Bansomqare Wanna Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 15 |
| First Seen: | April 6, 2018 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
The Bansomqare Wanna Ransomware is an encryption ransomware Trojan. The Bansomqare Wanna Ransomware is commonly delivered in the form of a Microsoft Word document with corrupted embedded macro scripts that download and install the Bansomqare Wanna Ransomware onto the victim's computer. The Bansomqare Wanna Ransomware will reference WhatsApp, a popular messaging application in its attack, to convince the victims to download the file being used to deliver the Bansomqare Wanna Ransomware threat. Once installed, the Bansomqare Wanna Ransomware will run using executable files named 'runas.exe' and 'whatsapp.exe' on the victim's computer and will carry out its attack.
Table of Contents
How the Bansomqare Wanna Ransomware Attacks a Computer
Once the Bansomqare Wanna Ransomware is installed, the Bansomqare Wanna Ransomware will encrypt the victim's files using a strong encryption algorithm. The Bansomqare Wanna Ransomware also will interfere with the Windows recovery utilities and various native Windows services. The Bansomqare Wanna Ransomware will use a strong encryption algorithm to encrypt the victim's files and takes them, hostage, since they will be unrecoverable except to those that have the decryption key. The Bansomqare Wanna Ransomware marks the files encrypted by the attack by adding the file extension '.bitcoin' to the original affected file's name. Threats like the Bansomqare Wanna Ransomware target the user-generated files, such as photos, audio, video, and numerous document types, while avoiding Windows system files and the victim's applications. The files that are targeted in attacks like the Bansomqare Wanna Ransomware include:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
The reason for this is that threats like the Bansomqare Wanna Ransomware want to take the victim's files hostage, but they also need for the victim to be able to access their operating system and Web browser to carry out a payment.
How the Bansomqare Wanna Ransomware Demands Its Ransom Payment
The Bansomqare Wanna Ransomware displays a program window with the name 'Bansomqare Wanna' after encrypting the victim's files. This ransom note has been seen before in other threats, mainly in ransomware Trojans that try to imitate WanaCry, a high-profile ransomware threat. The text of the Bansomqare Wanna Ransomware ransom note reads:
'Ooops, Your files have been encrypted!
What happened to my computer?
Your important files are encrypted.
Many of your documents, photo, video, database, and other files are no longer accessible because he have been encrypted. Maybe you are busy looking for a way to recover your files but do not waste your time. Nobody can recover your files without our decryption service.
Can I recover my files?
Sure, We guarantee that you can recover all your files safely and easily.
But you have not so enough time.
You can decrypt some of your files for free.
The bitcoin address will be saved to the 'bitcoin2018.txt' file'
It is important to avoid following the instructions in the Bansomqare Wanna Ransomware ransom note, or making any payment to the Bitcoin address contained in the text file associated with the Bansomqare Wanna Ransomware attack. Instead of this, PC security researchers strongly advise computer users to take preventive measures against the Bansomqare Wanna Ransomware and similar threats. The files encrypted by the Bansomqare Wanna Ransomware should be deleted and replaced with backup copies.
SpyHunter Detects & Remove Bansomqare Wanna Ransomware
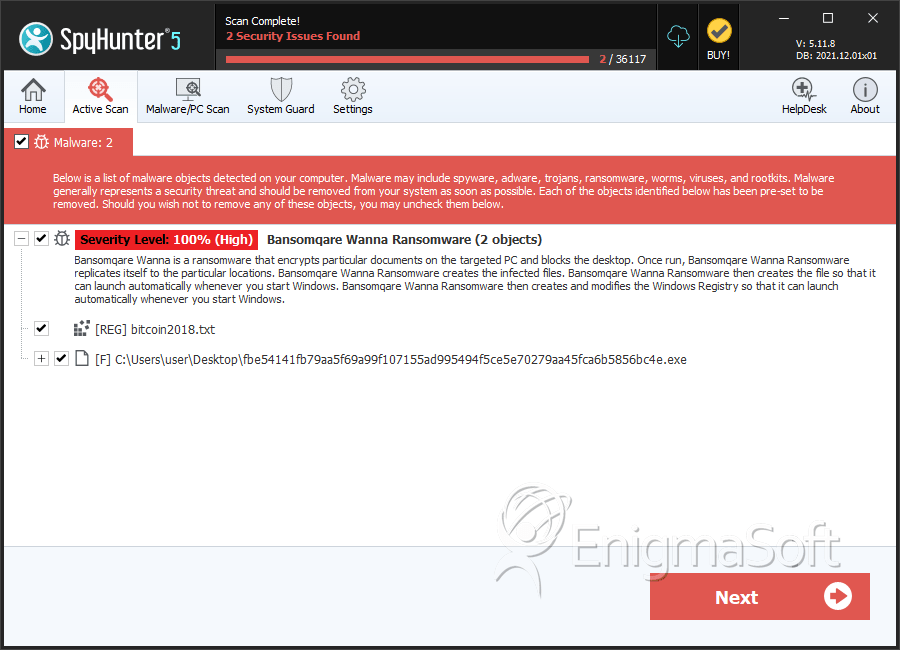
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | fbe54141fb79aa5f69a99f107155ad995494f5ce5e70279aa45fca6b5856bc4e.exe | 6d0fefdd39ad1c289e15eac8cb2d9394 | 2 |
