AntiMalware
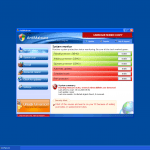
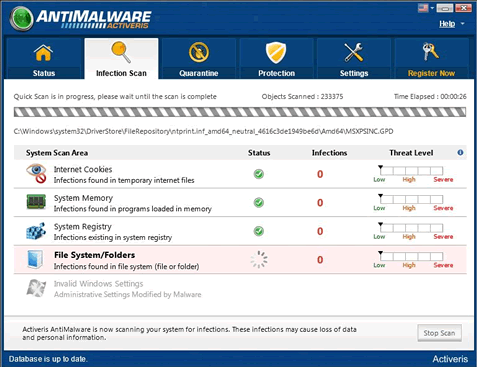
A typical deceptive campaign is disguising harmful threats as legitimate security programs in order to steal money from inexperienced victims. AntiMalware is a particularly short-named version of this campaign, with clones with names such as Active Security and Total Security. AntiMalware uses an interface that is very similar to the Windows Defender and legitimate Microsoft security programs, to make the victim believe that AntiMalware is a legitimate anti-malware application. Observing AntiMalware's design, you will quickly spot authentic-looking Windows and Microsoft Security Essentials logos as well as a layout that may seem familiar to most users of legitimate Microsoft Security products. It is important to understand that AntiMalware is a fraud with absolutely no anti-malware capabilities. If you find that your computer is displaying notifications from AntiMalware, you will need to use a reliable, real anti-malware program to remove AntiMalware from your computer.
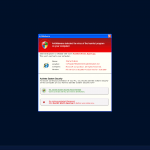
AntiMalware belongs to a family of rogue security programs that attempt to mislead the user they are legitimate anti-malware applications. These infections affect computers running Microsoft Windows operating system, and most of them have the characteristics of a Trojan-type of malware. The typical behavior of threats like AntiMalware is to pretend they are performing an anti-virus scan on the user's computer, and subsequently to display a long list of infections they have supposedly detected on that PC. Then, the malware would start bombarding the user with fake security alerts and pop-up windows, eventually asking him or her to purchase the full version of AntiMalware in order to have all these non-existent infections removed from the PC.
The truth is, however, that AntiMalware, or any of its variants, cannot detect any malware as these malicious apps do not have a real anti-malware scanner. Therefore, all displayed scan results are completely fake, and buying any of the offered products will most likely results in the user's computer being actually infected with some real and dangerous malware threats. Infections like AntiMalware exploit a well known deceptive technique to trick naive PC users into buying the bogus security tools, and that includes using names, logos, and interface that strongly resemble those of legitimate Microsoft security products, like Microsoft Security Essentials and Windows Defender. The layout of the windows and alerts that AntiMalware displays also look familiar and authentic to many Windows users, which makes such malware campaigns particularly successful.
Fake anti-virus programs like AntiMalware can have many variants, all with the same functionalities, behavior, and strategy. Researchers warn that these malicious apps can be endlessly "re-skinned" and "rebranded," meaning that the cybercriminals can use the same source code to develop new clones which have different names, appearances, and interfaces but are able to perform the same actions. Some aliases of threats detected as part of the AntiMalware campaign include Trojan.FakeAV, Artemis!7BB7211CD996, Trojan:Win32FakeCog, CoreGuard Antivirus 2009, AntiVirus, Dr.Guard, Malware Defense, Digital Protection, AntiMalware, Your Protection, Data Protection, Protection Center, Defense Center, Anvi Antivirus, Paladin Antivirus, User Protection, Protection Center, RogueAntiSpyware.WindowsAntivirusPro, FraudTool.Win32.RogueSecurity, Packed.Win32.TDSS.aa, and many others.
