Are You Sure You’re NOT Infected with Malware?
Don’t Fall Victim to Malware or Ransomware Attacks!
Detect and remove malware, viruses, ransomware & other threats for FREE! Get Protected with SpyHunter.
Download SpyHunter (FREE Trial!)*If you use a computer and have access to the Internet, chances are high you’ve heard of a bot or botnet, but do you really know what each means and what they do? First of all, bot is a term that is short for robot. No, tiny robots (well, the machine types) are not roaming throughout the Internet or on your computer. However, tiny robotic-type programs, aka viral robots, able to carry out automated yet complex tasks over the Internet could be.
Cybercriminals implant bots on infected or compromised computer systems to build a botnet, a group of compromised systems, and collectively and illegally use the system resources to carry out mass attacks. Attacks could mean distributing email spam campaigns, waging a Denial of Service (DDoS or DNS) attack against targeted websites, i.e. government, fundamental or industrial, to cripple online operations, the global spread of other malware, or other criminal acts offering monetary benefits.
Unlike humans, robots are built to follow instructions and do exactly as ordered, thus allowing an attack of heightened precision. Digital robots or bots offer yet another level of excellence, speed. Thus, bots are designed to carry out complex tasks with precision and speed. The collective resources of botnets, of course, intensify an attack.
Source: YouTube Channel Archer News Network
Bots are mainly distributed using a drive-by attack, a strategy allowing a Trojan downloader to exploit back-end programming of compromised websites to automatically download malicious files upon a landing or visit to the page in which it is housed. However, other common distribution vectors may be used to plant a bot on either stand-alone hosts or networked clients and servers. Also, a possibility is the aid of a co-conspirator or neighboring malware agent, i.e. Trojan, worm, virus, etc., first gaining deceptive entry and leaving open a backdoor to intercept the download of a bot or allow a hacker to add the system to his botnet. Therefore, the best way to avoid your system being used as a bot and added to a botnet is to stay atop of necessary maintenance that patch vulnerable software and keep a stealth antimalware and firewall in place to block malicious downloads. Another thing to avoid is clicking on random links on social media or opening attachments of email messages from unknown senders. These may contain the malicious scripts that turn your machine into a bot or redirect to corrupted websites controlled by the attackers.
Once the malicious code that sets up the target system to become a bot is executed, the malware establishes a connection with its Command-and-Control (C&C) server through which it communicates its tasks – receives commands and other instructions or sends specifically collected data. At the same time, to build the entire botnet, the threat actors focus on recruiting additional computers through common methods. Once the zombie network is ready and fully functioning, the cybercriminals will try to sell or rent it to subcontractors, which then decide on when and what type of attacks they wish to launch.
The client-server approach of controlling the bots is a centralized approach that operates through IRC (Internet Relay Chat) networks, domains and websites. In that case, bots connect to a pre-designated infected IRC channel which the bot herder uses as a C&C server for sending commands through the IRC, i.e each client retrieves and executes commands from one predetermined location.
Contemporary botnet masters use a different architecture that involves peer-to-peer (P2P) networking instead of one central C&C server. Bots are programmed to act both as C&C servers and as clients, so they can scan for malicious websites and other devices in the same botnet, share updated commands and download the latest versions of the botnet malware. Nowadays, hackers prefer the P2P approach as it circumvents the “single point of failure” issue that centralized botnets have, making it harder for anti-malware programs and law enforcement agencies to detect and disrupt the botnet’s operations.
Botnets can be deployed to execute many types of mass-scale cyberattacks against various targets. In the case of a structured DDoS or DNS attack, the bot makes a connection with a command and control (C&C) server to let its boss know it is in place and ready for instruction. While several techniques can be used to launch an attack, the most common are SYN Floods and HTTP Get requests. SYN Floods are an intentional disconnect or broken handshake. The host or client initiates a SYN with the server, who responds with a SYN-Ack and awaits the client or host to send back an Ack. An attacker or bot, however, spoofs IP addresses to send a falsified SYN so that the SYN-Ack has really nowhere to go and ends in a failed connection. When aborted SYN packets are sent in mass to a target, the server resources are stressed, causing the SYN Flood or DDoS. HTTP Get requests, on the other hand, requests a specific web page (usually the target’s homepage) and with the help of a botnet, can overwhelm the target server, thus shutting it down. The thing is, the attack or DDoS can occur without the victim (PC user) realizing a bot is installed and that their system is being used in the attack and illegal act.
Total DDoS attacks in Millions, actual numbers and predictions:
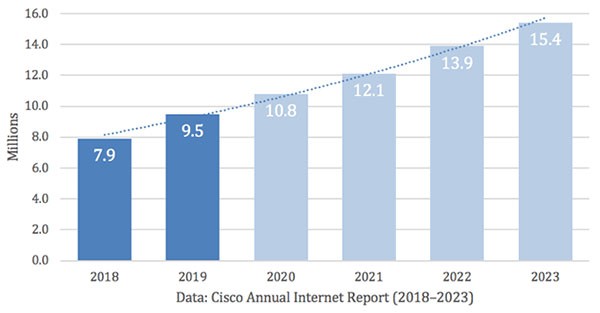
Source: Cisco Annual Internet Report 2018-2023
However, a bot is not limited to partaking in just DDoS strikes. Bots can be programmed to steal vital data or empty your bank account. If receiving aid from a co-conspirator, a backdoor could allow the download of a keylogger or rogue security program that stages a security breach to push the purchase of its full-versioned software. Browser settings may be reversed to allow a floodgate of annoying pop-up advertisements or to corrupt traffic and send victims to sites encouraging click fraud, earning undue pay-per-click residuals or a cybercrook. Another purpose of botnets is to mine stealthily cryptocurrencies using the resources of remotely controlled computers. That allows the cybercrooks to earn profits without paying the electricity bills their victims will receive.
