LookBack
 Recently, there has been a series of attacks targeting various companies and institutions located in the United States and dealing in the utility industry. The attackers use phishing emails to propagate their threat. These emails would claim to be sent by the National Council of Examiners for Engineering and Surveying and are designed to look legitimate carefully and not raise any red flags. The emails would state that the recipient has failed to meet the standards set by the organization. They offer further information on the issue which is supposedly contained in the '. DOC' file, which is attached to the fraudulent email. This appears to be the work of a high-end group of cyber crooks, and some malware researchers speculate that an APT (Advanced Persistent Threat) may be responsible for these attacks.
Recently, there has been a series of attacks targeting various companies and institutions located in the United States and dealing in the utility industry. The attackers use phishing emails to propagate their threat. These emails would claim to be sent by the National Council of Examiners for Engineering and Surveying and are designed to look legitimate carefully and not raise any red flags. The emails would state that the recipient has failed to meet the standards set by the organization. They offer further information on the issue which is supposedly contained in the '. DOC' file, which is attached to the fraudulent email. This appears to be the work of a high-end group of cyber crooks, and some malware researchers speculate that an APT (Advanced Persistent Threat) may be responsible for these attacks.
LookBack's activities were noticed between July 19 and July 25 2019 when spear phishing emails were found targeting three US utilities companies. The emails were attempting to claim they were a US-based engineering licensing board. The emails were coming from what seemed to be a domain controlled by the threat actors – nceess[dot]com. The attempt was to make a website that attempts to impersonate the US National Council of Examiners for Engineering and Surveying. The email contained a malicious Microsoft Word attachment, one that installs and runs the LookBack malware. LookBack is a combination of a remote access trojan (RAT) and a mechanism used for command and control communications with the servers used by the threat actors. The document attachment in the email had the file name 'Result Notice.doc'.
Initially, this seems like an attack similar to the one that affected the Gundremmingen nuclear plant in Germany, but upon closer inspection it appears to be nothing but a phishing scam paired with a remote access Trojan. There appears to be a possible connection to the APT10 threat actor, as a similar set of VBA macros was used in the APT campaigns against Japanese companies in 2018, but there is no solid proof that the same threat actors are behind this campaign. The scam emails attempt to look as legitimate as possible, even going so far as to include their own logo, as discovered by security firm ProofPoint:

All emails were originating from the IP 79.141.168[.]137, which seems to be the IP used by the threat actors to host their phishing domain. Examination of the passive DNS and domain registration history revealed more domains registered by the same threat actor, also attempting to impersonate electric and engineering licensing bodies within the United States. Out of the domains involved in these activities, only nceess[dot]com was observed as active in the phishing campaign.
The Word attachment uses VBA macros to install the LookBack malware. Once the attachment is executed, the VBA macro drops three Privacy Enhanced Mail (PEM) files onto the host – tempsodom.txt, tempgup2.txt and tempgup.txt. Additionally, the macro creates a copy of the decoded PEM files, restoring their proper extensions in the process. Tempgup.txt gets changed to GUP.exe, which impersonates an open source binary used by Notepad++, tempsodom.exe becomes Sodom.txt, containing the command and control configuration data the malware uses. Finally, tempbup2.txt gets renamed to libcurl.dll, which is a malicious loader DLL that becomes part of the package.
Table of Contents
The LookBack Malware
LookBack at its core is a remote access Trojan, one written in C++ that relies upon a proxy communication tool to send off data on infected hosts to a command and control server. LookBack can view processes, system and file data, execute commands, take screenshots, record mouse movement and clicks, delete files. It can also reboot the system and it may even delete itself from infected hosts to hide its tracks after the job is done. The malware contains the following components:
GUP – the command and control proxy tool
A malware loader that uses a legitimate libcurl.dll file with a modified function to execute shellcode.
The SodomNormal communication module, which creates the C&C channel used by the GUP proxy tool.
The SodomMain remote access Trojan component delivered after decoding the initial beacon response received via the GUP proxy tool and the SodomNormal host proxy.
The complete and very similar method of attack to that of APT10 was visualized below, courtesy of FireEye:
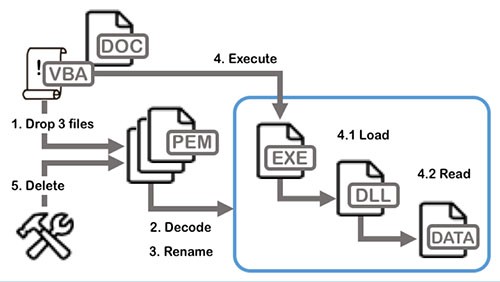
In conclusion, the detection of a new malware family aimed at United States utility companies hints of a potential state actor behind the campaign, such as the tactics used by APT10 back in 2016 and 2018. Though a definitive attribution to a specific actor cannot be made at this time, the toolset, infrastructure, methods and risks of the campaign bear a striking similarity to that of APT10.
Obfuscated Code
The code of the threat that is contained in the corrupted '. DOC' file is heavily obfuscated. The goal of obfuscating the code of the malware is to avoid detection by anti-malware applications, which may be present on the compromised host. If the threat succeeds in staying under the radar of any security tools, the LookBack RAT (Remote Access Trojan) will be executed.
Uses a Proxy Server
LookBack packs RAT-like features but also has other functionality, which is a clear sign that its authors are not amateurs. When LookBack compromises a computer, it will attempt to set up a proxy server used to tunnel malicious traffic. To make the whole operation seem inconspicuous, LookBack's proxy server my imitate the open-source utility WinGup that is used by notable software suites like Notepad++.
A Macro Script Used Before
It appears that the macro script used in the installing of the LookBack RAT was used previously in 2018 in several attacks targeting businesses located in Japan. These attacks were carried out by the APT10. However, this does not mean that they are in any way involved in the spreading of the LookBack RAT, and this may be a pure coincidence.
Capabilities
The LookBack RAT is a rather potent threat with a long list of capabilities such as:
- Taking screenshots of the desktop.
- Restarting or shutting down the system.
- Using the Command Prompt to execute remote commands.
- Listing directories.
- Launching files.
- Modifying/copying/deleting files.
- Controlling the cursor.
- Listing and controlling processes.
- Starting/stopping/browsing Windows Services.
- Removing itself from the host.
Despite the LookBack RAT only being spotted in several campaigns, it is likely that its creators will not stop there as this is a very well-built malware. Make sure you download and install a legitimate anti-virus software suite which will keep your system safe from threats like the LookBack RAT.

