WannaRen Ransomware
At the start of April 2020, malware researchers uncovered a new ransomware threat dubbed the WannaRen Ransomware. It would appear that the WannaRen Ransomware targets Chinese users mainly.
Nearly three years after the chaos caused by WannaCry, a new virus called "WannaRen" has appeared to continue on the legacy. WannaRen works similarly to WannaCry and encrypts files across Windows computers. Like most ransomware, the virus demands a payment of 0.05 bitcoin for the safe return of data.
Researchers have uncovered two variants of WannaRen. The main difference between the two is that they send information using either pictures or text. The language used for the information is in simplified Chinese, and the bitcoin address for both versions is the same. The two variants likely come from the same person/group.
The Chinese web security firm Huorong Security found a supposed sample of the virus. The company confirmed on April 8 that the sample was, in fact, a decryption tool. The team looked at real samples of the virus and discovered everything they could about it.
Huorong Security tracked the virus down to an open-source code editor on a website called Xixi Software Center. The script on the website was similar to the script used to send the ransomware, leading researchers to believe that the site was used as a channel to spread the WannaRen virus.
The ransomware discovered by the security team does two things to computers; it downloads a mining virus and a ransomware virus. WannaRen can spread through the "Eternal Blue" vulnerability in Windows and uses the same kind of asymmetric encryption that other ransomware viruses do. This means that there is currently no way to decrypt files without intervention from the threat actor.
The WannaRen script on Xixi software only spreads the mining virus, but it’s impossible to rule out the possibility of it spreading the ransomware in the future.
The ransomware virus has been detected and caught by the Huorong Security software. The software was able to intercept the ransomware and the transmission scripts it uses. Huorong has repeatedly warned users about the risks of using third-party download sites such as Xixi, which are often populated with viruses, malware, and ransomware. The group encourages people only to use official download channels and websites to download software and apps, a sentiment shared by many other security firms.
How Does WannaRen Spread?
Huorong says that the virus spreads through the use of a "hidden" virus transmission script. This malicious script is shown below;
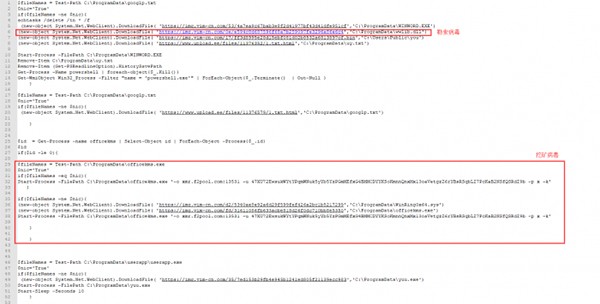
(malicious script)
When the virus is launched, it downloads several malicious modules, including the ransomware itself, the mining virus, and an attack tool for the eternal blue vulnerability. This attack module is used to spread malicious code through the network using the vulnerability as an attack vector.
Once the attack has succeeded, the virus runs a remote malicious script through the terminal and processes the ransomware virus.
WannaRen Ransomware's Operations
The WannaRen ransomware operates on a "white plus black" module. The script that spreads the virus downloads the "white plus black" modules and executes them. The virus then registers C:\ProgramData\WinWord.exe as a system service. This causes the computer to run the code and encrypt files once the computer restarts.
The virus code also causes the virus to be programmed into the system program so that it launches automatically every time the computer starts.
WannaRen uses symmetric and asymmetric (RSA+RC4) encryption that can’t be decrypted without a private decryption key. The ransomware creates the key and encrypts the files with it. Encrypted files are renamed to have the .WannRen suffix. After creating a decryption key, the virus imports the RSA public key to encrypt the original decryption key further.
WannaRen targets almost all files on a computer. The full list of files it encrypts is as follows:
doc, docx, xls, xlsx, ppt, pptx, pst, ost, msg, eml, vsd, vsdx, txt, csv, rtf, 123, wks, wkl, pdf, dwg, onetoc2, snt, jpeg, jpg, docb, docm, dot, dotm, dotx, xlsm, xlsb, xlw, xlt, xlm, xlc, xltx, xltm, pptm, pot, pps, ppsm, ppsx, ppam, potx, potm, edb, hwp, 602, sxi, sti, sldx, sldm, sldm, vdi, vmdk, vmx, gpg, aes, ARC, PAQ, bz2, tbk, bak, tar, tgz, gz, 7z, rar, zip, backup, iso, vcd, bmp, png, gif, raw, cgm, tif, tiff, nef, psd, ai, svg, djvu, m4u, m3u, mid, wma, flv, 3g2, mkv, 3gp, mp4, mov, avi, asf, mpeg, vob, mpg, wmv, fla, swf, wav, mp3, sh, class, jar, java, rb, asp, php, jsp, brd, sch, dch, dip, pl, vb, vbs, psl, bat, cmd, js, asm, h, pas, cpp, c, cs, suo, sln, ldf, mdf, ibd, my, myd, frm, odb, dbf, db, mdb, accdb, sql, sqlitedb, sqIite3, asc, lay6, otg, odg, uop, std, sxd, otp, odp, wb2, slk, dif, stc, sxc, ots, ods, 3dm, lay, mml, sxm, max, 3ds, uot, stw, sxw, ott, odt, pem, p12, csr, crt, key, pfx, der
The ransomware also generates a ransom note and a splash screen that informs victims on how to pay the ransom. The ransom note is titled "Please Decrypt This Text.gif," and the program to enter the decryption key is called "@WannaRen@.exe."
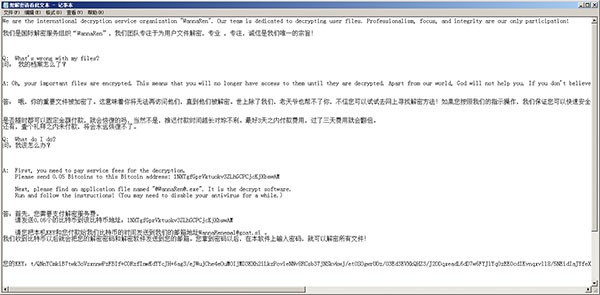
WannaRen Ransomware ransom note

WannaRen program
As noted before, WannaRen shares some similarities with the infamous WannaCry virus. WannaCry affected over 300,000 computers across 150 countries in 2017. The virus caused over $8 billion of damages and affected every industry. It’s unlikely that WannaRen will produce the same amount of damage, but this highlights the severity of malicious viruses and shows what they can do.