IoT devices also increasingly become a target for botnet herders. The sharp rise of the use of such devices alone, along with the fact that a very tiny percentage of them are actually being protected against malware through a firewall or otherwise, urge hackers to develop specialized threats that would bring in considerable profits. The COVID-19 pandemic contributes as well as the IoT segment is among the fastest-growing malware categories for the first half of 2020. Protecting IoT gadgets is a challenge, though potential dangers for industrial users should not be underestimated, especially in the current circumstances where so many people are working from their homes. Significant IoT botnets include Mukashi, Dark Nexus (which is derived from Mirai and Qbot), Mozi, LeetHozer, and Hoaxcalls.
A look at the key trends in 2019 shows an incredible over 70% increase in the identified and blocked botnet C&C servers compared to the previous year. Also, researchers have observed that last year botnet C&Cs were a very popular infection vector for cybercriminals with over 40% of all detections on the block list of a well-known international organization that tracks cyber threats. Considering the geolocations, Russia takes the top spot for 2019, closely followed by the USA. Other affected countries show a significantly lower number of cases. At the same time, Switzerland and China made the highest leap in botnet detections for 2019.
While some malware families previously associated with botnet activities virtually disappeared, some taken down by authorities, others keep gaining power. Almost 60% of the botnet servers are associated with credential stealers like Lokibot, joined by AZORult at the top of the chart. Emotet and TrickBot keep their positions, however, researchers observed a shift in their fraudulent activities in the past two years. While previously mostly used to commit ebanking scams, recently threat actors who operate botnet C&C servers have moved to a Pay-per-Install (PPI) model. These two malware families are still highly active in propagating themselves alone, but also in serving as droppers for additional malware like Ransomware.
Along with credential stealers, malware droppers, and financial fraudsters, RATs are another popular malware family that is very often associated with botnets. NanoCore and NjRAT report the highest jump in the ranking on a yearly basis (all data from “The Spamhaus Project” www.spamhaus.org).
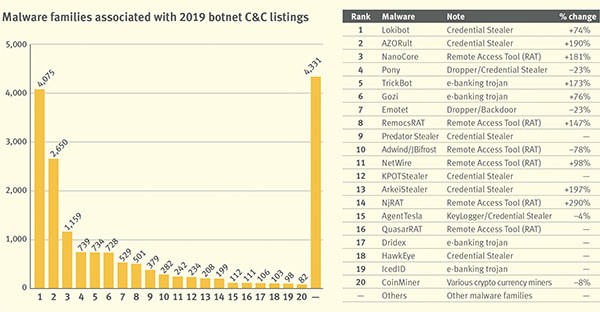
Source: The Spamhaus project
An example of a very popular infection chain that involves botnets is the so-called “Triple Threat”. When implementing that attack vector, threat actors initially infect target organizations with Emotet. Emotet delivers the TrickBot Trojan, which serves as an exploration tool for finding and harvesting sensitive information. If collected data matches the criminals’ intentions, Ryuk Ransomware is delivered as a final step.
Though the malicious programs that make your computer part of a zombie network are designed to work stealthily in the background without raising any suspicion, there are some symptoms that could flaunt the infection. Since the idea behind creating a botnet is to use collective resources without the users’ notice or consent, you may notice your computer needs much longer than normal to perform certain actions, like start-up or shut down. Checking the Task Manager may unveil some weird running programs or processes that consume a huge amount of resources. Also, a hijacked device may start behaving erratically all of a sudden, crash or freeze; unexplained error messages may occur, as well as unusual network traffic.
Bots and other malware activity can drastically slow down your system, bringing it to a frustrating crawl. An overload could cause an undue system crash and threaten the security of data and wipe clean installed applications that require a ‘key’ to reinstall. The best way to determine if your system has a bot aboard and is being used to perform illegal acts is by using a tested and tried anti-malware solution to scan every nook and cranny, in case the malicious files are masked and hidden in the root or kernel. Removal should be swift and precise. In other words, the anti-malware solution should easily be able to distinguish between the good OS files and the bad malicious files without harming data, programs or apps and thus able to quickly restore order.
| # | Threat Name |
Severity Level
Severity Level: The determined severity level of an object, represented
numerically, based on our risk modeling process and research, as explained in our
Threat Assessment Criteria.
|
Alias(es) |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|---|
| 1. | Sysrv-K Botnet | |||
| 2. | iWorm | |||
| 3. | Jaku Botnet | 80 % (High) | 13 | |
| 4. | Wauchos Botnet | |||
| 5. | Kimwolf Botnet Campaign | |||
| 6. | RUBYCARP Botnet | |||
| 7. | KashmirBlack Botnet | |||
| 8. | Scarface Botnet | |||
| 9. | GoBruteforcer Botnet Attacks | |||
| 10. | RapperBot Malware | |||
| 11. | TERRACOTTA | |||
| 12. | Simda Botnet | |||
| 13. | ZHtrap Botnet | |||
| 14. | Momentum Botnet | |||
| 15. | HeadCrab Malware | |||
| 16. | Ddostf Botnet | |||
| 17. | Pink Botnet | |||
| 18. | Smominru | |||
| 19. | SORA Botnet | |||
| 20. | Mirai_ptea Botnet | |||
| 21. | Muhstik Malware | |||
| 22. | UNSTABLE Botnet | |||
| 23. | LilithBot | |||
| 24. | Quad7 Botnet | |||
| 25. | HinataBot | |||
| 26. | Mayhem Botnet | 80 % (High) | 4 | |
| 27. | Ttint Botnet | |||
| 28. | Roboto Botnet | |||
| 29. | Demonbot | |||
| 30. | AESDDoS Botnet |
Last updated: 2026-02-07