Nemucod Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 24,272 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 684 |
| First Seen: | April 27, 2016 |
| Last Seen: | January 9, 2026 |
| OS(es) Affected: | Windows |
The Nemucod Ransomware is a variant of the Nemucod family that includes a ransomware component. The Nemucod is a well-known threat family composed by threatening Java scripts. A variant of the Nemucod downloads a variant of TeslaCrypt, referred to by malware researchers as the Nemucod Ransomware. The Nemucod Ransomware poses a real threat to computer users, and steps should be taken to ensure that your machine is not vulnerable to threats like the Nemucod Ransomware.
Table of Contents
The Damage that may be Caused by a Code-Based Ransomware
These Nemucod variants include code that allows them to drop ransomware on an affected computer. The Nemucod Ransomware may be distributed using spam email messages that contain encrypted JavaScript attachments. When the JavaScript is decrypted, it tries to download a corrupted file. This file is a threatening executable file for the Nemucod Ransomware which will try to encrypt the victim's files. After the Nemucod Ransomware has finished encrypting the victim's files, it drops a ransom note in the form of a text file with instructions on carrying out payment. The Nemucod Ransomware, like other encryption ransomware Trojans, searches for files of a certain type on the victim's computer and then encrypts them. The Nemucod Ransomware targets documents, media files, images and other files. After a file is encrypted, the Nemucod Ransomware changes its extension to '.crypted,' making it clear that the Nemucod Ransomware is a variant of TrueCrypt. The Nemucod Ransomware encompasses two infections in one; after it has completed its attack, the Nemucod Ransomware will connect to a remote server and download additional threats on the victim's computer.
Good and Bad News Related to the Nemucod Ransomware
The good news about the Nemucod Ransomware is that the Nemucod Ransomware does not use RSA-1024 encryption, like more sophisticated ransomware Trojans. The Nemucod Ransomware only encrypts the first 2048 bytes of each file using the XOR encryption and a pre-defined key that is embedded in the corrupted executable file. However, even though it is relatively simple, the Nemucod Ransomware can still encrypt the victim's files. The Nemucod Ransomware serves as a successful amalgamation of encryption ransomware Trojans with the pre-existing family of JavaScript Trojans. This is possibly bad news since it's likely that the people responsible for the Nemucod Ransomware and other the Nemucod threats may be planning to increase the severity of these attacks.
Additional Information Regarding the Nemucod Ransomware
Our PC security researchers have observed that the Nemucod Ransomware is very similar to the KeyBTC Ransomware. However, the Nemucod Ransomware seems to be a simpler implementation of this ransomware Trojan's component. It is currently unknown if there is a direct relationship between the people responsible for the Nemucod Ransomware and the KeyBTC Ransomware, or if they simply copied the code from one to the other. Fortunately for computer users, the Nemucod Ransomware uses the XOR encryption, meaning that it is possible to decrypt the files without having to obtain the decryption key from the threat's creators. If your files have been encrypted by the Nemucod Ransomware, PC security researchers recommend the following measures to help with recovery:
- Files encrypted by the Nemucod Ransomware can be recovered with the XOR key that is embedded in the threat executable (a 255 character key). It is possible that a decryption utility has been made available by security researchers.
- Affected PCs can be restored using System Restore, which is usually disabled by more sophisticated ransomware Trojan variants.
- Files encrypted by the Nemucod Ransomware can be restored using Shadow Volume copies, which are deleted by more advanced ransomware Trojans. To do this, it may be necessary to download and run a Shadow Volume browser or recovery utility that can find the shadow copies of files that were encrypted.
SpyHunter Detects & Remove Nemucod Ransomware
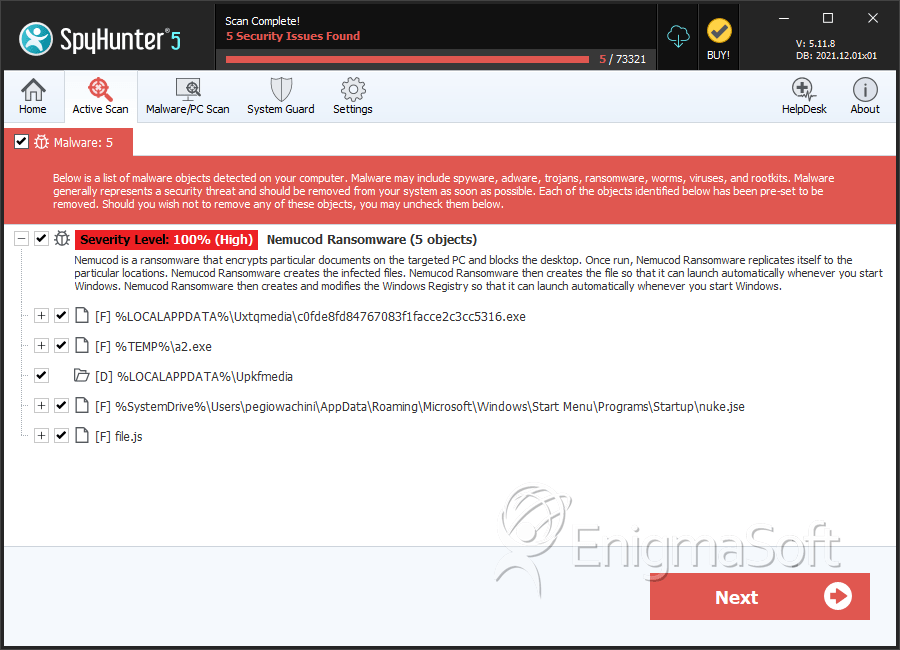
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | c0fde8fd84767083f1facce2c3cc5316.exe | c0fde8fd84767083f1facce2c3cc5316 | 93 |
| 2. | a2.exe | 3e1634d65e61bec012dffed6eef042c2 | 19 |
| 3. | nuke.jse | e56ac7e5354df06673495d6da96cd8ef | 1 |
| 4. | file.js | ba44cb88fb6b3d68a0198ad29ad9f27b | 0 |
Registry Details
Directories
Nemucod Ransomware may create the following directory or directories:
| %LOCALAPPDATA%\Upkfmedia |