RobinHood Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | August 4, 2017 |
| OS(es) Affected: | Windows |
RobinHood Ransomware Image
The RobinHood Ransomware (RobbinHood Ransomware or RobbinHood File Extension Ransomware) is a ransomware Trojan that is used to harass computer users under the pretext of raising awareness and funds for the people of Yemen. In fact, there is no evidence to support the theory that the creators of the RobinHood Ransomware have altruistic motives. It is likelier that the con artists are using the RobinHood Ransomware to profit in the same way that the creators of most encryption ransomware Trojans act today. However, the ransom demand in the case of the RobinHood Ransomware is extremely elevated, making it very unlikely that any individual PC users will pay the RobinHood Ransomware ransom in case of an attack. Take preventive measures against ransomware Trojans like the RobinHood Ransomware, which are becoming common increasingly.
This Week in Malware Episode 4: Robbinhood Ransomware
Table of Contents
Yemen Got a RobinHood Too
It is very little that's different about the RobinHood Ransomware infection. The RobinHood Ransomware is nearly identical to most other encryption ransomware Trojans; the RobinHood Ransomware will encrypt the victim's files and then demand a ransom payment in exchange for the decryption key necessary to recover the affected files. The RobinHood Ransomware includes messages claiming to serve the people of Yemen, referencing the killing of innocent people in Yemen by Saudi Arabia.
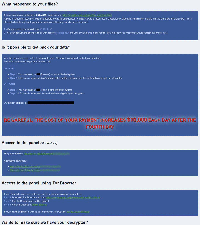
There are many ways in which the RobinHood Ransomware can be installed on victim's computers. The most common distribution method linked to the RobinHood Ransomware are corrupted websites and links, often distributed using spam email messages or tactics on social media. The RobinHood Ransomware includes a propaganda image rather than a standard ransom note, changing the victim's desktop image to reflect its aims of supposedly raising money for the people of Yemen. The RobinHood Ransomware will encrypt numerous files, especially targeting media files, photos, and documents associated with Microsoft Office. The RobinHood Ransomware's desktop image reads 'HELP YEMEN' and includes a message instructing victims to take several steps to recover. The RobinHood Ransomware also will drop a text file on the infected computer's desktop. This file, named 'READ_IT.txt' contains the following ransom note, which is displayed on the infected computer:
'HELP YEMEN
Bin Salman of Saudi Arabia is Killing poor and innocent people of Yemen by bombing , creating famine and disease!
You as a Saudian or a Supporter of their activities, are partner of his homicide. So you have been subjected to a ransomware attack and must accept one of the following:
a) Giving up all your information
b) Pay five Bitcoins to help Yemeni people.
bitcoin address = 1ENn1BelaKXBotiGuAFE1Yrin3e3vBjUAQH
and send transaction link to: decrypter.files@gmx.com
c) Use Tweeter to condemn Bin Selman for his crimes and ask him to stop the war against Yemen and make 100 users to retweet.'
The figure of five Bitcoin demanded by the RobinHood Ransomware is currently close to $14000 USD, making it very unlikely that regular computer users will pay the ransom amount to recover their files. Additionally, there is no evidence that the con artists will use these ransom amounts to help the people of Yemen. In fact, PC security analysts have dealt with 'altruistic' ransomware before, which make similar claims that the ransom amount will be used for charity or for a noble goal, when in fact there is no difference between the RobinHood Ransomware and other ransomware attacks.
Dealing with the RobinHood Ransomware Infection
The best way to deal with the RobinHood Ransomware and similar infections is to remove the RobinHood Ransomware threat completely with the help of a security program and then recover the files affected in the attack using file backups. Positively, file backups are the best protection against ransomware Trojans like the RobinHood Ransomware. PC security analysts strongly advise computer users to keep the copies of their files updated regularly on a mobile memory artifact or the cloud. Having access to backups undoes the con artists' strategy, giving computer users a way to recover their files after an attack.
RobinHood Targets Each System Individually
Malware researchers have managed to reverse engineer one of the scarcely available samples of RobinHood ransomware, and their analysis has revealed some interesting features. Upon execution, the malware uses a specific command to disconnect all network shares from the infected computer, meaning that other computers from the same network are not encrypted via connected shares. Rather, RobinHood targets each machine individually, which indicates that the attackers push the malicious payload to each individual computer through a domain controller or a framework like EmpirePowerShell or PSExec. Then, the malware attempts to read an RSA encryption key from the Windows Temporary folder.
If it is unable to find such key, RobinHood displays a message that the system cannot find the specified file and then quits its execution. If the searched key is present, however, the ransomware continues with the file encryption. As a next step, the malware quits 181 Windows services related to database, antivirus, and mail server programs, as well as to any other software that could keep files open and prevent their encryption. Next, during this preparation phase, RobinHood clears event logs, Shadow Volume Copies and disables the Windows automatic repair function.
