter Detects & Remove W32.Gammima.AG
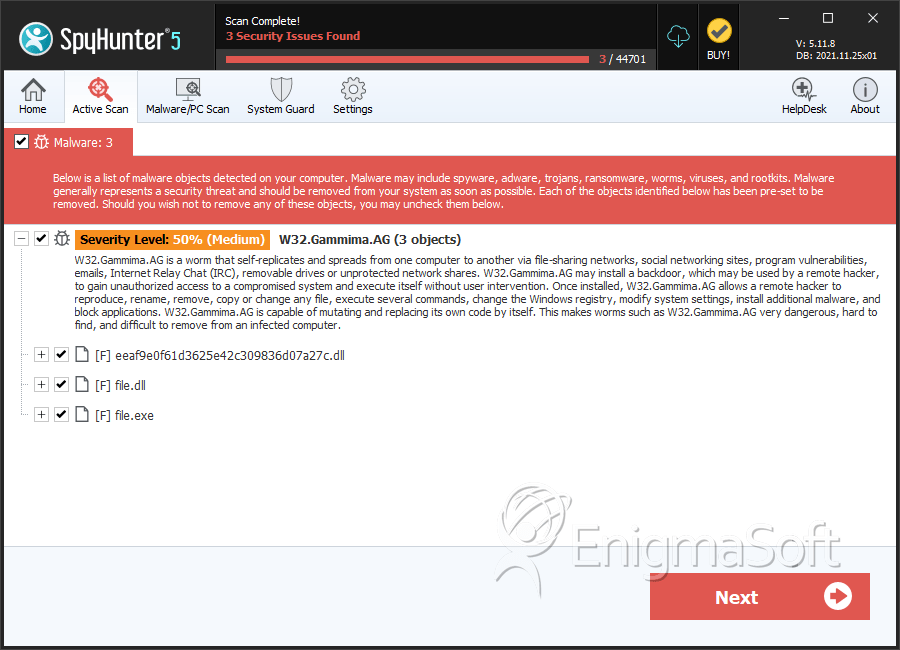
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | %Temp%\[RANDOM FILE NAME].dll | ||
| 2. | %System%\kavo.exe | ||
| 3. | %System%\kavo0.dll | ||
| 4. | [DRIVE LETTER]:\ntdelect.com | ||
| 5. | [DRIVE LETTER]:\autorun.inf | ||
| 6. | eeaf9e0f61d3625e42c309836d07a27c.dll | eeaf9e0f61d3625e42c309836d07a27c | 0 |
| 7. | file.dll | 75eccb98c4f662ed1a77c44016868e87 | 0 |
| 8. | file.exe | becfa1dc26af3f64973e4a79631dda5d | 0 |
| 9. | file.exe | 569274c539a985a35daa195dd2bd6df1 | 0 |
| 10. | file.exe | be84a150a7bf01b5c9ac7a537f1391ae | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.