Skeleton Ransomware
The Skeleton Ransomware is an encryption ransomware Trojan that was first observed in early December 2017. The Skeleton Ransomware seems to belong to the same ransomware family that has been spawning threats such as the Blind Ransomware since September 2017. The Skeleton Ransomware, like most ransomware Trojans, is being delivered to victims through the use of spam email messages. These emails will often contain corrupted email attachments that impersonate email messages from legitimate sources such as social media platforms, online retailers, messaging companies or banks. The Skeleton Ransomware is downloaded and installed on the victim's computer when the victim opens the compromised email attachment.
Table of Contents
Describing the Skeleton Ransomware’s Actions
After the Skeleton Ransomware is installed, the Skeleton Ransomware begins encrypting the victim's files using a powerful encryption method that combines the AES and RSA encryptions. The Skeleton Ransomware's code uses a large quantity of open source resources, which have allowed the cybercrooks to create highly effective encryption ransomware Trojans with very few resources. This has resulted in an explosion of these attacks since 2014, making them some of the most common (and harmful) threats active currently. The Skeleton Ransomware will encrypt the victim's files to make them inaccessible, essentially taking them hostage up to the victim pays a large ransom amount. Unfortunately, the encryption used by the Skeleton Ransomware is quite strong, which means that it becomes almost impossible to recuperate the affected files without the decryption key, which the cybercrooks hold in their possession. The Skeleton Ransomware targets the file types mentioned below when it attacks a computer:
.3gp, .7z, .apk, .avi, .bmp, .cdr, .cer, .chm, .conf, .css, .csv, .dat, .db, .dbf, .djvu, .dbx, .docm, ,doc, .epub, .docx .fb2, .flv, .gif, .gz, .iso .ibooks,.jpeg, .jpg, .key, .mdb .md2, .mdf, .mht, .mobi .mhtm, .mkv, .mov, .mp3, .mp4, .mpg .mpeg, .pict, .pdf, .pps, .pkg, .png, .ppt .pptx, .ppsx, .psd, .rar, .rtf, .scr, .swf, .sav, .tiff, .tif, .tbl, .torrent, .txt, .vsd, .wmv, .xls, .xlsx, .xps, .xml, .ckp, .zip, .java, .py, .asm, .c, .cpp, .cs, .js, .php, .dacpac, .rbw, .rb, .mrg, .dcx, .db3, .sql, .sqlite3, .sqlite, .sqlitedb, .psd, .psp, .pdb, .dxf, .dwg, .drw, .casb, .ccp, .cal, .cmx, .cr2
The Skeleton that will Haunt Your Files
One of the ways the Skeleton Ransomware can be recognized easily is because the Skeleton Ransomware will rename affected files adding the file extension '.[skeleton@rape.lol].skeleton' to the end of each affected file's name. The Skeleton Ransomware also will create a text file named 'How_Decrypt_Files.txt' in each of the folders containing the files affected by the Skeleton Ransomware attack. This text file contains the Skeleton Ransomware's ransom note, which demands a ransom payment because they will need a decryption key to restore the affected files that will be supposedly delivered upon payment. Although it is unknown exactly how much money the criminals require to restore files affected by the Skeleton Ransomware currently, these ransoms are typically between 500 and 2000 USD and should be paid using Bitcoins. The full text of the Skeleton Ransomware's ransom note:
'Hello !
All your files have been encrypted !
If you want restore your files write on email - skeleton@rape.lol
In the subject write – ID-[redacted]'
Computer users that decide not to pay the Skeleton Ransomware ransom or contact the people responsible for the Skeleton Ransomware are taking the right decision. It is very unlikely that the cybercrooks will help the victims of the Skeleton Ransomware recover from the attack. In fact, they are just as likely to demand more money or target the victim for additional attacks (since the victim will have already shown a willingness to pay the Skeleton Ransomware ransom one time).
Protecting Your Data from the Skeleton Ransomware
The best way to protect your data from the Skeleton Ransomware is to have file backups. Having file backups on the cloud or a removable device means that you can restore your files after an attack immediately. This combined with a security program is the best protection against these attacks.
SpyHunter Detects & Remove Skeleton Ransomware
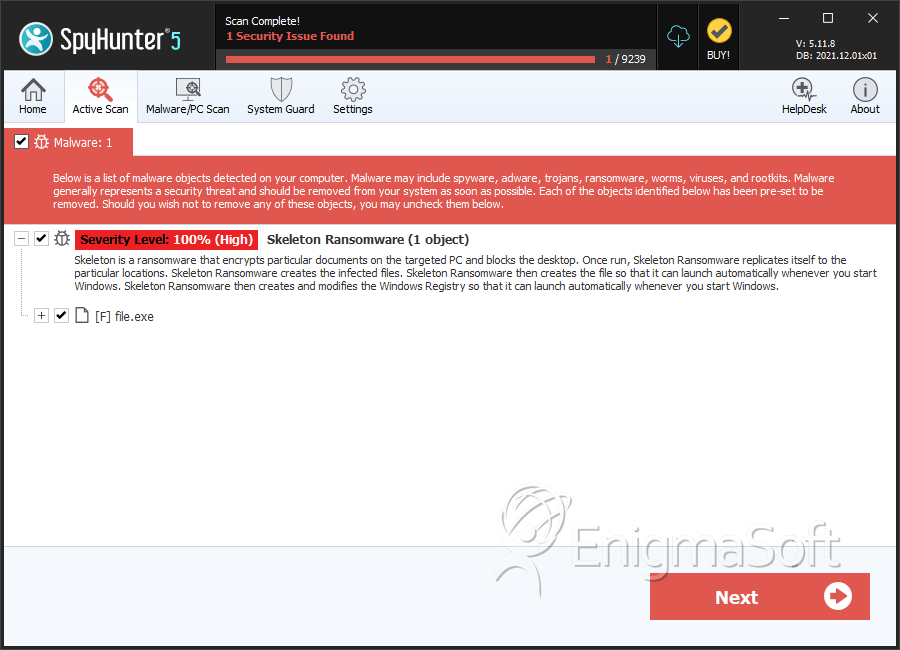
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | acff55cf4665f9412fc6951b89a0d33f | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.