Unlock92 Zipper Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 5 |
| First Seen: | July 22, 2018 |
| Last Seen: | July 23, 2019 |
| OS(es) Affected: | Windows |
The Unlock92 Zipper Ransomware is a generic file cryptor Trojan that was reported on July 19th, 2018. Samples of the cryptor revealed that it is based on the Unlock92 Ransomware from October 2017. The new version is dubbed Unlock92 Zipper Ransomware based on the act that the malware payload is delivered as a password-protected ZIP file. PC users may be proposed to open the malicious ZIP file and acquire a document with valuable information. However, that is a simple trick to convince the users to run the self-extracting ZIP file and install the Unlock92 Zipper Ransomware Trojan on their system.
The Unlock92 Zipper Ransomware is very similar to the Unlckr Ransomware and the Naampa Ransomware that belong to the same malware family. It is believed that Unlock92 Zipper Ransomware is not controlled by the same team behind the original project. The Unlock92 Zipper Ransomware is programmed to encipher data in a new way, and the researcher Michael Gillespie is confident the new variant can be decrypted. The threat is observed to take files in any given folder and put them in a password-protected ZIP container. The protected container is titled following the model
'Если хотите вернуть ваши файлы отправьте один небольшой архив и файл KEY.VL на e-mail: un92@protonmail.com
Если вы не получили ответа в течение суток то скачайте с сайта www[.]torproject[.]com браузер TOR
и с его помощью зайдите на сайт: hxxp://n3r2kuzhw2h7x6j5[.]onion - там будет указан действующий почтовый ящик.
Пароль для архива состоит более чем из 50 символов. На самостоятельный подбор уйдёт не один год.'
Translated into English:
'If you want to restore your files, send one small archive and file KEY.VL to e-mail: un92@protonmail.com
If you did not receive an answer within 24 hours then download the TOR browser from www[.]torproject[.]com
and with his help, go to the site: hxxp://n3r2kuzhw2h7x6j5[.]onion - there will be a valid mailbox.
The password for the archive consists of more than 50 characters. An independent attempt at recovery will take more than one year.'
Affected PC users may find the obfuscated decryption key titled 'KEY.VL' under the AppData folder and on the desktop. As mentioned above, you may be able to use help from Michael Gillespie via Twitter and recover your data. It is a bad idea to transfer money to the people behind the Unlock92 Zipper Ransomware. Most users may be comfortable using backup images and system recovery disks to rebuild their data. Infected machines should be cleaned with a reliable anti-malware instrument. Computer security companies mark related objects with the following tags:
Artemis!57931947A5AF
MSIL/Filecoder.OD
Ransom:Win32/Genasom
Ransom_ZIPPER.THGBOAH
TR/Genasom.qjmcf
Trojan-Ransom.MSIL.Agent.fqmw
Trojan-Ransom.Rokku
Trojan.IGENERIC
Trojan.Ransom.Unlock92
Trojan.Razy.D569D7
W32/Trojan.NTRA-3663
SpyHunter Detects & Remove Unlock92 Zipper Ransomware
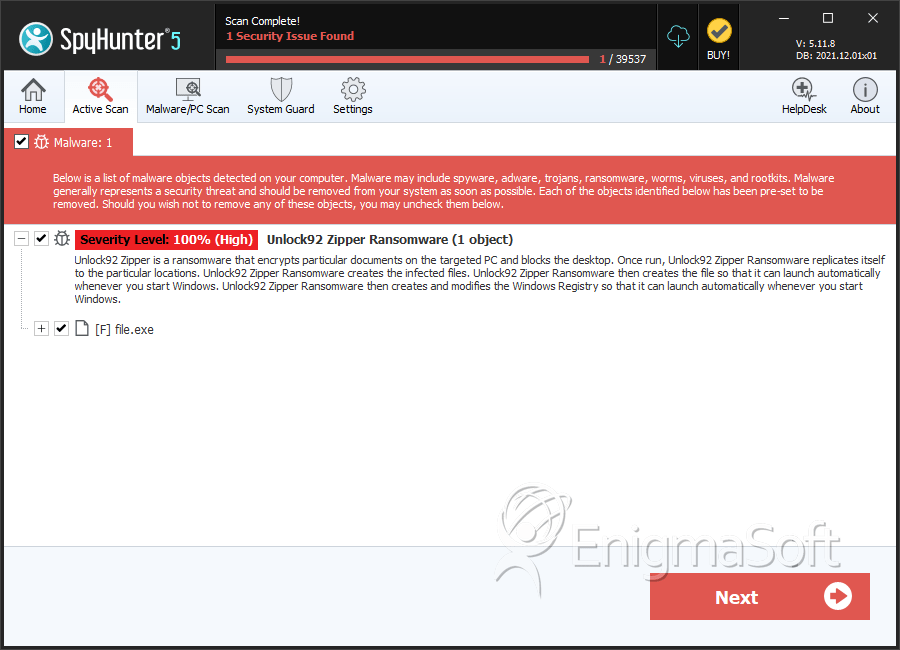
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | c9929a0ec2d9016b98dacbae20ff9431 | 1 |
| 2. | file.exe | 57931947a5afd6c9e7adc566ae88a4e6 | 1 |

