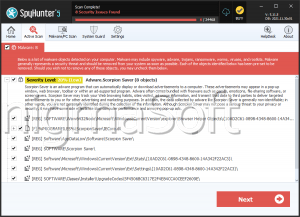
Scorp Ransomware
Cybercriminals have created a new potent ransomware threat capable of disrupting any computer it manages to infect. This particular malware is being tracked as the Scorp Ransomware, and analysis has revealed that it is a variant belonging to the VoidCrypt malware family. Most variants from a single threatening family are practically copies of each other, with minimal differences. However, that in no way diminishes their destructive potential.
Once delivered to the targeted system, the Scorp Ransomware will initiate an encryption process that will see nearly all of the files stored on the device being rendered inaccessible. Victims are left with few viable options when it comes to restoring their data. As part o its actions, the threat also will modify the names of the affected files. It will append to them an email address, a string o random characters and '.scorp' as a new extension. The email used by Scorp is 'sc0rpio@mailfence.com.'
Ransom Note's Details
When the threat has finished locking all targeted file types, it will drop a ransom note with instructions for its victims. The message from the hackers will be delivered to the infected system as a text file named 'Decrypt-me.txt.' According to the message, victims must first and foremost locate a file named prvkey.txt ( can be a number) that should have been created by the ransomware in the C:\ProgramData\ folder. This file is essential for the restoration of the encrypted data and without it, even the cybercriminals will be unable to unlock the files.
The ransom note also clarifies that victims are expected to pay a ransom and the funds that should be transferred must be in the Bitcoin cryptocurrency. Users also can send a couple of small files (less than 1MB) to be decrypted for free. The ransom note reiterates that the only way to reach the attackers is via the 'sc0rpio@mailfence.com' email address.
The full text of the ransom-demanding message is:
'All Your Files Has Been Encrypted
You Have to Pay to Get Your Files Back
1-Go to C:\ProgramData\ or in Your other Drives and send us prvkey*.txt.key file , * might be a number (like this : prvkey3.txt.key)
2-You can send some file little than 1mb for Decryption test to trust us But the test File should not contain valuable data
3-Payment should be with Bitcoin
4-Changing Windows without saving prvkey.txt.key file will cause permanete Data loss
Our Email:sc0rpio@mailfence.com
in Case of no Answer:scorpi0@mailfence.com.'