Ghost Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 10,849 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 336 |
| First Seen: | November 21, 2018 |
| Last Seen: | August 10, 2023 |
| OS(es) Affected: | Windows |
The Ghost Ransomware is an encryption ransomware Trojan that first appeared on November 17, 2018. The Ghost Ransomware is typically delivered to victims via corrupted spam email attachments. Once the Ghost Ransomware has been installed onto the victim's computer, it is designed to take the victim's files hostage. The Ghost Ransomware is not very different from the majority of encryption ransomware Trojans, all of which carry out a similar tactic.
Table of Contents
How the Ghost Ransomware Attack Works
The victims of the Ghost Ransomware will receive a PDF or DOCX email file attachment, which uses inserted macro scripts to download and install the Ghost Ransomware onto the victim's computer. Once the Ghost Ransomware is installed, it uses the AES and RSA encryptions to make the victim's files inaccessible, demanding a ransom payment of 360 USD approximately from the victim via a ransom note. The Ghost Ransomware will mark the targeted files with the file extension '.Ghost,' which it adds to the file's name. The following are examples of the types of files that threats like the Ghost Ransomware target in these attacks:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
Once the Ghost Ransomware encrypts the victims' files, it delivers its ransom note in a program window named 'Ghost' that displays the following message onto the victim's computer:
'All your files have been encrypted. but don't worry. I have not deleted them yet. To desencrypt them. you have to pay 0.08116 bitcoin to following address:
h[tt]ps://blockchain[.]info/payment_reguest9 address=1N7AmgH12EN3yAkVMPB5rZoVX758jgLbzjaamount_local=5008currency=USD8nosa vecurrency=true8message=Pay%20me!
Them, send a mail to paymemen@gmail.com with your CODE ID.
I'm sorry for the inconvenience caused.'
Protecting Your Data from Threats Like the Ghost Ransomware
You can remove the Ghost Ransomware threat by using a reliable security program if your data has been compromised by a Ghost Ransomware attack. Unfortunately, once the Ghost Ransomware is done with the files' encryption, these files will not be recoverable without the decryption key. Therefore, computer users should have backup copies of all of their files to counteract the damage caused by threats like the Ghost Ransomware since computer users can restore any files compromised by the Ghost Ransomware by replacing them with a backup copy. If you are willing to pay the ransom that the criminals behind the Ghost Ransomware demand, remember that it only enables these criminals to continue demanding ransom payments, distributing the Ghost Ransomware, and updating this threat or creating new variants. Apart from file backups and a reliable security program, computer users should be aware of the tactics that are used to distribute the Ghost Ransomware, particularly through spam email attachments, recognize these, and prevent them from installing these threats in the first place.
SpyHunter Detects & Remove Ghost Ransomware
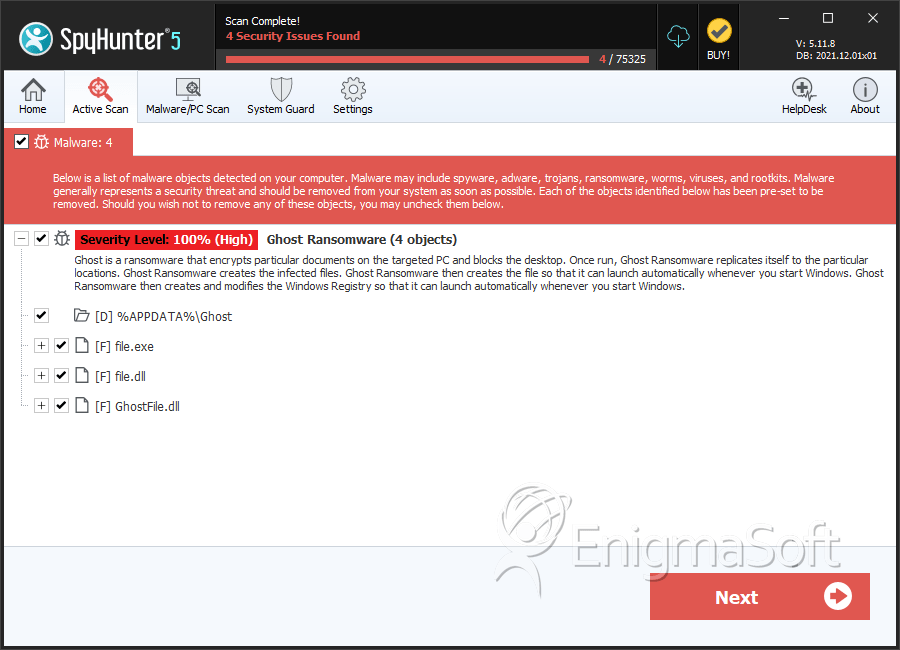
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | cd0f7f29e337f2ebe455ba4a85fb2b70 | 2 |
| 2. | file.dll | 5db40b7c42376cc077383069a9c509eb | 0 |
| 3. | file.exe | 3a2633cd5152a229d1f986073082ecd0 | 0 |
| 4. | GhostFile.dll | 464da6c4465816cba2d278634e2b9d3e | 0 |
Directories
Ghost Ransomware may create the following directory or directories:
| %APPDATA%\Ghost |