ROGER Ransomware
ROGER Ransomware Image
Many cyber crooks are dabbling in the creation of ransomware threats, as this is often perceived as a quick way to make some cash with very little risk of facing any negative consequences. Most low-level cybercrimes tend to go unpunished, which only serves to tempt more shady individuals into taking part in illicit activities online. Among the most popular malware lurking on the Web are data-locking Trojans, also known as ransomware threats. One of the most operating ransomware families in the whole of 2019 is the Dharma Ransomware family. Recently, cybersecurity experts have detected a brand-new copy of the Dharma Ransomware called the ROGER Ransomware. Unfortunately, the Dharma Ransomware is still not decryptable via any free means, which means that the victims of the ROGER Ransomware cannot recover their data using a free decryption utility either.
Propagation and Encryption
The ROGER Ransomware is likely being propagated via fake software updates, torrent trackers, bogus pirated copies of legitimate software tools or mass spam email campaigns. However, for now, these remain as speculations as we do not have information to confirm the infection methods utilized in the distribution of the ROGER Ransomware. Once the ROGER Ransomware infiltrates your system, it will lock all the data present – images, audio files, documents, videos, presentations, spreadsheets, databases, archives, etc. Once the ROGER Ransomware locks a file, you will no longer be able to use it. All the files encrypted by the ROGER Ransomware will have their names altered. This file-locking Trojan appends a '.id-
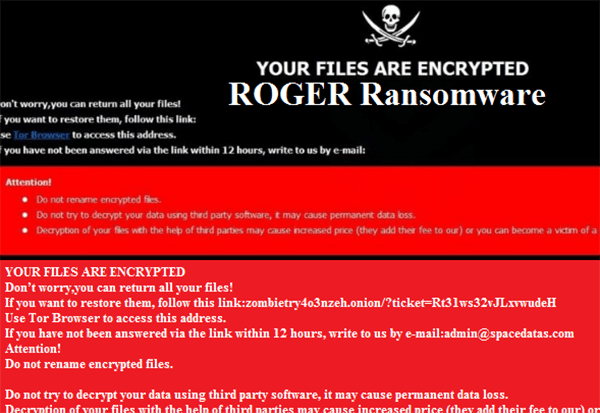
The Ransom Note
When the encryption process of the ROGER Ransomware is through, the threat will drop a ransom message that is located in two files called 'Info.hta' and 'FILES ENCRYPTED.txt.' The ransom message is rather concise. The authors of the ROGER Ransomware do not mention a specific sum, which will be required as a ransom fee, but you can be sure that they will attempt to blackmail you into giving them money. They make it clear that the transaction has to be made via Bitcoin. Most cyber crooks prefer to use cryptocurrencies instead of conventional payment methods, as this helps them maintain their anonymity and avoid punishment by the law. There is an email address provided for the victims – ‘backdata.company@aol.com.'
It is best to stay away from cyber crooks. Even victims who decide to pay the ransom fee are often left empty-handed as the cybercriminals usually lose interest in cooperating after they receive the payment that they demanded. If you have fallen victim to the ROGER Ransomware, you should consider using a reputable anti-virus solution to remove the threat from your computer safely.