RobinHood Creates Four Ransom Notes
After everything is ready, RobinHood starts the actual encryption, creating an AES key for each file. Then, the AES key is locked up, while the original file name is encrypted with the public RSA key and altered to "Encrypted_[randomstring].enc_robbinhood" (for example: Encrypted_b0a6c73e3e434b63.enc_robinhood"). This ransomware skips files in certain directories, like Program Data, Windows, Boot, Temp, Program Files, tmp, AppData, System Volume Information, and others. Another uncommon feature of RobinHood is that it creates numerous log files named "rf_s," " ro_l," and "ro_s" in the C:\Windows\Temp folder, which are deleted after encryption is complete. The "rf_s" file logs the creation of ransom notes in each folder, however, the purpose of the other log files is not known yet. In some cases, a final message "Done, Enjoy buddy:)))" appears to indicate that encryption has been completed.
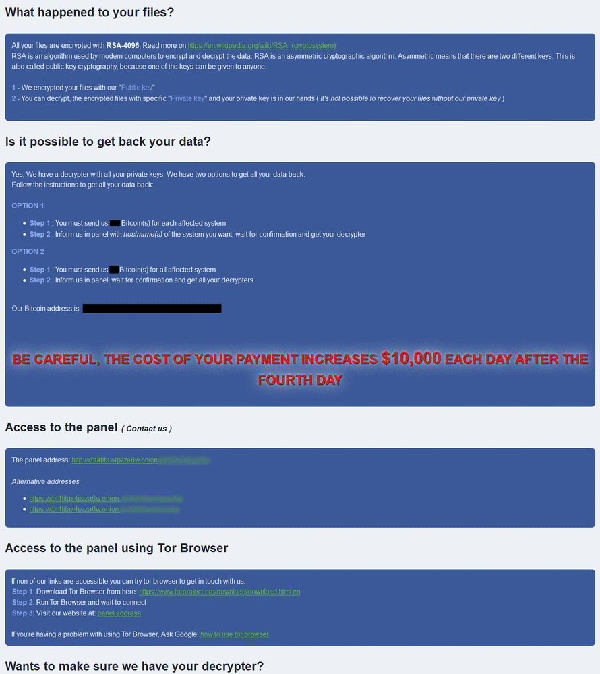
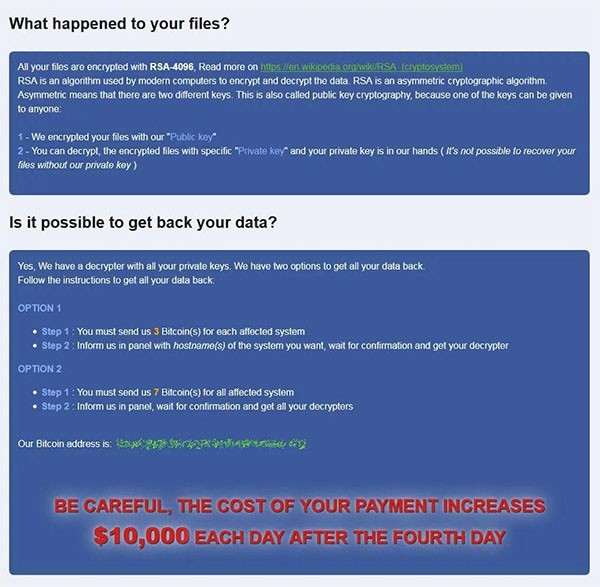
During the encryption process, the ransomware creates four different ransom notes named "_Help_Help_Help.html," " _Decrypt_Files.html," " _Help_Important.html," and "_Decryption_ReadMe.html." These ransom notes inform the victim about what has happened to their files and state the Bitcoin address that should be used to make the ransom payment. The latest variants of RobinHood demand 3 Bitcoin for the decryption of one affected system, and 13 Bitcoin for the entire network. Some of the older variants demanded 7 Bitcoin for all affected systems.
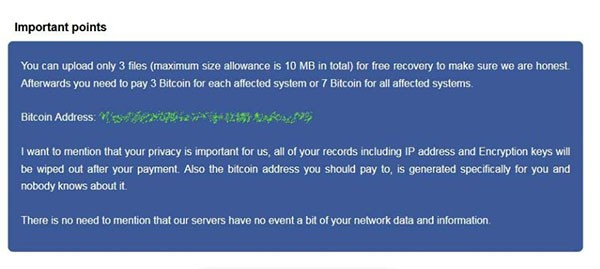
There are also reports which claim that some RobinHood samples threaten to impose a $10,000 penalty per day to victims who do not pay, starting from the fourth day of encryption. Another interesting detail that is not observed in many ransomware threats out there is a surprising claim made by its creators. They state they value the victim’s privacy and would delete all data related to a particular user, like IP addresses or encryption keys, as soon as the ransom payment has been made. Also, RobinHood’s contact page says that ransom payments cannot be tracked as an individual Bitcoin address is set up freshly for each victim. The attackers insist on honesty as well - they offer to decrypt three files of up to 10 MB for free.
