Worm.Python.Agent
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 11,031 |
| Threat Level: | 50 % (Medium) |
| Infected Computers: | 13,778 |
| First Seen: | July 15, 2017 |
| Last Seen: | January 30, 2026 |
| OS(es) Affected: | Windows |
Anti-virus products do not always check for the presence of particular cyber threats – sometimes, they look for a particular behavior that is related to malicious software, and use generic descriptions for such files. One of these descriptions is 'Worm.Python.Agent' – it is typically used to refer to a malicious file that exhibits behavior typical for computer worms. This means that it might be able to self-replicate to removable storage, shared network drives, and other accessible storage. As the name of the detection suggests, the threat is likely to be written in the Python programming language.
Although Worm.Python.Agent is used to describe computer worms, you should know that these threats might exhibit additional harmful traits – often, backdoor Trojans have the ability to spread across the network like a computer worm.
Currently, cybercriminals are abusing the chaos surrounding the Coronavirus outbreak to distribute malicious files that are disguised as leaflets or documents regarding the infamous virus. In many cases, these files might be caught as 'Worm.Python.Agent' by your anti-virus software.
Table of Contents
SpyHunter Detects & Remove Worm.Python.Agent
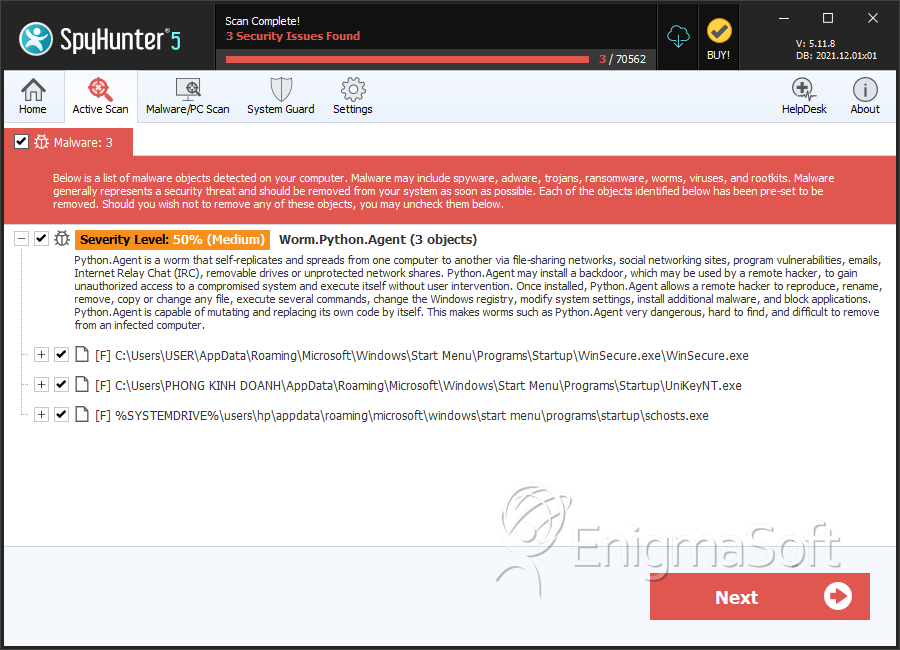
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | f01e5.exe | 3217beecdd50219e106b039a4eb1f662 | 10 |
| 2. | bot.exe | 69bc8cc4a9e4e9e16674f13bf208fd0a | 6 |
| 3. | tmp566A.tmpg r.exe | 4f972d5956b43955b9a0b7f215da76d6 | 6 |
| 4. | Hhzge.exe | 8cc695aede6f46df88287895f79a639f | 5 |
| 5. | 2eff39848b503cef5851c596a5ec669b68f1c1115063b8749fe11090c5e028e3.dll | 7112a1006b204998a3587a4677c4478c | 4 |
| 6. | Synapse Cracker.exe | e6669644bd9ea8c3acdf7a429b0dfa00 | 4 |
| 7. | DuckySploit.exe | 0af7af82500defa27a94d10d26fe226f | 3 |
| 8. | Nitro Gen +Checker.exe | 3862cfed4cf0c1dcfff667101dd17490 | 3 |
| 9. | ff196.exe | 4a5f3ba4130ab892c1fc4e724e5dbeef | 3 |
| 10. | 02641de534a8ac83f24242bb589b9ecb769bd25235e6f345f05c340bcd7c2634.dll | 49258619c1582a831ddc18aa30204cdd | 2 |
| 11. | 04a5238487b4ed9a00c14a7402c3a7390149310b64cfc743dab9d0329821e578.dll | f4eee3ad65b2b200e83007a2e4d298a3 | 2 |
| 12. | 04bf1b479f1b502b1e81ed92eca409140202856b15237d7e4e469f019b345e47.dll | e73f2038a303deb3d8f96726d50c94b8 | 2 |
| 13. | 088da0e42b76740bd0bf7a3ada64268dab7d0df2ed9929296630f209d94e0da6.dll | b074d578e349fc86b5fb690e1e2b5499 | 2 |
| 14. | 08eab55c5eb9a73e8f6ffef03a4b1f4fc9a005bcc070d63fc59b1672e46e4de6.dll | 5cdf921b29da7c868be25b2d246aa5d8 | 2 |
| 15. | 0a86062ad4c2c16e5bab597ac0c6598f568017b9720bb57a14e3b2e1e26f4f5e.dll | f2d4b5b3d2a82451831bdb936239e3d1 | 2 |
