ICS-CERT Reports Majority of 2012 Critical Infrastructure Malware Attacks Were Against the Energy Sector
The Cyber Emergency Response Team for Industrial Control Systems (ICS-CERT) headed up by the Department of Homeland Security, reported that during the 2012 fiscal year they responded to 198 cyber incidents where a large majority of them, about 41%, were targeted on the energy sector.
Cyber intrusion among company networks, online banking institutions and power-grid infrastructures have all been viable targets in the past few years for malicious attacks. It has not been until recently that new sophisticated attacks have set their cross hairs in the direction of the energy sector on such a broad scale.
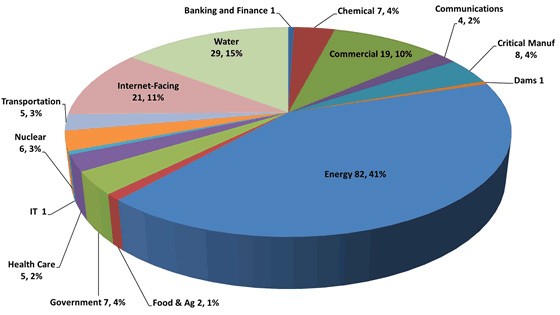
During the recent 2012 fiscal year, the ICS-CERT monitored and recorded data of vulnerability incidents by sectors where the energy sector accounted for 41% followed by other sectors that paled in comparison, such as the water sector with 15% targeted rate and commercial accounting for 10%. The percentage breakdown is demonstrated in the ICS-CERT Monthly Monitor Report for Oct/Nov/Dec 2012 chart in figure 1 below.
Figure 1. ICS-CERT Monthly Incident Response Activity Monitor Report Pie Chart for Oct/Nov/Dec 2012
To correlate the severity of these findings and how vulnerable energy infrastructures are, you must look to one of the two attacks on two US power plants being hit by malware last year. In one of the incidents a determination was made of sophisticated malware existing on two engineering workstations at a power generation facility. An employee prompted the malware discovery after asking company IT staff to inspect his USB drive, one he had routinely used for backing up control systems configurations, after experiencing issues with the drive. A PDF document release from the October through December 2012 ICS-CERT monitor report starts with this explanation going on to concur the following:
"When the IT employee inserted the drive into a computer with up-to-date antivirus software, the antivirus software produced three positive hits. Initial analysis caused particular concern when one sample was linked to known sophisticated malware. Following analysis and at the request of the customer, an onsite team was deployed to their facility where the infection occurred."
Within the October through December 2012 ICS-CERT report, there is additional information and discoveries related to virus infections at electric utility facilities. One could conclude from the report that anyone with malicious intent could locate certain devices within a utility station and attempt logon, leaving the systems vulnerable to a remote attack.
Not only are vulnerable energy infrastructures a target that stands out like a deer in headlights, but they are vulnerable to the point that their 'up-to-date' antivirus software is not sufficient for detecting and preventing attacks by new viruses or sophisticated malware attacks. Research teams, such as those from the University of Tel Aviv, have said that antivirus software may be a waste of money when it comes to new viruses. In their test conducted of 82 new malware files against 40 antivirus products, they found that none of the programs detected the files.
It goes without saying that the energy sector is a ticking time bomb waiting for the right cyber intrusion to light the fuse. If a power plant is under attack by a malware intrusion, the possibilities of a serious pandemic are almost inevitable. Just think, a hacker shuts down a power plant and it could cripple surrounding areas.
We can even look to previous incidents where the Stuxnet worm attack took place under the radar infecting an Iranian nuclear enrichment plant's control systems in addition to 14 other plants mostly in Germany. At the time authorities and security experts were unaware of who conducted the attack and the initial severity. This goes to show that the energy sector deserves to be scrutinized for their security protection efforts even if they 'think' they are well shielded.