FakeSmoke
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 110 |
| First Seen: | December 1, 2010 |
| OS(es) Affected: | Windows |
FakeSmoke is a family of rogue security programs that have been around since 2009. Some examples of malware belonging to the FakeSmoke family include SoftCop, Antivirus, BlockKeeper, AntiAID, Link Safeness, SiteVillain and Virus Protector. If malware belonging to the FakeSmoke family of rogue security programs is present on your computer system, this constitutes a severe risk to your computer's integrity. ESG security researchers urge immediate action in order to remove this dangerous invader from your hard drive.
Table of Contents
A Summary of the FakeSmoke Scam
There are various Trojan infections that belong to the FakeSmoke family of rogue security programs. All of these have two components in common; a fake version of Windows Security Center, which consists of nothing more than an interface designed to mimic the layout of Security Center and a bogus anti-virus which carries out the main portion of the FakeSmoke scam. These two components take over the victim's computer system and display a constant stream of fake notifications that are designed to imitate closely notifications that Windows Security Center displays normally. These notifications will usually urge the victim to register the fake anti-virus, purchasing a malicious product with absolutely no anti-malware capabilities. FakeSmoke perform fake scans and display a false positive in order to sell copies of their useless product.
How FakeSmoke Attacks Your Computer System
Typically, Trojans in the FakeSmoke family of rogue security programs copy themselves to the System folder. The program's name varies depending on the particular rogue security program that is infecting your computer system. As part of their installation process, FakeSmoke makes a change to the Windows Registry that allows them to run automatically whenever Windows starts up. As part of its installation process, a rogue security program belonging to the FakeSmoke family of rogue security programs will also install files in the Program Files, like a legitimate application. This will usually be in a folder with the rogue security program's name containing another folder marked as 'Software'. FakeSmoke also creates a Start Menu icon and Desktop shortcut. The icon that FakeSmoke uses is often identical from one rogue security program to another, characterizing this malware infection. As part of their payload, FakeSmoke displays its fake Windows Security Center window and a legitimate-looking notification which has been found to appear in various languages, among them Italian, French, German and Russian. Some of FakeSmoke malware's messages will include a 'Get Registration Code' button, which will then take the victim to a malicious website requesting the victim's credit card information.
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| AVG | Generic4.ADKX |
| Ikarus | Gen.Variant |
| Sunbelt | Trojan.Win32.FraudPack.aoej (v) |
| AhnLab-V3 | Trojan/Win32.FakeAV |
| Antiy-AVL | Trojan/Win32.Pakes.gen |
| AntiVir | TR/FakeAV.1690112 |
| DrWeb | Trojan.Fakealert.14846 |
| Avast | Win32:Adware-gen |
| Symantec | Trojan.FakeAV!gen25 |
| F-Prot | W32/MalwareS.AYNI |
| NOD32 | Win32/Adware.VirusProtector.AA |
| McAfee | Artemis!E85975B410E2 |
| CAT-QuickHeal | Trojan.FakeSmoke |
| Panda | Trj/Krap.Y |
| AVG | FakeAV.AUI |
SpyHunter Detects & Remove FakeSmoke
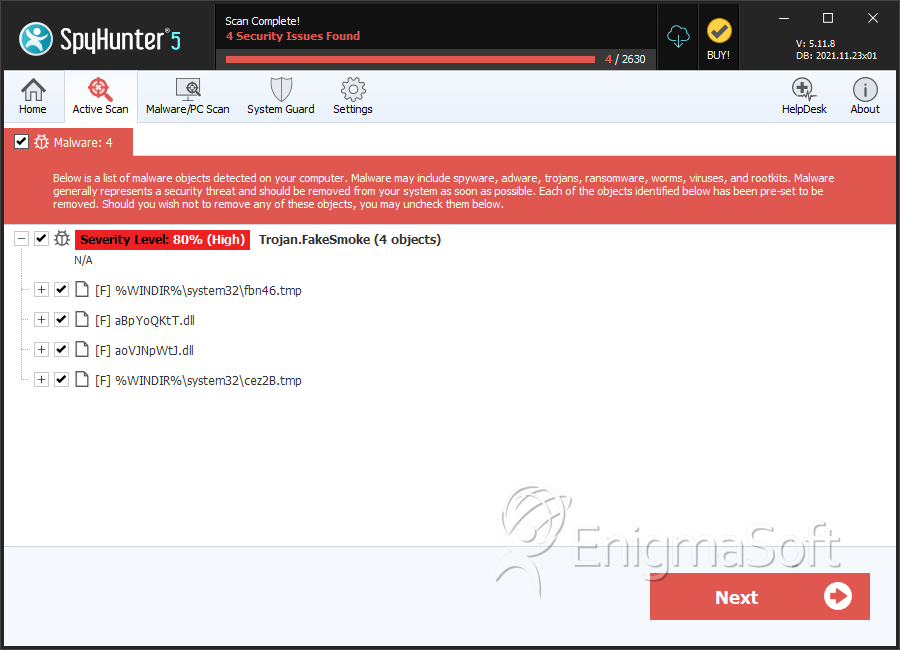
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | fbn46.tmp | 1bd24f3b3bc23fe578ac533359d93779 | 81 |
| 2. | aBpYoQKtT.dll | 2c019ec0d78438ac96f80ad38a030a02 | 25 |
| 3. | aoVJNpWtJ.dll | e85975b410e2908d38ae9bf3665718e5 | 3 |
| 4. | cez2B.tmp | 05f89f6b0e80845d24e3a25ff0f986a6 | 1 |

