Instalador Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 3 |
| First Seen: | January 24, 2018 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
Malware researchers discovered the Instalador Ransomware on January 19th, 2018. The first samples of the Instalador Ransomware suggest that the program is still under development and that the Instalador Ransomware is aimed at Portuguese-speaking users. The threat payload is designed to arrive on remote computers as a software package with updates to popular browser plug-ins like Adobe Flash Player and Java. The Instalador Ransomware appears to be based on the HiddenTear code, also seen as the Unikey Ransomware. The Instalador Ransomware Trojan behaves like the USBR Ransomware and uses a personalized AES-256 cipher to transcode the targeted data. The affected files are renamed to
The Instalador Ransomware is using the '.qwerty' extension to mark the transcoded objects and you may notice that images, presentations, databases, music, text, and spreadsheets are represented by white icons in the Windows Explorer. Some AV companies may use the name QwertyCrypt Ransomware as a substitute for the name Instalador Ransomware. The team behind the Instalador Ransomware is reported to ask potential victims to pay 0.05 Bitcoin (≈585 USD/478 EUR) for retrieving the decryption key and associated decryption program. Cybersecurity vendors stated that the Instalador Ransomware operators are using the 15tGsTDLMztrxP1kCoKPBTaBgv1xCKRtkY Bitcoin wallet to collect payments. Communication with the threat actors may be possible via a channel on the Telegram IM network, which is accessible via smartphones. Computer users that may fall victims to the Instalador Ransomware are likely to be directed to use the t.me/@rodolfoanubis IM channel if they are willing to deliver the ransom payment.
We encourage PC users to look out for the 'Instalador.exe' process that is associated with the Instalador Ransomware. The threat can be terminated with the help of a reputable cybersecurity product. You can rebuild your data using backups and search online for a tool called 'HiddenTearDecrypter.' Malware researchers were successful in cracking the encryption procedure in the Instalador Ransomware, but newer versions of the threat may feature a modified encryption sequence. That is why you should add a backup manager to your OS sooner rather than later. AV engines may flag the files related to the Instalador Ransomware, a.k.a. QwertyCrypt Ransomware as:
- Ransom_Gen.R002C0WAK18
- Trojan ( 005249991 )
- Trojan-Ransom.FileCoder
- Trojan-Ransom.Win32.Gen.hdp
- Trojan.GenericKD.12777021
- Trojan.Ransom.Instalador (A)
- Trojan[Ransom]/Win32.AGeneric
- Win32.Trojan.Gen.Wska
SpyHunter Detects & Remove Instalador Ransomware
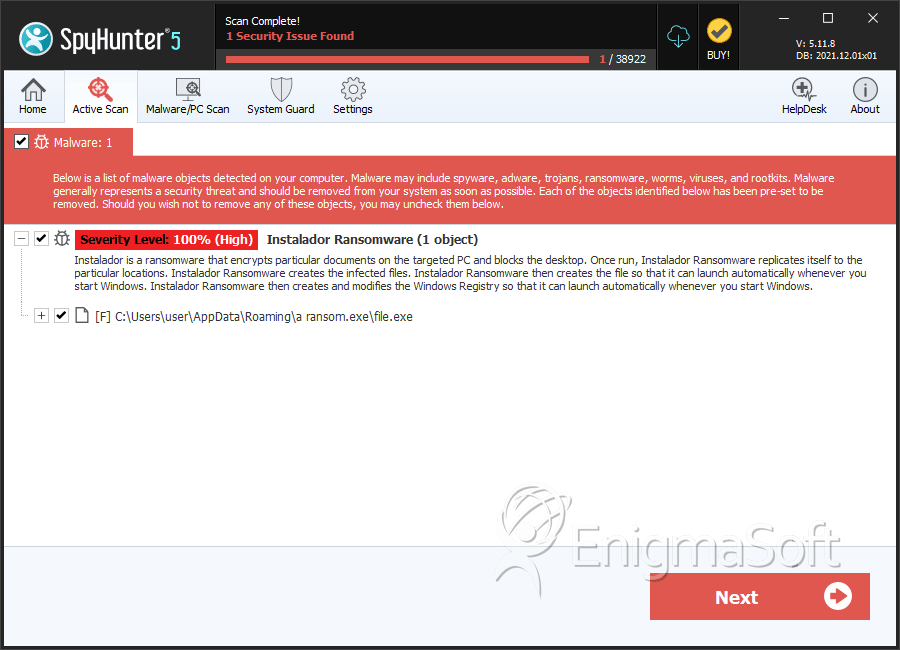
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | dc4c2932b4efa11cb2ce3e4761b1f8a1 | 2 |