Table of Contents
The Infection’s Typical Routine and Distribution Channels
Rogue security programs like AntiMalware follow a typical routine that includes several steps. First, the malware needs to sneak into the target PC, usually with the help of another Trojan capable of exploiting vulnerabilities in Java or Flash. After the malware is installed, it makes changes to the Windows registry in order to ensure its persistence and launch upon every boot. Then, AntiMalware-like threats start to flood the user with fake security warnings, system tray balloons, and deceptive scan results. These malicious processes slow the performance of the infected computer or even crash it down completely, which, in turn, again serves the malware's effort to convince the user that the strange behavior is due to the presence of malware on his or her PC. Finally, the rogue program will suggest the user to purchase the "full version" of the program to have the computer all cleaned up.
Rogue anti-malware applications like AntiMalware can land on a PC through various different channels, however, that happens mostly when users visit websites with embedded malicious scripts or downloads software from unsafe sources. Spam email campaigns that contain attachments carrying the malware, or links leading to compromised pages on the Internet, are another distribution channel. Spammed links and files can also be found on online forums and blogs, whereas malicious advertisements, hacked software, movies or music, and infected torrents on file-sharing networks can carry the malicious payloads as well. Researchers have estimated that the largest part of the rogue anti-malware programs get distributed through affiliate programs where the vendor recruits affiliates for the task of spreading the malicious apps in exchange for some part of the revenues.
Technical Details
The changes made by AntiMalware to the Windows registry ensure that the malicious tool runs automatically upon system start-up, while the Windows Settings are altered to allow the malware to display its misleading error and security messages, to block specific applications, and to connect to the Internet. Technical details about the AntiMalware rogue security program, in this case, identified as Win32/FakeCog, show that it creates a subkey and its associated entries in the Windows registry:
In subkey: HKLM\SOFTWARE\AntiMalware
Sets value: "SecStatus_3"
With data: "dword:00000001"
Sets value: "Settings_0"
With data: "dword:00000000"
Sets value: "SecStatus_4"
With data: "dword:00000001"
Sets value: "SecStatus_5"
With data: "dword:00000001"
Sets value: "swver"
With data: "1.0"
Sets value: "dbver"
With data: "1.0"
Sets value: "FD"
With data: "dword:00000000"
Sets value: "GUID"
With data: "455366164553576845534928"
Sets value: "dbsigns"
With data: "61473"
Sets value: "InfectedFiles"
With data: "C:\WINDOWS\System32\olecli.dll,C:\WINDOWS\System32\scrrun.dll,C:\WINDOWS\System32\stclient.dll,C:\WINDOWS\System32\url.dll,C:\WINDOWS\System32\winhttp.dll,C:\WINDOWS\System32\oobe\dtsgnup.htm,C:\WINDOWS\System32\Drivers\cdaudio.sys,C:\WINDOWS\System32\Drivers\sonydcam.sys,C:\Program Files\outlook Express\wab.exe,"
Sets value: "Infected"
With data: "dword:00000009"
It is also known that Win32/FakeCog leaves two components in the %TEMP% folder. The first component creates a .dll file with a variable name in the same directory. That file is then injected into the corresponding Windows Explorer process, ensuring this way that the malware keeps running on the infected computer. The second component displays a dialog box that looks like it belongs to Windows Security Center and then drops a file with a double-named extension (which can look like asdf.tmp.exe, for example) in that same folder. This last file attempts to disable and remove any legit security products found on the computer, installing at the same time the rogue program.
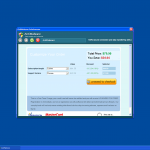
The malware also creates shortcuts on the desktop, again using names and logos of legitimate Windows anti-virus tools, for example, "Defense Center Support", or "Defense Center". Win32/FakeCog then displays false scan results and fake security alerts, pretending to be Windows Security Center and attempting to convince the user to purchase the full version of the malicious program. To make all transactions seem safe, the malware puts the logos of well-known payment companies like Mastercard and Visa to the bottom left corner of the displayed windows. It also constantly shows system tray balloons and dialog boxes "informing" the user that various dangerous threats like rootkits and Trojans have been detected on the computer, trying again to draw the attention of the victim and to convince it to upgrade the currently installed demo version of the rogue software to the complete and paid version.