| 16. | 0bb0a2111b48afd9ee8186d9b5f81db91d8679d39df5edcf9d3cea6535237c2c.dll | 0845da911143f54b864f0f70a7b503ec | 2 |
| 17. | 1298daf4128053929fbc1c8fe7f536828c7e4b4ff97610a843d80de96e5e908c.dll | 20266cdf32490816dd6d84993d43a70d | 2 |
| 18. | 165776db86405be546ddca54fd8f61fd0b32835338f21450c59fb3bbfdb824dc.dll | 0db6e0b4907f484211d54bb3456a190d | 2 |
| 19. | 1b10af44b46e160c29f5df9d18e20f4c652418c35df8dd8ddd44cb5fe266f5db.dll | 2fa56b2ab4b789bef2916b0992e7a182 | 2 |
| 20. | 209b3ddf6e54adc9166caeb01cdd4de55f125a9a74013db282521a790e113832.dll | 1227d12c93bc6ddcb7cda61d30a6b0fc | 2 |
| 21. | 27eb2c8077ca04969145e1ac6009b43c9d7e8a985a6d6396cf995c33ca46b4b4.dll | 18f00346487206e762ac1886a2821943 | 2 |
| 22. | 2c304604086bf262c0a347be06b29c79d3473994d19ba7b93fd4b1ff464c4b41.dll | 20ed801f031508360ca4a82144d6ca37 | 2 |
| 23. | 2c62b07467f44b41d4cc5d262f6ed5023865be49d5fc6397fff18ab989625cc8.dll | 74fb74e601141fb26f8237b08eaf3436 | 2 |
| 24. | 2ce25ce9423854ee62434c7d1c39c447b8275697a52a333d7faf7d29eaf7694f.dll | d048f0539a6533aaad45ba65e2c570e0 | 2 |
| 25. | 2cf52f36e7955d6b91582886a0f3f57e6866fd9639156b3529fb7cf95833bdf8.dll | c23e48b9a1852c6b059939c68e46f80b | 2 |
| 26. | 2d66e6a62436980e9ca1c20a3328bd9443bff30c1973741b5fc2c405fd88610a.dll | d9f290f4e89190b22ea6acc518278705 | 2 |
| 27. | 2e648818d565bbb6c7d75c8422e0585474ef8935e8a96d729d86c1185f626acf.dll | 0dec91b7e1903084cd03994ac60379a4 | 2 |
| 28. | 107785a5e4aec54be8a66d9a44073cef337b122acf581ba8ebfe1e3216628611.dll | c7f0b0343d3ef18d7b12230db3506069 | 0 |
Registry Details
Analysis Report
General information
| Family Name: | Worm.Python.Agent |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
883efe93e36fa83b43b181664e8a6bc4
SHA1:
4074e206bc137d0d4c9df4c438197dc7644d488b
File Size:
4.73 MB, 4730812 bytes
|
|
MD5:
03a96fc826a577d3f91786eab549669d
SHA1:
89dd2d09956dd182c73008ec22578c1d883a0365
SHA256:
BBDEF45A796C11A657D766AD8A071943B33652B58FBE937E52716475050CB905
File Size:
2.53 MB, 2528051 bytes
|
|
MD5:
5bee25f4229f54c4fe7b435eb453cefa
SHA1:
a3ec2f7814be9231953feab965612aef073d6787
SHA256:
8F51D16780140173D2CF9FBAA9329CA4AD10C01D71CAC2A0379B6AFAA5B412FB
File Size:
4.21 MB, 4210688 bytes
|
|
MD5:
9e200f616ea40d3b8ce111111e2cc9e3
SHA1:
f30fc359b25ea1d1176f87e72c50faf6321c8318
SHA256:
4EFF71CA97C13F925E9F91F2C3F6EC67BB1EF97CE2EB934A1E593DD425F31FCE
File Size:
4.73 MB, 4730812 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File is 32-bit executable
- File is 64-bit executable
- File is console application (IMAGE_SUBSYSTEM_WINDOWS_CUI)
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
Show More
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.File Traits
- big overlay
- No Version Info
- WinZip SFX
- x86
- ZIP (In Overlay)
- ZIPinO
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Syscall Use |
Show More
|
