FakeCog
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1,505 |
| First Seen: | October 4, 2010 |
| Last Seen: | July 9, 2023 |
| OS(es) Affected: | Windows |
FakeCog is a family of bogus security applications that have been around since 2009. While they carry out a common online scam that is practically identical to rogue security programs belonging to other large families of rogue security programs (such as FakeSmoke and FakeScanti), malware in the FakeCog family is characterized by their green icon shaped like a shield (which attempts to imitate Windows Defender much like FakeSmoke's rogue security programs attempt to imitate Windows Security Center. Some rogue security programs belonging to this extensive family of malware include Dr. Guard, Your Protection, Digital Protection, Protection Center, AnVi, Defense Center, Data Protection, Malware Defense, Paladin Antivirus and User Protection. These names will often be followed by a year (such as 2009, 2010, 2011 or 2012) or by a word like 'Pro'. The presence of any malware in the FakeCog family on your computer system is cause for concern, since ESG security researchers consider rogue security programs belonging to this family to pose a severe danger to your computer's health.
Table of Contents
A Technical Overview of a FakeCog Family Infection
The main way in which programs in the FakeCog family of rogue security programs attack a computer system is by pretending to run a malware scan and then displaying constant fake alerts for non-existent threats. The point of this is to convince the victim that they must pay a certain amount of money in order to register the rogue anti-virus program on the victim's computer in order to remove these threats completely. As part of its installation process, FakeCog-related malware will make dangerous changes to the Windows Registry that must be reversed as part of the FakeCog removal process. These Windows Registry changes allow FakeCog to block certain applications, display its fake alerts and run automatically when Windows starts up. Malware in the FakeCog family will place two malware components into the TEMP folder. These are a DLL file which will be injected into the explorer.exe file process so that FakeCog will run continually on the infected computer system. The second malware component that a FakeCog rogue security program installs is an imitation of the Windows Security Center main window along with an EXE file with the extension .TMP.EXE which will try to uninstall or disable common anti-virus applications that may be installed on the victim's computer system. As part of their installation process, rogue security programs in the FakeCog family also create a Start Menu shortcut and a Desktop icon with the green shield that characterizes FakeCog rogue security programs.
