Ra Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 18 |
| First Seen: | July 17, 2018 |
| Last Seen: | September 15, 2018 |
| OS(es) Affected: | Windows |
The Ra Ransomware is an encryption ransomware Trojan that was observed on July 9, 2018. The Ra Ransomware is delivered to victims through the use of corrupted phishing email messages containing a file attachment that uses embedded macros to download and install the Ra Ransomware onto the victim's computer. Because of this, learning how to recognize spam email tactics and handle unsolicited email attachments is a fundamental part of preventing attacks like the Ra Ransomware.
Table of Contents
How the the Ra Ransomware Attack Works
Once the Ra Ransomware is installed on the victim's computer, the Ra Ransomware will use the RSA and AES encryptions to make the victim's files inaccessible. The Ra Ransomware will target a wide variety of the user-generated files, which may include media files, documents, databases, configuration files, archives, and numerous other file types. The files that threats like the Ra Ransomware will target in their attacks include:
.ebd, .jbc, .pst, .ost, .tib, .tbk, .bak, .bac, .abk, .as4, .asd, .ashbak, .backup, .bck, .bdb, .bk1, .bkc, .bkf, .bkp, .boe, .bpa, .bpd, .bup, .cmb, .fbf, .fbw, .fh, .ful, .gho, .ipd, .nb7, .nba, .nbd, .nbf, .nbi, .nbu, .nco, .oeb, .old, .qic, .sn1, .sn2, .sna, .spi, .stg, .uci, .win, .xbk, .iso, .htm, .html, .mht, .p7, .p7c, .pem, .sgn, .sec, .cer, .csr, .djvu, .der, .stl, .crt, .p7b, .pfx, .fb, .fb2, .tif, .tiff, .pdf, .doc, .docx, .docm, .rtf, .xls, .xlsx, .xlsm, .ppt, .pptx, .ppsx, .txt, .cdr, .jpe, .jpg, .jpeg, .png, .bmp, .jiff, .jpf, .ply, .pov, .raw, .cf, .cfn, .tbn, .xcf, .xof, .key, .eml, .tbb, .dwf, .egg, .fc2, .fcz, .fg, .fp3, .pab, .oab, .psd, .psb, .pcx, .dwg, .dws, .dxe, .zip, .zipx, .7z, .rar, .rev, .afp, .bfa, .bpk, .bsk, .enc, .rzk, .rzx, .sef, .shy, .snk, .accdb, .ldf, .accdc, .adp, .dbc, .dbx, .dbf, .dbt, .dxl, .edb, .eql, .mdb, .mxl, .mdf, .sql, .sqlite, .sqlite3, .sqlitedb, .kdb, .kdbx, .1cd, .dt, .erf, .lgp, .md, .epf, .efb, .eis, .efn, .emd, .emr, .end, .eog, .erb, .ebn, .ebb, .prefab, .jif, .wor, .csv, .msg, .msf, .kwm, .pwm, .ai, .eps, .abd, .repx, .oxps, .do.
The Ra Ransomware is designed to rename any files compromised by the attack, adding a string of five random letters as a new file extension to the affected files and scrambling the name of the affected files using base64. The Ra Ransomware delivers a ransom note in the form of an HTML file named 'Recovery instructions.html,' which is dropped on the infected computer. The Ra Ransomware ransom note reads as follows:
'All your files are belong to us!
All your personal files, including, but not limited to:
Photos, videos, databases and office projects have been encrypted using a mix of two very strong cryptographic algorithms – AES-128 and RSA-1028. Original files have been overwritten, recovery tools and software will not help you.
The only way to recover your files, are to meet our demands.
Be warned, we won't be able to recover your files if you start fiddling with them.
You have 120 hours (5 days) from this moment to send us payment, or you files will be lost in eternity.
To start the recovery process you need to download and install the Tor browser, which is easily done from their own home-page.
Once you have the Tor browser running you need to navigate to hxxp://recovery6m3lvkxg[.]onion and then input your personal id displayed below.
Further payment instructions will be given once logged in.'
Malware specialists strongly advise computer users against connecting to the Ra Ransomware's payment portal, since paying the Ra Ransomware ransom allows the criminals to continue developing and releasing Ra Ransomware variants.
Protecting Your Data from Threats Like the Ra Ransomware
The best protection against these threats is to have file backups, stored on external devices, such as the cloud. Apart from file backups, PC security researchers recommend that computer users have a security program. Since the Ra Ransomware is delivered using spam email messages, learning to deal with this content kind is also important.
SpyHunter Detects & Remove Ra Ransomware
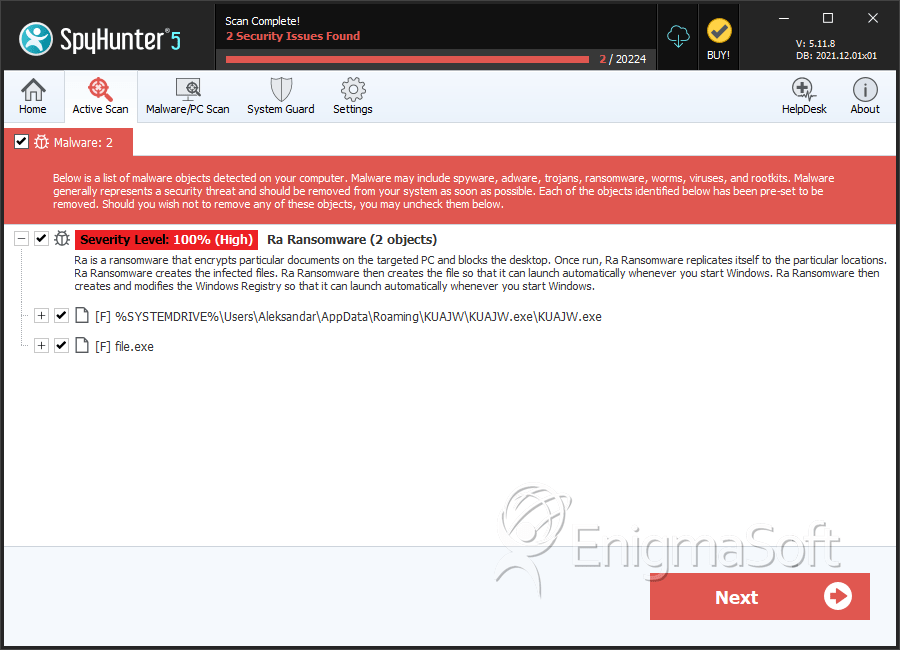
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | KUAJW.exe | 550a730bfcb7d164765fd8894548d375 | 14 |
| 2. | file.exe | c33c8eb72c1dbd7cdab54da0273ba679 | 0 |

