MacRansom Ransomware
MacRansom is a malware kit offered as Ransomware-as-a-Service (Raas) that has been attacking MacOS-based machines since 2017. The threat lives on to this day thanks to a constant inflow of affiliate hackers who obtain MacRansom builds from its creators through a TOR-hosted web portal. MacRansom can either run at a predetermined trigger date or self-execute upon plugging an external drive to a USB socket. In most cases, victims must pay 0.25 BTC (approx. $2,860 as of Aug. 2020) to recover their files.
Infection Vectors
MacRansom's developers do not offer it directly on the dark web. They provided it on demand using a TOR-based web portal. Cybercriminals who obtain a MacRansom build do not lack any incentive to establish contact — the actors behind MacRansom promise to give back 70% of the required compensation provided that the victim agreed to pay. What is more, MacRansom is said to leave no digital footprints whatsoever, which gives attackers a fair chance to get away from a potential criminal charge. Once a hacker has got hold of MacRansom, he or she would either need to have physical access to the targeted MacOS machine or lure the victim into getting it from an email attachment or via Apple's AirDrop service. The latter option is available for an additional fee.
How MacRansom Works
A MacRansom infection starts when it reaches its 'trigger time.' The latter may launch at a fixed date or upon mounting an external USB drive, depending on the client's order. Either, MacRansom will first perform a series of checks to make sure that it:
- Runs on a dual-core MacOS-based machine.
- Has not landed on a debugger.
If those two conditions are at hand, MacRansom generates a launch point hidden behind a genuine-looking file in ~/Library/LaunchAgents/com.apple.finder.plist. That's when the countdown to trigger time begins. MacRansom then scans the user's system for files bigger than 8 bytes in size before applying a symmetric encryption algorithm. Here's what the ransom note looks like:
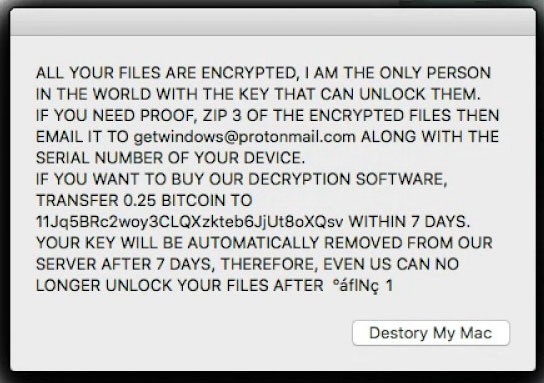
MacRansom alert message image
MacRansom note text:
"All your files are encrypted. A am the only person in the world with the key that can unlock them. If you need proof, zip 3 of the encrypted files then email it to getwindows@protonmail.com and the serial number of your device. If you want to buy our decryption software, transfer 0.25 Bitcoin to [random_characters] within 7 days. Your key will be automatically removed from our server after 7 days, therefore, even us can no longer unlock your files after [random_characters]."
There are two flaws in the note above, though. First, MacRansom can only encrypt as many as 128 of the victim's files. Second, MacRansom does not communicate with a remote C&C server, which implies that the decryption key is only available on the victim's machine. The crooks in charge may have no copy of it stored on another server, contrary to what they claim in the note. Nevertheless, researchers are confident that a brute-force attack should break the symmetric encryption algorithm, as long as you act before MacRansom terminates.

