MegaCortex Ransomware
MegaCortex Ransomware Image
MegaCortex is a strain of ransomware that first appeared in early 2019. However, in the first week of May 2019, security researchers with Sophos noticed a very significant spike in attacks where MegaCortex was used. The attacks were targeted at victims all over the globe, from Europe to Canada and the US. The attack vector that MegaCortex uses has become more advanced over time and currently employs both manual and automated techniques, with the automated part of the process dedicated to infecting as many systems on the network as possible. In this sense, MegaCortex is similar to the Ryuk ransomware that also relied on some hands-on work and probing for system holes, then stealing credentials, before the automated attack spread the ransomware.
Table of Contents
The Ransomware from the Matrix
The name MegaCortex is likely an intentional misspelling of MetaCortex - the fictional software corporation that Keanu Reeves' Neo from the Matrix movie worked for.
According to the findings and report published by Sophos, the attackers used a red team script to call up a reverse shell on the victim network. Red teams, in terms of cyber security, are independent organizations that can be hired to challenge a company's security, testing it and attacking it the way a bad actor would, within a controlled environment and for the benefit of the client. Once the revere shell is activated, the bad actors behind MegaCortex run PowerShell scripts as well as remotely hosted batch files that cause MegaCortex to deploy secondary payloads, originally embedded in the ransomware.
Sophos also note that there is a possible connection between MegaCortex and the Emotet and Qbot malware, as the networks hit by MegaCortex had Emotet and Qbot on them when examined. Since both Emotet and Qbot can serve as vehicles for a separate payload, it is possible that they may have been instrumental in the infections, but there is no direct evidence of it.
How MegaCortex Infiltrates Its Victims
In one instance of the attacks, the point of entry was a domain controller. The attackers seem to have previously stolen the credentials for the domain controller, as part of the direct, manual approach to the attack. MegaCortex uses a batch file to shut down running software and kill processes that might interfere with its execution and are linked to system security and anti-malware solutions - something that almost all current ransomware are doing to ensure uninterrupted operation. A total of 44 processes, 189 services are terminated, then 194 services are set not to start up on boot.
The full package delivered to the victim consists of the batch file, an executable named rstwg.exe that is really a copy of PsExec, as well as the main executable of the ransomware. Once the batch file shuts down all it can and makes sure the services don't start again, the main executable named winnit.exe (possibly another intentional misspelling of wininit.exe, a legitimate Windows process) is called up with a command-line argument that consists of encoded data. This causes winnit.exe to drop and run a DLL payload that is given a name of eight random letters. This is the module that performs the actual encryption. Sophos also reports finding another bunch of batch files named 1.bat through 6.bat that are intended to spread the winnit.exe payload around the network.
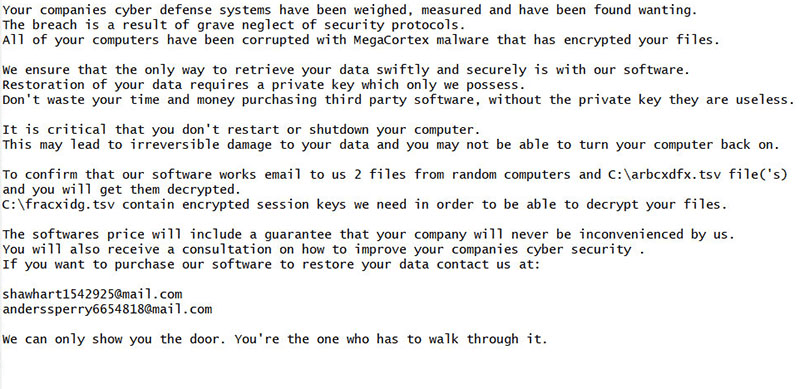
MegaCortex drops its ransom note in the root directory of the system hard drive, in the form of a plain text file. Here is the full text of the note:
Your companies cyber defense systems have been weighed, measured and have been found wanting.
The breach is a result of grave neglect of security protocols.
All of your computers have been corrupted with MegaCortex malware that has encrypted your files.
We ensure that the only way to retrieve your data swiftly and securely is with our software.
Restoration of your data requires a private key which only we possess.
Don't waste your time and money purchasing third party software, without the private key they are useless.
It is critical that you don't restart or shutdown your computer.
This may lead to irreversible damage to your data and you may not be able to turn your computer back on.
To confirm that our software works email to us 2 files from random computers and C:\[8-letter filename].tsv file('s)
and you will get them decrypted.
C:\[8-letter filename].tsv contain encrypted session keys we need in order to be able to decrypt your files.
The softwares price will include a guarantee that your company will never be inconvenienced by us.
You will also receive a consultation on how to improve your companies cyber security .
If you want to purchase our software to restore your data contact us at:
shawhart1542925 at mail.com
anderssperry6654818 at mail.com
We can only show you the door. You're the one who has to walk through it.
The .tsv file generated by MegaCortex has the same name as the malicious DLL mentioned above. The file itself contains records of each encrypted file, along with a string encoded in base64 and two separate 40-character hexadecimal strings. According to the ransom note, those are "encrypted session keys" that the criminals claim they need to decrypt the victim's files. There is no specific ransom demand listed in the note, possibly to give the bad actors behind MegaCortex more flexibility to tailor the ransom sum depending on the type and size of enterprise that is being attacked.
Encrypted Files and Extensions
At least one instance of a MegaCortex infection used the ".aes128ctr" extension to mark encrypted files, appending the extension after the original one. In this way, a file named "invoice.pdf" will become "invoice.pdf.aes128ctr" once MegaCortex has encrypted it. The extension implies the ransomware might use AES-128 encryption but this has not been confirmed. It's also not known whether the extensions are static and are used in all attacks or different attacks use different extensions.
As with every ransomware, despite the professional tone of the ransom note, there is no guarantee that a victim of MegaCortex will ever get their files back even if they pay any named ransom. At the moment, there is no decryption tool that can restore files scrambled by MegaCortex.
A newer version of MegaCortex, dubbed MegaCortex 2.0, was released recently, equipped with anti-analysis features, alongside a slew of other capabilities. The new variant has added functionality that allows the attackers to kill security service functionality. That was something done manually by the original threat by executing batch scripts on each infested host individually.
The people behind the new variant of MegaCortex decided to stay away from using a custom password used during infection. Although this feature allowed them to hide the inner workings of the malware, it also prevented the threat from reaching more targets. It was necessary for the handlers of the ransomware to manually execute specific actions on each targeted network, which slowed down the rate of infection. This problem changed with this new version by using a hardcoded password inside the malware binary.



