Topi Ransomware
Topi Ransomware Image
One of the newest copies of the STOP Ransomware is called the Topi Ransomware. The creators of the Topi Ransomware have borrowed the code of the notorious STOP Ransomware and altered it slightly to fit their needs. The STOP Ransomware family was the most active one throughout the entire 2019, with over 200 copies of the threat circulating the Web.
Table of Contents
Propagation and Encryption
Authors of ransomware threats tend to use a variety of infection vectors to propagate these nasty Trojans. It is likely that the most popular propagation methods are spam email campaigns. The attackers would send the targeted user an email that contains a message riddled with social engineering tricks. The o of the fake message is to trick the user into opening the file attached to the email. Usually, the attached file is macro-laced, and launching it would compromise one's system. Other commonly utilized propagation methods would include torrent trackers, fake software updates, malvertising, etc. The Topi Ransomware would target all the user's data and lock it securely using a complex encryption algorithm. All the files' names will be altered after the encryption process has been concluded. The Topi Ransomware appends a '.topi' bextension to the names of the newly locked files. For example, a file named 'jelly-bean.mp3' will be renamed to 'jelly-bean.mp3.topi.'
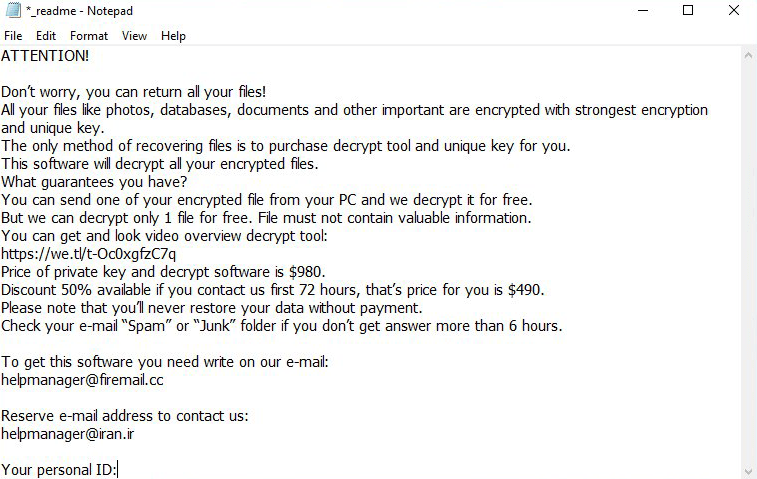
The Ransom Note
The Topi Ransomware's ransom note is named '_readme.txt,' which is a classic name used by most variants of the STOP Ransomware. jectiveIn the note, the attackers state that the ransom fee is $980. However, users who contact them within 72 hours successfully will get a 50% discount, meaning that the ransom fee will be reduced to $490. The attackers' preferred means of communication is via email. Two email addresses have been provided - 'helpmanager@iran.ir' and 'helpmanager@firemail.cc.'
It is never a good idea to contact cybercriminals or attempt to negotiate with them. These are not trustworthy individuals, and they would take your money gladly and disappear into the sunset without providing you with the decryption key they promised. This is why you should consider obtaining a reputable anti-malware service that will not only remove the Topi Ransomware from your PC but will also keep your system and your data secure.
Topi Ransomware Video
Tip: Turn your sound ON and watch the video in Full Screen mode.