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| K7AntiVirus | Trojan-Downloader |
| Kaspersky | Trojan-Downloader.Win32.FraudLoad.xfup |
| Fortinet | W32/FakeAV.BSY!tr |
| Antiy-AVL | Trojan/Win32.FraudLoad.gen |
| eTrust-Vet | Win32/FakeAV.CYB |
| Sophos | Troj/FakeAV-BSY |
| AntiVir | TR/Dldr.FraudLoad.xfah |
| BitDefender | Trojan.Generic.KDV.45406 |
| eSafe | Win32.TRDldr.FraudLo |
| Avast | Win32:Malware-gen |
| Symantec | AntivirusFraud |
| NOD32 | Win32/TrojanDownloader.Prodatect.AQ |
| Avast | Win32:Agent-AMLR |
| McAfee | Artemis!03C20AC80D0A |
| AVG | Generic4.ANRS |
SpyHunter Detects & Remove FakeCog
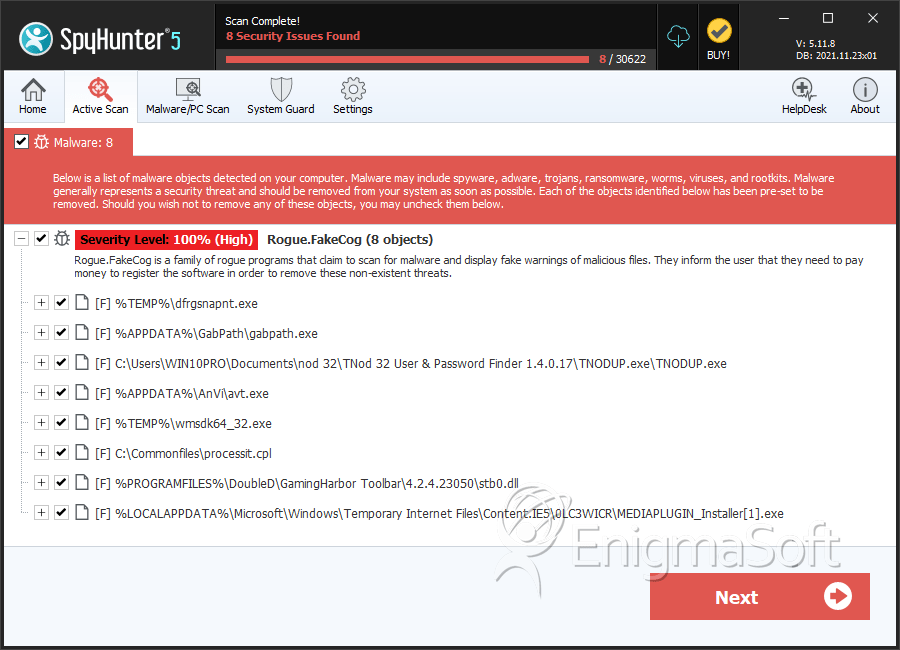
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | avt.exe | 415689ba35701ff80805b12ed06846d7 | 57 |
| 2. | dfrgsnapnt.exe | b82591d16d40e4af689d5178e70dfeae | 56 |
| 3. | dfrgsnapnt.exe | cf419370d8e7732f301a95aec10cd4aa | 55 |
| 4. | dfrgsnapnt.exe | 38a65dc1e60c358c9356a14bb95141e3 | 45 |
| 5. | dfrgsnapnt.exe | bddd35b19d8ce7e42446b0bc182455fe | 45 |
| 6. | dfrgsnapnt.exe | b57d2bb2702314d1414932d7191784cc | 39 |
| 7. | avt.exe | 56e6a70ca07cdb6dace0c52db014bade | 39 |
| 8. | TNODUP.exe | 18c84f2c40e9a1d6a748ef8359403dcc | 34 |
| 9. | avt.exe | 5831379eec07843e525c724a49e0c4e5 | 34 |
| 10. | avt.exe | 0bec56e51cdfd27f3c4ba8c0522be422 | 29 |
| 11. | avt.exe | 0bd4b5d7b2f0a67f0741b0a0da0dedd4 | 27 |
| 12. | avt.exe | abfb4e71253c82b8830b569f7c9216f6 | 24 |
| 13. | avt.exe | 8f3c2ed2cb047eb2b77804e16fab0a86 | 21 |
| 14. | dfrgsnapnt.exe | 161c82fa6bc007d8876a32166aef23c3 | 19 |
| 15. | avt.exe | 894edee5b466f504f73d6d4cc5748dc1 | 16 |
| 16. | avt.exe | b9e7141f69fc082fc05e977d2d1844fd | 14 |
| 17. | stb0.dll | e1463171557fd96c4aa6a5b94da56150 | 13 |
| 18. | avt.exe | c9ac2f34842073da9a608ad3bd071ca1 | 12 |
| 19. | avt.exe | 45033a8780887fa9460352f3514f7925 | 12 |
| 20. | ComboFix.exe | 3a7288c09145e5a1edbe619b917ec2ea | 7 |
| 21. | ComboFix.exe | 03c20ac80d0af1affc6fc454f35999fc | 5 |
| 22. | avt.exe | 3d04633909edc25991e68d04a344f3bc | 4 |
| 23. | MEDIAPLUGIN_Installer[1].exe | 1affc3a34abd0afc6152a245232079db | 2 |
| 24. | MemScan.exe | 1e4959ff1843cd1d51cbc4ce2fa5ade0 | 2 |
| 25. | ComboFix.exe | 3fef48d0d82e80548a2ed96a674583cd | 2 |
| 26. | mobedirlinkers.exe | d6f32418d68a998d9c643c0ffa009f2c | 1 |
