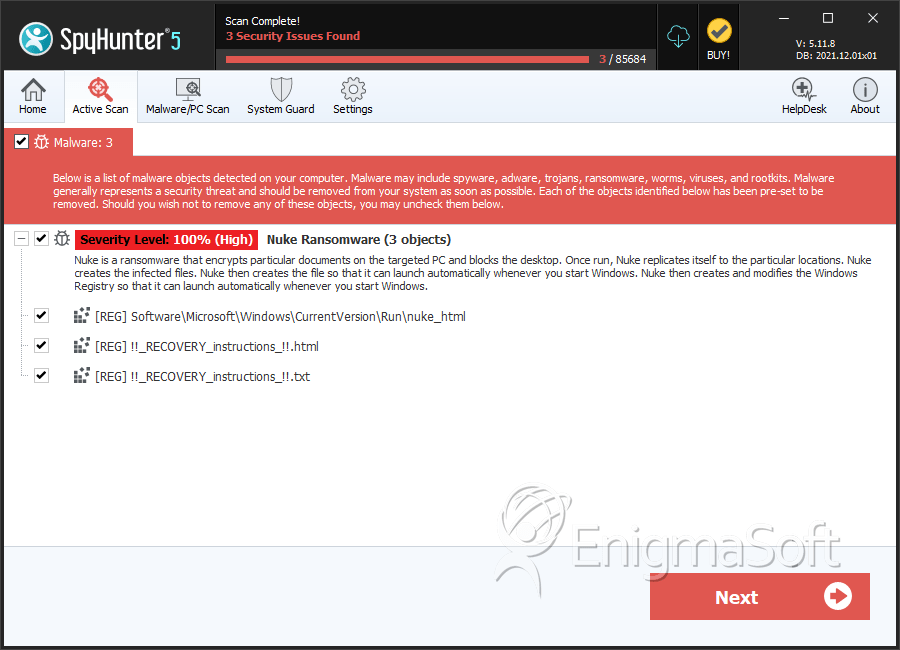
Nuke Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 77 |
| First Seen: | September 30, 2016 |
| Last Seen: | May 2, 2022 |
| OS(es) Affected: | Windows |
The Nuke Ransomware is a ransomware Trojan that is used to take its victims' files hostage. The Nuke Ransomware demands the payment of a substantial ransom from the victim to return access to the victim's files. The Nuke Ransomware is one of numerous other ransomware Trojan attacks that have been uncovered in the last year. The Nuke Ransomware belongs to a large family of ransomware that is being used to carry out attacks on potential victims around the world.
Table of Contents
The Nuke Ransomware Attack
To take the victim's files hostage, the Nuke Ransomware encrypts them by using a strong encryption algorithm. Files that have been encrypted by the Nuke Ransomware can be identified because the Nuke Ransomware changes their names to random characters and adds the extension .0x5bm to the end of the file name. The original name is embedded in the final portion of the encrypted file. Files that have been encrypted by the Nuke Ransomware may become unrecoverable, making it quite difficult to deal with the Nuke Ransomware. However, PC security analysts advise computer users against paying the ransom that the people responsible for the Nuke Ransomware demand in exchange for the means to decrypt the affected files.
How the Nuke Ransomware Demands the Payment of Its Ransom
Whenever the Nuke Ransomware encrypts files, it drops files containing the ransom message associated with the Nuke Ransomware. The Nuke Ransomware drops both a text and an HTML file. These files are named '!!_RECOVERY_instructions_!!.html' and '!!_RECOVERY_instructions_!!.txt.' Below is the message contained inside these ransom note files:
!! Your files and documents on this computer have been encrypted !!
** What has happened to my files? **
Your important files on your computer; photos, documents, and videos have been encrypted. Your files were encrypted using AES and RSA encryption.
** What does this mean? **
File encryption was produced using a unique 256-bit key generated specifically for this machine. Encryption is a way of securing data and requires a special key to decipher.
Unforunate for you, this special key was encrypted using an additional layer of encryption; RSA. Your files were encrypted using the public RSA key. To truly reverse the unfortunate state of your files, you need the private RSA key which is only known by us.
** What should I do next? **
For your information your private key is a paid product. If you really value your data we suggest you start acting fast because you only short amount of time to recover your files before they are gone forever.
There are no solutions to this problem, and no anti-virus software can reverse the process of file encryption because we have also erased recent versions of your files which means you cannot use file recovery software.
Modifying your files in any way can damage your files permenantly and we will no longer be able to help you. Follow our terms assigned to you below, and we will have your files recovered.
** Recovering your files **
- Send an email with the subject 'FILE RECOVERY' to opengates@india.com
- For a free test decrypt, send one small file which will decrypt free
- Wait for a response from us (up to 24-48 hours)
- We will send you further information regarding payment and full file decryption of your computer
- Receive file decryption software to decrypt every encrypted file on the hard drive
Dealing with the Nuke Ransomware and Other, Similar Ransomware Trojans
It can be difficult to deal with ransomware Trojans like the Nuke Ransomware. This is because, unlike other threats, once the Nuke Ransomware is removed, the problem does not stop. Even if the victim removes the Trojan itself, the affected files will remain encrypted and inaccessible. This makes it extremely important for computer users to take steps to back up their files. If adequate backups of all files exist, then computer users can recover from a Nuke Ransomware attack quickly by removing the Trojan and then recovering the files from the backup.
SpyHunter Detects & Remove Nuke Ransomware


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.