Win32/FakeCog is also capable of connecting to malicious websites and downloading additional files from them. These encrypted files could contain dangerous data as well as other types of malware. Some variants of the rogue security software also have another functionality - to disable Windows Task Manager. This happens through modifications in the registry:
In subkey: HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System
Sets value: "DisableTaskMgr"
With data: "1"
In subkey: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system
Sets value: "DisableTaskMgr"
With data: "1"
How to Protect Against Rogue Security Software like AntiMalware
The most important thing that users should do in order to avoid the infection with AntiMalware and similar threats is to avoid suspicious websites that could contain malicious scripts, not to download and install files from untrusted sources, and not to open e-mail attachments from unknown senders. The use of an Internet browser with strong security settings could also protect against such rogue security programs, yet the purchase of a reputable anti-malware application is the safest method of protection against these dangerous infections. The removal of AntiMalware and its variants is also tricky, so inexperienced PC users are advised to use a reliable professional removal tool.
Regardless of Its Name, AntiMalware is Actually a Threat
AntiMalware is a typical iteration of the rogue security software deceptive strategy. This is a well-known online tactic that is designed to prey on inexperienced computer users that frequent unsafe websites. The AntiMalware strategy has several steps, all of which are typical of this kind of infection:
- First, AntiMalware is installed on the victim's computer, usually with the help of another Trojan. Typical sources of an AntiMalware infection may include unsafe advertisements that exploit security vulnerabilities in Java or Flash, fake video codecs on pornographic video websites and fake versions of popular files on file sharing networks.
- Once installed, AntiMalware makes changes to the Windows registry that allow AntiMalware to run automatically upon start-up. AntiMalware also alters your computer's settings so that AntiMalware will have the capacity to display error messages, system notifications and security alerts, as well as being able to connect to the Internet, block specific applications and crash your computer unexpectedly.
- Once the victim's computer is restarted, AntiMalware will use its new-found power over that computer in order to make the victim believe that a threat has been detected. AntiMalware will do this by displaying a fake scan of the victim's computer, pestering the victim with constant fake security alerts and causing the victim's computer to behave erratically, crash frequently, run slowly and become unstable.
- AntiMalware will then pretend to offer a solution to the problems AntiMalware itself caused. However, first the victim will have to pay for a fake 'full version' of AntiMalware.
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Symantec | Trojan.FakeAV |
| Panda | Suspicious file |
| McAfee+Artemis | Artemis!7BB7211CD996 |
| F-Secure | Suspicious:W32/Riskware!Online |
| Sophos | Sus/UnkPacker |
| Sunbelt | FraudTool.Win32.RogueSecurity (v) |
| Sophos | Mal/FakeAV-BP |
| NOD32 | a variant of Win32/Kryptik.BFC |
| Microsoft | Trojan:Win32/FakeCog |
| McAfee-GW-Edition | Trojan.PCK.Tdss.AA.636 |
| McAfee+Artemis | Artemis!6B53DC5751F6 |
| Kaspersky | Packed.Win32.TDSS.aa |
| Ikarus | Packed.Win32.Tdss |
| AVG | SHeur2.BVVU |
| AntiVir | TR/PCK.Tdss.AA.636 |
SpyHunter Detects & Remove AntiMalware
AntiMalware Video
Tip: Turn your sound ON and watch the video in Full Screen mode.
AntiMalware Screenshots
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | antimalware[1].exe | 5c69d34ec162f045228eb5cb316ff8c9 | 0 |
| 2. | antimalware.exe | a15d8b2aba915c9d01ece6aed792a7e8 | 0 |
| 3. | antimalware.exe | 4689058a0d017dc865f4969e8f4d3892 | 0 |
| 4. | antimalware.exe | 7bb7211cd99636a6c43f212b807de8f2 | 0 |
| 5. | AntiMalware.exe | b7f355a106a75ad266ac85ef00e6faa3 | 0 |