EternalBlue
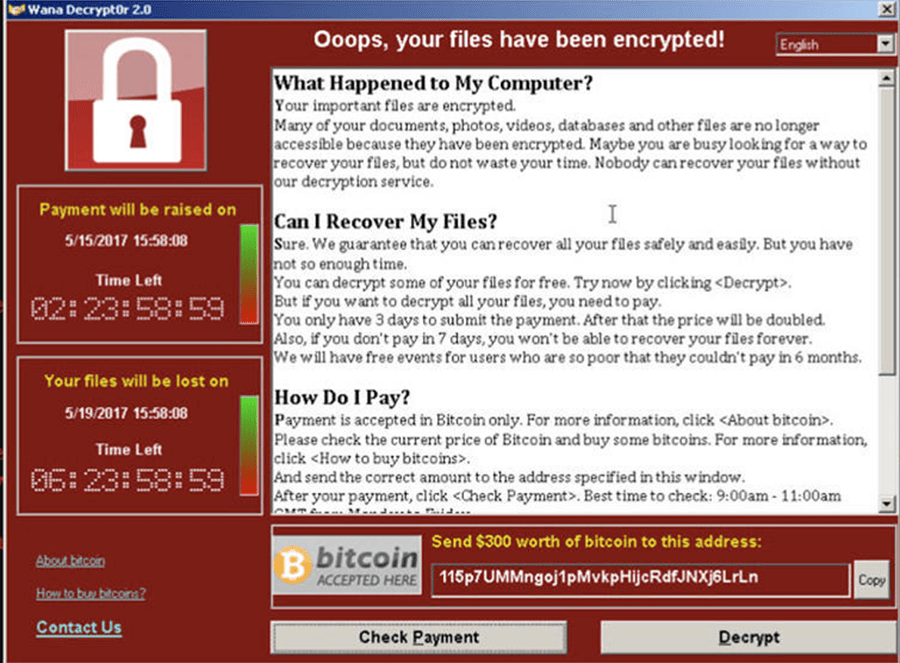
EternalBlue Image
The EternalBlue exploitation device isn't new since it was leaked in April 2017 by a group called 'The Shadows Brokers.' The EternalBlue exploitation device uses vulnerabilities in the implementation of the SMB protocol of Windows and can work on old versions that were used before the release of Windows 8 since they have an interprocess communication share (IPC$) that enables a null session. By using the null session, the criminals can create a connection using an anonymous login that enables the null session by default, allowing the server to receive multiple commands from the client.
The EternalBlue exploitation device exploits three bugs, the 'Non-paged Pool Allocation Bug,' the 'Wrong Casting Bug' and the 'Wrong Parsing Function Bug.' The Non-paged Pool Allocation Bug installs various threatening components on the infected machines and will attack the ones with frail passwords. The EternalBlue exploitation device also adds a Monero crypto miner, XMRig that will accomplish its main objective; crypt-mining. The EternalBlue exploitation device can also b used to execute many more tasks on the devices it infects. Computer users affected by it should use an anti-malware product to detect and remove the EternalBlue exploitation device from their machines immediately.