Significant Attacks of RobinHood Ransomware
One of the known major attacks of RobinHood happened on May 7, 2019, when Baltimore’s city government got paralyzed for weeks. News agencies reported at that time that the servers of the city’s administration had been breached by a hacking tool developed by the National Security Agency which had landed in the hands of cybercriminals. Later, it was confirmed that the incident was caused by RobinHood Ransomware.
As a result of the attack, the city’s entire digital content had been locked so that the government emails were down, no real estate transactions could be processed, and no payments to city departments could be made online. Baltimore City Mayor stated that the city would not pay the demanded ransom of 13 Bitcoin (equal to $100,000), while the FBI and the Secret Service started an investigation. Another RobinHood attack affected the network of the City of Greenwell, North Carolina in April 2019. Responsible law authorities and cybersecurity experts are currently working on that case as well.
June 2020 Update:
Recently, the RobinHood ransomware family was observed using an encryption strategy that isn't hindered by endpoint protection software. The threat actors behind RobinHood managed to subvert a setting in kernel memory in Windows 7, 8, and 10 to achieve it.
The module that the actors are using to kill encountered endpoint protection software consists of several files, all embedded into STEEL.EXE. The files are extracted to C:\WINDOWS\TEMP.
- STEEL.EXE – The kill application that kills processes and files of detected security products, using kernel drivers.
- ROBNR.EXE – A driver installer that deploys the signed third party driver and the criminal unsigned kernel driver. Once the unsigned driver is implemented, it gets loaded using a known vulnerability in the third-party driver.
- GDRV.SYS – A vulnerable kernel driver, an outdated Authenticode-signed driver that contains the vulnerability exploited by RobinHood.
- RBNL.SYS – A malicious kernel driver, the one that kills the processes and deletes files from kernel space.
- PLIST.TXT – A list of processes and their files destroyed by the malware. That is a text file with the names of the applications the malicious driver is after, virtually a kill list. It is not embedded in STEEL.EXE and may be tailored on a case-by-case basis.
STEEL.EXE
The STEEL.EXE application is the one killing processes and deleting files of installed security applications. To make that possible, STEEL.EXE deploys its driver. The driver runs in kernel mode, making it ideally positioned to take on processes and files without being caught by endpoint protection and security controls. Although endpoint security products run under NT AUTHORITY/SYSTEM, most of them are running in userspace.
The STEEL.EXE application deploys ROBNR.EXE, which in turn installs RBNL.SYS, the malicious unsigned driver that comes with the malware. Once the driver is installed, STEEL.EXE reads from the PLIST.TXT file and sends instructions to the driver. That deletes any of the applications listed within, essentially killing the processes. If the process is running as a service, the service is blocked from automatically restarting, as the file gets deleted.
Once STEEL.EXE exits, the ransomware may perform an encryption attack without any issues, since the security applications on the device are taken out for good, giving itself free rein.
ROBNR.EXE
This application is dropped on the disk when STEEL.EXE is present. That is an application that cuts and installs the vulnerable driver GDRV.SYS, as well as the malicious RBNL.SYS driver. 64 bit Windows devices have a mechanism that enforces driver signatures, meaning Windows only allows drivers to load when both Microsoft and the manufacturer signed them. That is necessary for all drivers so they can be loaded on 64 bit Windows machines.
The malware authors didn't care to sign the malicious driver since that involves a purchasing certificate. Such certificates may be revoked by the certificate authority, making the driver irrelevant, as it cannot be accepted by Windows anymore.
The malware authors went with a different tactic, using the properly signed third party driver GDRV.SYS, as it contains a privilege escalation vulnerability. That allows it to read and write arbitrary memory. The threat actors used that to abuse the vulnerability, temporarily disabling driver signature enforcement in Windows within the kernel memory. Once that's done, the attackers get their foot in the door and load their malicious, unsigned driver.
New Versions of RobinHood:
- Version 0.3: First spotted on February 27, 2020, it has a reference to a folder called Robinhood2. It drops the obfuscation, though it keeps the embedded text in an encoded form. It is now capable of erasing event logs and using pattern matching to discover and kill services, no longer using hardcoded values. That allows RobinHood to disable anti-malware software with greater effectiveness.
- Version 0.4: First seen on April 24, 2020. Many changes were implemented since 0.3, with this version referencing to a folder called Robbinhood6.1. The added functions make some radical changes in the overall architecture of the program, going back to a hardcoded list of processes and services. The list is now designed to stop services that write data constantly, such as databases.
SpyHunter Detects & Remove RobinHood Ransomware
RobinHood Ransomware Screenshots
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | ROBINHOOD-TIMER.exe | 780bdefbb37fe6df3f303304e4bf0ce9 | 1 |
| 2. | file.exe | 493edc98d300ffbfe3fb8d87e970f84f | 0 |